- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: My Top 3 Check Point CLI commands
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My Top 3 Check Point CLI commands
Just had a fun geeky conversation with Dameon Welch Abernathy (AKA Phoneboy) Jony Fischbein , Jeff Schwartz and Michael Poublon (over 100 accumulated years of experience in Check Point products) , on what are our favorite & most useful commands in a Check Point environment.
Below are my 3 , plz add yours in the comments (we will do a poll for the top 5 after getting your feedback ... ).
1) fw ctl zdebug drop
used to quickly see all dropped connections and more importantly the reason (e.g. anti-spoofing, IPS , FW rule , ....)
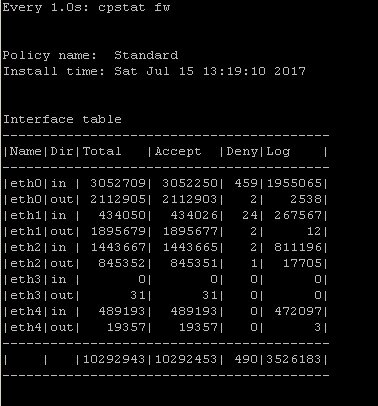
2) cpstat fw
quickly see stats of number of connections (accepted,denied,logged) with a breakdown
if the FW was under a high load i would usually run " watch --interval=1 'cpstat fw' " (would see a real-time to see the interface that is causing this)
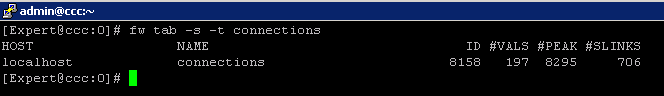
3) fw tab -s -t connections
allowed me to quickly see how much load is (and was i.e "peak" ) on the FW
that's it (i have more , but i want to hear yours ...)
plz add yours in the comments (we will do a poll for the top 5 after getting your feedback ... )
195 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes and no ![]() . Your solutions are perfectly correct, true, but ... don't forget that I called it 'List of Administrator's errors...' not Checkpoint product errors . So technical solutions existed long before R80.10,
. Your solutions are perfectly correct, true, but ... don't forget that I called it 'List of Administrator's errors...' not Checkpoint product errors . So technical solutions existed long before R80.10,
e.g. wrong Policy install ? ... can't be easier than that - just check relevant gateways in "Policy Targets" menu for this policy and this will never happen.
Removing object in use ? Well, just read the warning and click on the button "Where used" .
And while my list is compiled based on R55 - R77.30 versions, after speaking with thousands of IT guys/gals managing firewalls, I can assure you - they will 'outsmart' any technical safety measures put by bright R&D folks at Checkpoint, no one can beat the 8th layer of OSI, doesn't mean you should never try but ...
https://www.linkedin.com/in/yurislobodyanyuk/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yuri Slobodyanyuk wrote:
Yes and no . Your solutions are perfectly correct, true, but ... don't forget that I called it 'List of Administrator's errors...' not Checkpoint product errors . So technical solutions existed long before R80.10,
e.g. wrong Policy install ? ... can't be easier than that - just check relevant gateways in "Policy Targets" menu for this policy and this will never happen.
Removing object in use ? Well, just read the warning and click on the button "Where used" .
And while my list is compiled based on R55 - R77.30 versions, after speaking with thousands of IT guys/gals managing firewalls, I can assure you - they will 'outsmart' any technical safety measures put by bright R&D folks at Checkpoint, no one can beat the 8th layer of OSI, doesn't mean you should never try but ...
I encourage you to try to remove a used object from the objects bar in R80.10. Let me know if you found a way to do that.
In general, at Check Point we try to have our admins do the most by clicking the least. Some errors can be fully prevented with a smart backend platform (R80). Others are user best practices which aren't always a problem and are different between organizations - which I mentioned as stay tuned.
Of course there will always be the market for educational programs and partner sessions in which they help their customers make the most out of their Check Point products. We definitely learn from our partners' experience when shaping the future of our product line.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
About admin errors (not common ones ) there's one story I have to share that took me 24 hours straight to figure out back in the days of February 2004 in one the largest airlines core FW
There was a worm called mydoom that attacked www.sco.com and other IP addresses (https://www.google.com/amp/www.networkworld.com/article/2330164/lan-wan/the-worm-attacks--sco-downed...)
1)The security admin at that company created a rule #2 :any--(group called) bad-ip--http --drop
2)The symptom was downtime of traffic (ping worked ok) , if you reboot the firewall all works great for like 8 minutes and then the same down time of traffic
3)No drops in the logs
4)After troubleshooting with Cisco R&D, check Point R&D no solution found
5)All of the sudden I was hungry and ate a doughnut
6)After the doughnut I drank Diet Coke (to balance the calories )
7)Then I had an epiphany they should invent a doughnut + croissant , this could work (again it was back in 2004 )
8)No sleep
9)I decided to see what's inside the group called bad-ip
10)I see a fuc$!ng domain object of www.sco.com (I.e. The fw tried to reverse DNS every packet )
11)Face palm

12)I deleted it
13)Everything works till today
Lesson of the story : I should have patented cronut
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So what you're saying is domain objects caused traffic to fall into the proverbial cronut hole?
Thankfully, they work much better in R80.10 ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hehe yes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hahaha , hilarious.
Going down the memory lane I can recall in 10+ years at Netvision how at least 4 times clients downed their network by using this Dynamic Object - all major enterprises (and the newest case with R77.30 some 2 years ago). The user-friendliness of the SmartConsole tricked them:
" Hmm, my users are abusing the whole line to the Internet with Youtube/Facebook traffic, CEO is not happy - all is slow, but no license for URL Filtering, let's see...."
"Wait a minute, what this standing so prominently alone in the Smart DashBoard Dynamic Object does ?? Cool, it allows to enter facebook.com and youtube.com in its name and use it in Security Rules !!! Eureka ! Next pay raise is a done deal, I am genius. Let's create it as a 1st rule, source is all LANs (or any) ,destination this Dynamic Object(s), install policy and nirvana is close... Should "You were disconnected from the Management server" happen after that? Oh, here is CEO calling, probably to thank me."
"All is lost! No internet for the whole company, Checkpoint firewall failed, let me call my CSP and yell at them to fix it ASAP"
Me: "What changes were done just before failure?"
Him:"Nothing unusual, was doing some rules"
Me:" Can you connect to the firewall from LAN by ssh?"
Him:"Not really" [then goes short explanation how to disconnect the whole LAN, or run fw unloadlocal]
Me: "Please let it be a Standalone firewall" [I am happy - it is indeed Standalone so w/o Security policy I can connect to it from the Internet"
Me (after deleting this 1st rule and installing policy with CPU load going from 100% to 3%): "Look, this is not a technical failure this is you doing stuff you have no idea about"
Him:"Really? Ok, sorry for that ..."
Me [wishfully]: "I wish Checkpoint hid this stupid Dynamic Object deep inside Guidbedit cave or not created at all, in all these years I needed this object just once but took care of at least 20 cases of its misuse."
PS. I know what book I can write about Checkpoint - "Diaries of the phone boy or stories from the trenches" [if https://community.checkpoint.com/people/dwelccfe6e688-522c-305c-adaa-194bd7a7becc doesn't mind franchising his handle ![]() ]
]
https://www.linkedin.com/in/yurislobodyanyuk/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm assuming above you mean Domain Objects, which definitely has some performance implications and had some bugs.
R80.10 has hopefully solved those issues ![]()
Dynamic Objects are actually pretty useful in the sense they are basically placeholders in the rulebase.
On the local gateway, you can define what IP addresses those objects resolve to.
The DShield block list was implemented as a Dynamic Object.
You can use the dynamic_objects command to modify the contents of a given dynamic object without doing a policy installation.
A few pre-defined ones exist such as LocalMachine and LocalMachine_All_Interfaces.
The performance impact of Dynamic Objects is not nearly as bad as Domain Objects, though in pre-R80.10 releases, it did disable SecureXL templates on any rule that is used (as well as any rules that follow).
In R80.10, this limitation does not apply.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did mean Dynamic Object and rest assured - every time you use it in the Rulebase (especially at the top of the Rulebase) in a busy network your firewall will max out CPU load at 100% (true for all gateways up to and included R77.30 as I've seen it close up personally, not stories from someone and never mind the hardware - 16 Gb 8 cores + CoreXL + SecureXL still went down, haven't tried with R80 so can't comment) :
While problem with Domain object is its reverse DNS resolving , with Dynamic Object it is forward IP resolving for each passing session thanks to https://community.checkpoint.com/people/dwelccfe6e688-522c-305c-adaa-194bd7a7becc for clarification : the real reason for Dynamic Object causing trouble is that when configured only via Dashboard and not via CLI it is left undefined..
Domain Object hasn't been so much of a problem (still happened but rarely) because it is hidden from the eye, so you would not stumble upon it as you do with Dynamic Object.
And of course I know what all these objects were meant to be used for, only that end users find more creative ways to utilize them.
https://www.linkedin.com/in/yurislobodyanyuk/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Use of Dynamic Objects in R77.30 and earlier will disable SecureXL for the first rule it is used and all rules below that one.
If you put a Dynamic Object at the top of your rulebase, that could definitely lead to maxing out the CPU...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon,
are you 100% sure?
I am using dynamic objects with R77.30 and fwaccel stat says that access templates are not disabled by the rules using dynamic objects.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm 100% sure on this.
In fact, there was a bug that I personally experienced around this that was fixed in Take 17 of the R77.30 jumbo: Jumbo Hotfix Accumulator for R77.30 (R77_30_jumbo_hf)
If you're on a recent jumbo and you're still seeing this, I recommend opening a TAC ticket.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dynamic Objects do no DNS lookups, they only use what has been configured in the local gateway via the dynamic_objects command.
If they didn't, then the object is basically undefined, and that could be a problem if it's used in the rulebase.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Second that, it seems your opponent is a bit confused and actually means Domain objects.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are some top notch commands being shared here.
What defines a 'favorite' really depends on the scenario. So i'll go with a couple of what i deem to be 'cool' commands, that you may know now (or may not) but either way probably wished you knew them sooner!:
1 - sed -I s/"text"/"newtext"/ file.name << Find and replace when 'vi-ing' a file.
2 - watch -n 0.5 -d cpstat fw << can use cpstat fw or any other, but the '-d' flag allows fothe autorefresh to highlight the changes. perfect for spotting increments in hit counters, of use with 'df-h' to spot a hardrive filling up during upgrade processes.
3 - du -sk * | sort -n << got a full hardrive? no idea where the large files are? here you go, Merry Xmas!
4 - fw tab -t fwx_alloc -x << not had to use this for a few years now, but having the gateway suddenly dropping connections due to a full NAT table isnt fun. this isnt the cleanest way to clear the table, but possibly the best knee-jerk fix to get an instant relief on the traffic flow.
5 - fw sam -v -s 10.1.1.1 -f ClusterName -t 7200 -J src 8.8.8.8 << the SAM rule. nothing cooler than an instant block of a malicious IP.
thanks all for sharing. some great stuff here.
Pritchard
CCSM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I haven't seen this one yet:
- Activate fw worker stats (per instance!)
echo 1 > /proc/cpkstats/fw_worker_0_stats
- Read fw worker stats
cat /proc/cpkstats/fw_worker_0_stats
Again. Make sure you are aware of the impact that looking at a firewall may have on it's performance.
We could sure use some Heisenberg compensators for this.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My favorite (unsupported) command:
vsx_util downgrade😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually, not so much unsupported as undocumented. "vsx_util upgrade" option allows you to downgrade VSX cluster version too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gateway
fw1> show route destination 10.1.1.1
Codes: C - Connected, S - Static, R - RIP, B - BGP (D - Default),
O - OSPF IntraArea (IA - InterArea, E - External, N - NSSA)
A - Aggregate, K - Kernel Remnant, H - Hidden, P - Suppressed,
U - Unreachable, i - Inactive
S 10.0.0.0/8 via x.18.47.36, eth2-08, cost 0, age 328677
Really helps figuring out which route is going to which interface to run tcpdump on
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
installed_jumbo_take
cpwd_admin list
chsh -s /bin/bash admin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In latest R80.10 we don't have installed_jumbo_take command.
It was integrated in cpinfo:
[Expert@R80-10-MGMT:0]# cpinfo -y all
This is Check Point CPinfo Build 914000176 for GAIA
[IDA]
HOTFIX_R80_10
[CPFC]
HOTFIX_R80_10
HOTFIX_R80_10_JUMBO_HF Take: 24
[FW1]
HOTFIX_R80_10
HOTFIX_R80_10_JUMBO_HF Take: 24
Alex
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The question posed has no reference to R80, R77, R65, etc...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exactly, as there are a mix of versions that people use.
I was personally hoping for some oldies but goodies as well.
Remember fw putkey? ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
still using it ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ouch. That was another fine mess you could get into. Untill you understoord exactly the various connections and how the gateway object is defined it could lead to a lot of weird connectivity issues.
It still is usefull to uderstand it as some other problems have the same root cause. Multihomes hosts are ..... a challenge.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
General question is not, but my comment is for specific version. It will help to understand were it was deprecated and what to use instead of it.
This community will be in internet cache for a long time and maybe for someone running R100 it will be good to know that starting from version X they need to use different command to find installed jumbo take ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R65 old school:-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My command :
watch cphaprob stat
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
compare tables of two Clusternodes from Management Server
[Expert@management:0]# fw tab -t connections -s gateway1 gateway2
HOST NAME ID #VALS #PEAK #SLINKS
gateway1 connections 8158 53 1620 69
gateway2 connections 8158 52 1610 52
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I love the commands listed here!
Already mentioned several times (some of them are utilities instead of really commands):
- cpview -t (to view the history minute by minute, previously enabled with "cpview history on").
- fw monitor (classic, a basic and very powerful utility to diagnose traffic passing through the Gateway).
- fw ctl zdebug drop
Special mention to:
- fw unloadlocal
- fwaccel stat
- fwaccel stats -s
- cphaprob state
- fw ctl multik stat -l -v -r
- fw ctl affinity -l
- cpwd_admin list
Cheers!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw debug fwd on TDERROR_ALL_ALL=5
- Adds detailed debug to gateway's main user mode process fwd (firewall daemon). Debug can be found in fwd.elg
- I'm using it for example if a child of fwd doesn't start.
- You can debug any user mode process (a child of fwd) by replacing fwd with that process name.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 11 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Fri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter