- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: New updatable object for HTTPS Inspection: HTT...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
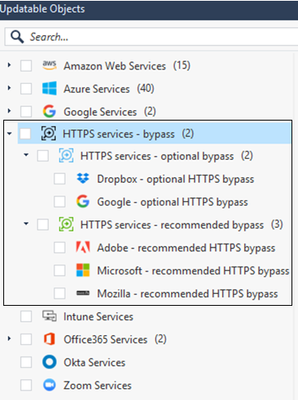
New updatable object for HTTPS Inspection: HTTPS Services Bypass
We are glad to share a new usability enhancement for our HTTPS Inspection customers.
Starting from R80.40, HTTPS Inspection customers will be able to consolidate their certificate pinned apps rules using managed updatable objects.
We've collected a list of HTTPS services which are known to be used in scenarios where HTTPS Inspection is unable to establish the trust between the client and the Security Gateway and is therefore unable to inspect the traffic.
These HTTPS services are part of "HTTPS services - bypass" updatable object.
You can choose to add this object to HTTPS Inspection policy as a bypass rule to avoid connectivity issues and/or to the Access policy as a drop rule to block these services explicitly.
For further information please refer to sk163595
If you'd like to see some additional services added to this, let us know!
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Check Point!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please tell me what is the difference between HTTPS Whitelisting and HTTPS Services Bypass ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The HTTPS Inspection policy determines what traffic is "man in the middled" so you can see and make security decisions on the unencrypted contents.
The actions for the rules in that rulebase are either "Inspect" or "Bypass."
Not sure where whitelisting enters into the discussion.
The actions for the rules in that rulebase are either "Inspect" or "Bypass."
Not sure where whitelisting enters into the discussion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You create a custom application with the domain(s) you wish to bypass and add a rule for that domain in the HTTPS Inspection policy.
The "whitelist" that document refers to is one we maintain and cannot be updated by you.
The "whitelist" that document refers to is one we maintain and cannot be updated by you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for insight. Are there plans to ADD this to R80.30 as part of future JHA jumbo update?
thanks -GA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Use of Updatable Objects in the HTTPS Inspection policy required some major infrastructure improvements.
I don't believe these will be backported to earlier releases.
I don't believe these will be backported to earlier releases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @PhoneBoy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Adding support for updatable objects in R80.30 releases won't be possible, the support for for updatable objects requires the new HTTPS Inspection policy that was embedded to the SmartConsole, and this change is to big and complicated for the jumbo releases.
Adding support for updatable objects in R80.30 releases won't be possible, the support for for updatable objects requires the new HTTPS Inspection policy that was embedded to the SmartConsole, and this change is to big and complicated for the jumbo releases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks for the insight!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a positive update for HTTPS inspection thanks!
Are there any improvements where a client certificate is used? Right now on R80.30 we have to add a bypass rule by IP address in rule position #1 to allow client cert to work. Being able to do this by domain name would be a huge benefit (especially when the application is hosted in AWS/Azure!)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don’t believe any vendor handles TLS Client Auth very well.
Sites that require this must be bypassed.
You can create a custom application definition with the domain in question and use that in the rule—should work in R80.30.
Sites that require this must be bypassed.
You can create a custom application definition with the domain in question and use that in the rule—should work in R80.30.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Has sk66405 been officially "fixed"? I guess it depends on whether the client cert based application supports SNI or not as to whether we can bypass by domain name.
I might have to setup a test server and give it a try.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe so if SNI happens early enough in the negotiation that we can bypass it in this case.
Also, the SK does not mention R80.30, but it's worth double-checking.
Also, the SK does not mention R80.30, but it's worth double-checking.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just curious, what is to fix in sk66405, @Ryan_Ryan. The SK says, client certificates are not supported with HTTPSi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That SK described a special method for bypassing client cert, the requirement was it had to be done by IP address (domain not supported) and it has to be in the first rule in the inspection policy. ie. so putting the IP address in a bypass rule in position #2 will still break the connection. Our real issue was one of the services we used was hosted out of AWS so we had to manually put every AWS IP address into rule number 1 so we have had to bypass a massive chunk of the Internet for the sake of one server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I understand you entirely. In R80.40, it is possible to use FQDN objects in the HTTPSi rulebase. It should resolve your issue.
I have also reached out to the SK owner to clarify why this option is not mentioned in the SK for R80.40. With R80.30 and below, there is no option for domain objects to be used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Ryan_Ryan , I have double-checked with R&D.
You can use FQDN object to represent your asset on AWS in the HTTPSi bypass rule, with R80.40 and up. SK is being modified to reflect that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can try to reference sk165094 (Custom Applications/Sites - Best practice).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Will this eventually include the O365 'Optimize' category from their RSS feed to bypass HTTPS inspection?
Reference article:
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think it is a good idea, but the question should be directed to R&D
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 21 | |
| 8 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Thu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasFri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter