- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Policy Insights and Policy Auditor in Action
19 November @ 5pm CET / 11am ET
Access Control and Threat Prevention Best Practices
Watch HereOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R80.20 - SYN Defender on SecureXL Level
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.20 - SYN Defender on SecureXL Level
I think the new feature "Accelerated SYN Defender" is a good choice to effectively prevent "SYN Flood Attack" on Check Point Gateways with enabled SecureXL.
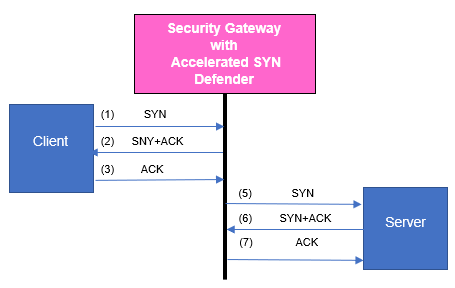
A TCP SYN Flood attack occurs when a host, typically with a forged IP address, sends a flood of TCP [SYN] packets. Each of these TCP [SYN] packets is handled as a connection request, which causes the server to create a half-open (unestablished) TCP connection. This occurs because the server sends a TCP [SYN+ACK] packet, and waits for a response TCP packet that does not arrive. These half-open TCP connections eventually exceed the maximum available TCP connections that causes a denial of service condition. The Check Point Accelerated SYN Defender protects the Security Gateway by preventing excessive TCP connections from being created. The Accelerated SYN Defender uses TCP [SYN] Cookies (particular choices of initial TCP sequence numbers) when under a suspected TCP SYN Flood attack. Using TCP [SYN] Cookies can reduce the load on Security Gateway and on computers behind the Security Gateway. The Accelerated SYN Defender acts as proxy for TCP connections and adjusts TCP {SEQ} and TCP {ACK} values in TCP packets.
You can find more in the manual under:
- fwaccel synatk
- fwaccel6 synatk
Regards,
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
This feature is supported by R80.20 SP in a 64000 Appliance?
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, Supported using “g_fwaccel synatk” command.
Note that it is supported via Gateway CLI only and not via Smart Console
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am wondering if someone may clarify for me about the “Syn Attack protection” and the “Accesslerated SYN Defender (i.e. fwaccel synatk).
Are they the same thing, or they are two different things?
I feel the "Syn Attack protection" was the legacy configuration from the Syn Defender in R65, whereas this "Accesslerated SYN Defender" is a new(?) generation of the Syn Defender?
Am I correct? Please educate me if I misunderstand these two terms.
Anyway, I hope I can understand these terms better, and start to configure one or both of them according to some kind "best practice" suggestion from Check Point.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Raymondn , in a nutshell, the idea of Syn Defender is still the same. It is just with R80.20, it can be moved from FW into SXL. If so, it is called "Accelerated Syn Defender". THis functionality did not exist in the previous releases.
More information can be found here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
and here (under "Accelerated Syn Defender" chapter"): https://sc1.checkpoint.com/documents/R80.20_GA/WebAdminGuides/EN/CP_R80.20_PerformanceTuning_AdminGu...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the info.
Spent sometime reading some of those and now I have a better understanding.
If I read SK correctly, in the end of the sk it did leave a statement where keeping this Syn Attack protection feature 'disable' until you are facing a DOS attack, may be a wise choice.
How do people feel about this? Is this a feature people typically disable, or leave it as "monitor only", and only set to enforcement when facing DOS issue?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would agree with the recommendation in the SK and leave SYN Defender off unless you need it. In R80.10 and earlier, enabling SYN Defender would kill SecureXL acceleration of most traffic traversing the firewall and make it go F2F, which could cause its own performance problems if the firewall was already under high load. This is why the Inspection Setting "SYN Attack" still shows a Performance Impact rating of "Critical". Now that SecureXL itself can perform this protection in R80.20+ turning it on is not likely to cause other performance problems.
Setting an email/SNMP alert for the Aggressive Aging signature could be one way to get alerted that you might need to turn on SYN Attack.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello. I wonder the reasoning for only turning this protection on when the issue occurs? Is it possible this idea is left over from when it was not available via SecureXL and therefore caused a critical performance hit? My customer has a requirement to have DDOS protection on and doesn't prefer to have it work via an alert and then a manual change. I told them it's not recommended, but I'd like to know the reasoning, as they may have to find another solution if this is the case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Although this SYN protection can now be handled inside SecureXL/sim, it still causes some overhead at the start of every TCP connection. If the new connection rate through your firewall is high this overhead can really add up. What I would suggest is making sure the Aggressive Aging Inspection Setting is enabled, and configuring alerting for it. When the alert fires due to excessive memory consumption for tracking connections, you can assess the situation and enable SYN Defender if appropriate. Aggressive Aging is always a great "canary in the coal mine" to let you know that something unusual is happening.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you. I'm sure this is correct, but now I need to figure out how to setup alerts for Aggressive Aging. In sk25941 when describing how to setup internal_sendmail, there is a note that says:
- Mail Alerts may not work even after configuring as per this sk. To receive mail alert you need to have an SMTP server configured with "Mail Relay" and "No Authentication".
I'm guessing this customer does not have their SMTP server setup with mail relay and no authentication, and I don't want to ask them to do that. There is another post here that says I need to write a script to get this to work. Do you have any other thoughts on how I can get alerts working for Aggressive Aging? Sorry I'm asking a new question here, but hoping I'm missing a more realistic way to do this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The customer just needs to allow emails from the IP address of the SMS to be relayed by their SMTP server, which would normally be denied by default. They don't have to allow mail relay for all IP addresses. They also need to allow unauthenticated emails from that single IP address. The setup for the mails will be on the Global Properties "Alert" screen, and then set the Aggressive Aging Inspection Track setting to Mail.
I don't see the ability to fire a mail-based Automatic Reaction from SmartEvent when Aggressive Aging kicks in but it might be possible to create a new Event type that could do so.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a couple of questions about setting up an SNMP trap for Aggressive Aging. One is, AA turns on when the connections table or memory hits X%, 80% by default. This made sense to me when the connections table used to have a finite limit. Now that the connections table is dynamically set, how does it calculate when it hits 80%?
Another question is, is there a good way to generate an Aggressive Aging SNMP trap? My thought is if I understand how the 80% connection table works, then I could open a change window where I artificially drop the connection % to generate some traps, and turn on Aggressive Aging. My monitoring guy says he wants to get a trap from this protection so he can use it to build a template to create a ticket when we receive this drop. Thank you as always.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is answered in sk122154: How is Aggressive Aging enforced when Concurrent Connections Capacity Limit is calculated ...
When the connections table sizing is set to "Automatically", if the overall memory utilization of the gateway exceeds the specified threshold percentage, Aggressive Aging will start up and send an SNMP trap if so configured. So for example if a system has 16GB of RAM and you run free -m, with the default 80% setting the amount of "used" memory would need to exceed ~12.8GB which would correlate to "available" reporting approximately ~3.2GB. All other values reported by this command such as "free", "shared", and "buff/cache" are irrelevant to this calculation for Aggressive Aging and should be ignored, especially "free" which does not mean what most people think it means.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any chance the behavior of Syn Defender has changed in R82 where CP recommends to leave it on?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not seen any such recommendation myself.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 42 | |
| 21 | |
| 10 | |
| 8 | |
| 7 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Wed 19 Nov 2025 @ 11:00 AM (EST)
TechTalk: Improve Your Security Posture with Threat Prevention and Policy InsightsThu 20 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERThu 20 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchWed 19 Nov 2025 @ 11:00 AM (EST)
TechTalk: Improve Your Security Posture with Threat Prevention and Policy InsightsThu 20 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERThu 20 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


