- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R80 Inline Layer Issue
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80 Inline Layer Issue
Hi,
I created an inline policy on R80.20. I did it by going through the logs to see which access control rule was used for each app control rule. Then I created layers and pasted all of the app control rules into appropriate layers assigned to each access rule per the action column. I left entire the app control policy in place and pushed this policy out, and everything broke. In the logs, I saw a lot of CP Early Drop. A lot of the logs were the remote users trying to get DNS, but I know that more than only that traffic broke. I restored an old policy to get it back up.
I’m not sure what I did wrong. The CP Early Drop indicates the packets had no way out of the new policy. I was sure to set each layer to implicit allow, and remove the default clean up rule that is added to each layer. One possibility was that it was failing because I didn’t add a specific allow rule at the bottom of each layer. However, I have not been able to replicate that as a problem in my lab. Does anyone have any ideas?
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
do you have a application control blade and firewall inside and enable on this inline layer? and https inspection too?
did you enable drop templates on secureXL?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, Firewall and Applications & URL Filtering are the enabled blades on this and all layers. HTTPS Inspection is not enabled. Drop templates are also not enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How is fail mode configured in advanced settings of application control?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you mean in the layer? In the layer, Implicit CleanUp Action is set to Accept. In the Application Control policy, there is an Any Any Allow rule explicitly at the bottom. I am not aware of a fail mode configuration in advanced settings for the Application Control policy. If there is such a thing, can you point me toward it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What I mean is, I know where this setting is in R77.30 but not R80.20. I would think fail open but don't know where to check.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Menu:
Manage & settings...
Blades...
Application Control & URL filtering...
Advanced Settings...
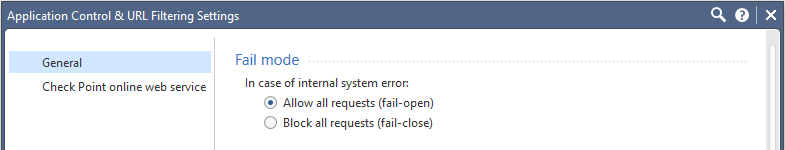
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I may have an answer. I noticed that the Policy layer has both blades Network and Application Control. This is because we wanted to have the Application Control layer as a backup in case something didn't work with the Inline layer. However, I didn't realize until now that in the Network layer (/blade), only Firewall is checked. Not Application Control + URL Filtering. So the packet gets to the old access rule that allowed it out, but since it's not doing Application Control, it can't get out from the Network blade? I will report back once I test.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ok. This logic seems to be reason.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks everyone. Yes this was the problem. It would make a good SK. Below, I have the Application Blade here because I'm not going to remove the Application policy until I know my inline layers are working.
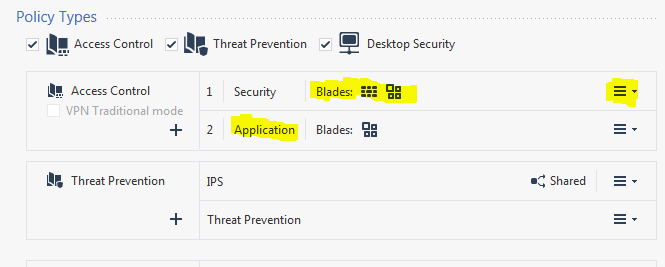
However, I needed to click the menu to the right of the Security Blade in Access Control, and choose Edit Layer. From there I had to enable the Application and URL "Blade" inside the Security "Blade".
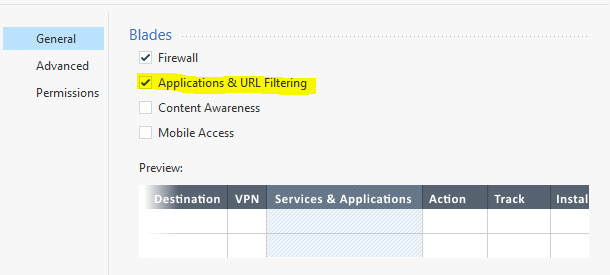
This was a very easy mistake to make and a hard one to fix, and it was a big deal for one customer and would have been a huge deal for the next if I didn't find the check box. Probably the best thing would be for Check Point to not allow you to install policy to a Security Blade with Inline Application Control rules if App & URL Filtering aren't checked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes Correct. If App & URL filtering is not checked then it should give warning message when we create rule for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ronen Zel think it's a good idea to turn into an SK.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you have an Explicit "any any allow" rule at the bottom of your App Control rulebase and/or the Implicit Cleanup rule for the layer is set to Accept, it should get through.
Am curious if the "early drop" is happening in the first layer instead (which adding App Control to won't necessarily solve).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, it was happening in the first layer. It showed the blade as Security Inline Policy, and then CP Early Drop. I think the packet hit the Security Rule with the Inline layer, but then couldn't get out on the Inline (App Control) rule because that blade wasn't on in the Security Blade, so the packet had no way out of Security.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Inline layer.

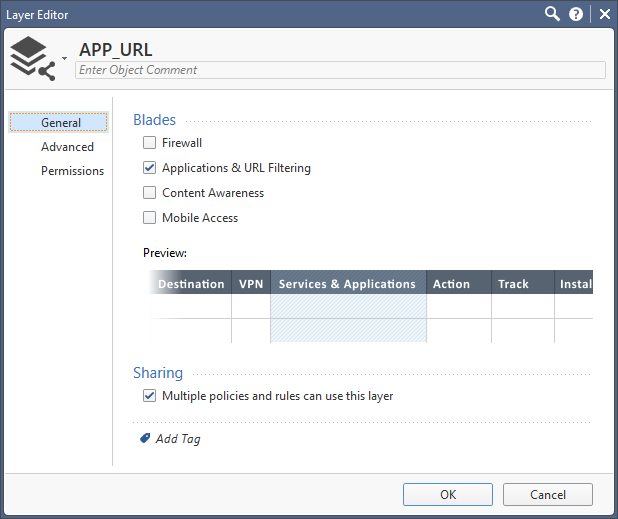
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 27 | |
| 18 | |
| 10 | |
| 9 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |
Upcoming Events
Mon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANMon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


