- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: My Top 3 Check Point CLI commands
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My Top 3 Check Point CLI commands
Just had a fun geeky conversation with Dameon Welch Abernathy (AKA Phoneboy) Jony Fischbein , Jeff Schwartz and Michael Poublon (over 100 accumulated years of experience in Check Point products) , on what are our favorite & most useful commands in a Check Point environment.
Below are my 3 , plz add yours in the comments (we will do a poll for the top 5 after getting your feedback ... ).
1) fw ctl zdebug drop
used to quickly see all dropped connections and more importantly the reason (e.g. anti-spoofing, IPS , FW rule , ....)
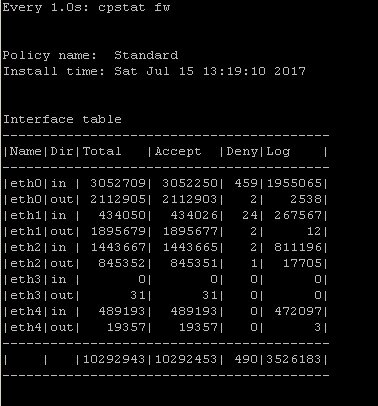
2) cpstat fw
quickly see stats of number of connections (accepted,denied,logged) with a breakdown
if the FW was under a high load i would usually run " watch --interval=1 'cpstat fw' " (would see a real-time to see the interface that is causing this)
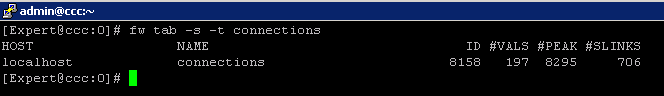
3) fw tab -s -t connections
allowed me to quickly see how much load is (and was i.e "peak" ) on the FW
that's it (i have more , but i want to hear yours ...)
plz add yours in the comments (we will do a poll for the top 5 after getting your feedback ... )
195 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My favorites for security gateways:
cphaprob stat to see the status of high availability
clusterXL_admin up/down to force the cluster node into a particular state (good for forcing failover in a healthy cluster so I can do work on a node)
vpn tu to see IKE/IPSEC security associations, and remove expired ones from gateways that burped
Some of my other favorites that I don't see listed here already are:
enabled_blades to list the blades that are enabled for the gateway by the management server (run in expert mode)
installed_jumbo_take to see what JHFA you have installed (does not work on the base R77.30 install, you have to have a JHFA installed and run in expert mode).
cphaconf cluster_id get Useful to see what the cluster magic id is if you have an id that's different from the default.
ips stat See if IPS is enabled, and what profile its running. When troubleshooting connectivity issues, ips on/off is useful too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw sam -v -l long_noalert -J any 123.234.111.222
installed_jumbo_take
mdsstop_customer 192.168.2.1;mdsstart_customer 192.168.2.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1) Clear ARP cache via CLI
In case you need to clear 1 arp entry the following command can be used:
arp -d [ip address]
In case the complete arp cache needs to be cleared the following single line script can be used:
for i in `awk -F ' ' '{ if ( $1 ~ /[0-9{1,3}].[0-9{1,3}].[0-9{1,3}].[0-9{1,3}]/ ) print $1 }' /proc/net/arp` ; do arp -d $i ; done
2) Flash Network Interface LED
To flash/blink a LED on an interface in order to physically identify the interface in question on a machine.
*Note this does not work on all type of interface cards.
ethtool -p <interface_name>
3) Analyze network traffic via CLI
A script created by a former CP employee, as alternative for SmartView Monitor, cpview or tcpdump you can use the following script in order to analyze traffic patterns. * Note there are some caveats to keep in mind.
http://expert-mode.blogspot.nl/2013/05/checkpoint-top-talkers-script-display.html
https://raw.githubusercontent.com/craigdods/scripts/master/top_talkers.sh
Security Solutions Expert for Global Strategic Partners GSI/MSP/Telco & Consultancy Firms
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A bit shorter to type version of clear arp: for ip in $(awk '/([[:digit:]]\.)+/ {print $1}' /proc/net/arp) ; do arp -d $ip ; done
Or even shorter way to do so per interface:
ip neighbor flush dev eth3
https://www.linkedin.com/in/yurislobodyanyuk/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've got one more to add to this: cplic print -p
This will show you not only the license you have installed but what features your license breaks down to.
I'm curious how many old-timers remember what sr5000 refers to? ![]()
[Expert@oscar:0]# cplic print -p
Host Expiration Primitive-Features
xx.xx.xx.x 22Aug2017 ::CK-xxxxxxxxxxxx fw1:6.0:swb fw1:6.0:ctnt fw1:6.0:swb fw1:6.0:abot fw1:6.0:swb fw1:6.0:appi fw1:6.0:swb fw1:6.0:aspm fw1:6.0:av1000 fw1:6.0:swb fw1:6.0:urlf fw1:6.0:av1000 fw1:6.0:swb fw1:6.0:av fw1:6.0:av1000 fw1:6.0:swb fw1:6.0:ips fw1:6.0:swb fw1:6.0:vsx5 fw1:6.0:vsx5 fw1:6.0:vsx5 fw1:6.0:vsx5 fw1:6.0:vsx5 fw1:6.0:swb fw1:6.0:cluster-1 fw1:6.0:cpls fw1:6.0:cluster-u fw1:6.0:mpu fw1:6.0:sxl_vpn fw1:6.0:sxl_fw fw1:6.0:sxl_ppk fw1:6.0:swb fw1:6.0:connect fw1:6.0:pam etm:6.0:fgcountunl etm:6.0:fg etm:6.0:tclog etm:6.0:fgvpn fw1:6.0:swb fw1:6.0:identity fw1:6.0:swb cvpn:6.0:ccvunl cvpn:6.0:cvpnunlimited fw1:6.0:des fw1:6.0:strong fw1:6.0:encryption cvpn:6.0:cvpn fw1:6.0:swb fw1:6.0:dlp fw1:6.0:swb evnt:6.0:smrt_evnt fw1:6.0:ipsa fw1:6.0:swb fw1:6.0:spcps fw1:6.0:pam fw1:6.0:enchostsunlimit fw1:6.0:encryption fw1:6.0:aes fw1:6.0:strong fw1:6.0:rdp fw1:6.0:des fw1:6.0:isakmp fw1:6.0:swb fw1:6.0:xlate fw1:6.0:auth fw1:6.0:content fw1:6.0:sync fw1:6.0:fm fw1:6.0:blades fw1:6.0:sxl_vpn fw1:6.0:sxl_fw fw1:6.0:sr5000 fw1:6.0:hostsunlimit fw1:6.0:sxl_vpn fw1:6.0:sxl_fw fw1:6.0:sync fw1:6.0:fm fw1:6.0:mc_all_8 fw1:6.0:multicore
Contract Coverage:
# ID Expiration SKU
===+===========+============+====================
1 | PSE6H1R | 20Sep2017 | CPSB-TEX-EVAL
+-----------+------------+--------------------
|Covers: CPSG-C-8-U CPSB-FW CPSB-VPN CPSB-IPSA CPSB-DLP CPSB-SSLVPN-U CPSB-IA CPSB-ADNC CPSG-VSX-25S CPSB-SWB CPSB-IPS CPSB-AV CPSB-URLF CPSB-ASPM CPSB-APCL CPSB-ABOT CPSB-CTNT CK-xxxxxxxxxxxx
===+===========+============+====================
2 | F7PG258 | 20Sep2017 | CPSB-TE-EVAL
+-----------+------------+--------------------
|Covers: CPSG-C-8-U CPSB-FW CPSB-VPN CPSB-IPSA CPSB-DLP CPSB-SSLVPN-U CPSB-IA CPSB-ADNC CPSG-VSX-25S CPSB-SWB CPSB-IPS CPSB-AV CPSB-URLF CPSB-ASPM CPSB-APCL CPSB-ABOT CPSB-CTNT CK-xxxxxxxxxxxx
===+===========+============+====================
3 | G177T42 | 20Sep2017 | CPSB-CTNT-EVAL
+-----------+------------+--------------------
|Covers: CPSG-C-8-U CPSB-FW CPSB-VPN CPSB-IPSA CPSB-DLP CPSB-SSLVPN-U CPSB-IA CPSB-ADNC CPSG-VSX-25S CPSB-SWB CPSB-IPS CPSB-AV CPSB-URLF CPSB-ASPM CPSB-APCL CPSB-ABOT CPSB-CTNT CK-xxxxxxxxxxxx
===+===========+============+====================
4 | D31EF56 | 20Sep2017 | CPSB-IPS-EVAL
+-----------+------------+--------------------
|Covers: CPSG-C-8-U CPSB-FW CPSB-VPN CPSB-IPSA CPSB-DLP CPSB-SSLVPN-U CPSB-IA CPSB-ADNC CPSG-VSX-25S CPSB-SWB CPSB-IPS CPSB-AV CPSB-URLF CPSB-ASPM CPSB-APCL CPSB-ABOT CPSB-CTNT CK-xxxxxxxxxxxx
===+===========+============+====================
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Securemote 5000 I guess 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice one ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1) Analyze top talkers via CLI using "fw tab"
As an alternative for SmartView Monitor, cpview, you can use the below script in order to analyze the top 10 source and destinations on a Security Gateway.
Top 10 Source Connections:
fw tab -t connections -u -f | awk -F';' '/Rule/ {source[$3] } ; END { for (name in source) print source[name], name }' | sort -nr | head -10
Top 10 Destination Connections:
fw tab -t connections -u -f | awk -F';' '/Rule/ {dest[$5] } ; END { for (name in dest) print dest[name], name }' | sort -nr | head -10
2) Monitoring concurrent connections via CLI and redirecting output to a file
There are various ways to monitor concurrent connections. You can use the following command in case you need to monitor this and store the output into a file for further analyzes.
The commands are derived from: fw tab -t connections –s and fw ctl pstat | grep Concurrent
The output will be stored in a file named e.g. “connections”.
while [ 1 ];do uptime | awk '{ split($1,DATE," "); printf "%s,", DATE[1]}' >>connections ; fw ctl pstat | grep Concurrent >>connections ;sleep 0.5;done
or
while [ 1 ];do uptime | awk '{ split($1,DATE," "); printf "%s,", DATE[1]}' >>connections ; fw tab -t connections -s | awk '{ i=i+1;split($4,VALS," "); if (i==2) print VALS[1] }' >>connections ;sleep 0.5;done
3) Clearing Connection Tables
The below command clears the entire connection table on a Security Gateway.
[Expert@FW-1:0]# fw tab -t connections -x
This will clear all the entries in table connections !!!
Are you sure (yes/no)? [n]
+ 4) List all cronjob tasks
The below script will allow you to quick list all cronjob tasks configured on a device for all accounts.
[Expert@FW-1:0]# more cron.sh
#!/bin/bash
#List all cron jobs for all users
for user in `cat /etc/passwd | cut -d":" -f1`;
do
crontab -l -u $user;
done
Security Solutions Expert for Global Strategic Partners GSI/MSP/Telco & Consultancy Firms
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all!
Most of my favourite commands were already mentioned, to add something else to the mix:
Check routes (even if they are not active)
dbget -rv routed (Add | grep if needed)
I remember a strange case where certain routes didn't work, when using ip route, route, netstat we couldn't see thos routes because they were not active.
This command helped me to confirm that the routes were properly configured in the gateway and together with tcpdump and fw monitor the customer was convinced that the issues were in their side 🙂
Example
Interface associated with static route 3 is down
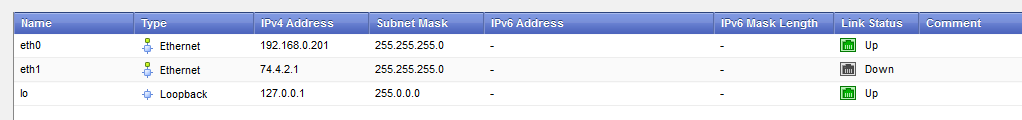
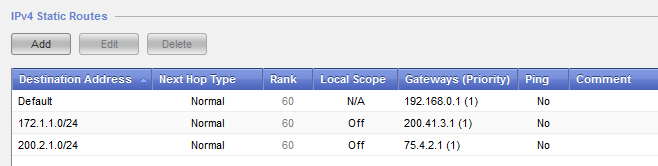
[Expert@BTMOB03:0]# ip route
192.168.0.0/24 dev eth0 proto kernel scope link src 192.168.0.201
default via 192.168.0.1 dev eth0 proto routed
No route even if its on the WebUI
[Expert@BTMOB03:0]# dbget -rv routed | grep 200.2.1
routed:instance:default:static:network:200.2.1.0 t
routed:instance:default:static:network:200.2.1.0:masklen:24 t
routed:instance:default:static:network:200.2.1.0:masklen:24:gateway t
routed:instance:default:static:network:200.2.1.0:masklen:24:gateway:address:75.4.2.1 t
Here we can see that its properly configured
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Or you could run "show configuration static-route" from clish mode to see what all routes are configured ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1) fw ctl zdebug drop | grep 8.8.8.8
2) ping -S src_addr dst_addr
3) ip route get 8.8.8.8 (or) Show route destination 8.8.8.8
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would add ping -I interface dst_addr or ping -I src_addr dst_addr. Found this real useful to send traffic from CMAs to destinations. Basically we now have Cisco extended ping capability in expert mode. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Umm difficult thing to just name 3 ... mine i think would be
fw monitor
mdsstat
cphaprob state
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
WOW, what an amazing engagment and useful crwodsourcing
So who's volunteering to do a "cheat sheet" out of this ? https://community.checkpoint.com/people/dwelccfe6e688-522c-305c-adaa-194bd7a7becc ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There's a document to be made from this list...as well as a poll.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I like cprid_util command to remotely execute command on a gateway:
cprid_util -server x.x.x.x -verbose rexec -rcmd "arp"
I'm using it on my hosts discovery/creation script available here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1)
CPMonitor tool (sk103212) - useful traffic analysis
2)
fw stat -l
HOST IF POLICY DATE TOTAL REJECT DROP ACCEPT LOG
localhost >Mgmt Standard 3Aug2017 6:04:09 394282 0 0 394282 0
localhost <Mgmt Standard 3Aug2017 6:04:09 583248 0 683 582565 519
3)
fw ctl set int print_conns_states 1 (output to dmesg or to kernel debug out-file is defined)
4)
cpstat fw, cpstat mg -f indexer
5)
sar -n DEV
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thx
Can u explain what 4,5 does ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mostly statistics per interface. Cannot figure -mg part though. a typo?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"mg" stands for management server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My 2 cents/agorot:
- df -h I always start SmartCenter (old habits die slow) Management Server debug with it. Especially back with the first line of UTMs 130/270/etc with their small root partition sizes, some 30% of SC 'failures' were caused by not enough disk space (Can't install policy / logs are empty/can't connect to the SmartCenter make sure it is running ...)
- cpwd_admin stop -name FWM -path "$FWDIR/bin/fw" -command " fw kill fwm" Followed by
cpwd_admin start -name FWM -path "$FWDIR/bin/fwm" -command "fwm"
You can't imagine how many downtime I prevented by teaching people to restart SmartCenter this way and not via reboot in Standalone installations. - lvresize -L 20GB vg_splat/lv_current
resize2fs /dev/mapper/vg_splat-lv_current
Again, harking back to the 1st series of UTMs, it became a lifesaver when root partition run out of space and you deleted all you could - SmartConsole.exe etc and the last solution left was to resize root partition. I did it quite a number of times remotely and no glitches . Big thanks to Tobias Lachmann for this command and courage to try it on a live system first.
. Big thanks to Tobias Lachmann for this command and courage to try it on a live system first. - awk -F\; ' {match($0,/{([[:print:]]+)}/,rules);rule_count[rules[1]]++} END {for (rule_number in rule_count) print " Rule number: " rule_number " Hits: " rule_count[rule_number]}' ./fw.log.txt | sort -n -k5
Rule number: FE40E076-BAEB-4979-8E41-5EF1333315e6 Hits: 440101 Rule number: BB3F6772-4D38-4D5A-952A-301333315de8 Hits: 1354341 Running time for a file of 900 Mb with 4.7 million records real 5m50.287s user 4m22.890s sys 0m3.190s
No, not my favorite command (while still valid after exporting logs via fw log) , but had to show you what a pain in the neck was to get Rule Hit statistics before they were introduced to the SmartConsole. - fw ctl zdebug drop While may be not the best as Valeri Loukine mentioned and not the prettiest, but who said life is pretty? So definitely most used in real life to quickly asses the reason of drops.
- fw monitor Last but not least, my real favorite of all versions and times (Hey, search Google for "fw monitor reference" and my blog post from 2009 comes before Checkpoint SK !
 ) . You can't debug traffic issues without it, if it wasn't fw monitor - I wouldn't be such a fan of the Checkpoint firewalls.
) . You can't debug traffic issues without it, if it wasn't fw monitor - I wouldn't be such a fan of the Checkpoint firewalls.
NB. Moti Sagey I guess the logical follow up would be - List Top Checkpoint Administrators' Errors You Have Seen ?
I actually wrote once an article on Most Frequent Errors by Checkpoint Administrators (in Hebrew but easy to translate) which could be a start:
http://www.digitalwhisper.co.il/files/Zines/0x4C/DW76-1-Firewall.pdf
https://www.linkedin.com/in/yurislobodyanyuk/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The primary reason I had a chapter on INSPECT in my books was for fw monitor.
I, of course, also had an FAQ on it back in the day, which you can read here: https://phoneboy.com/fw1/faq/0410.html
Just to clarify your suggestion, are you talking about configuration errors that Check Point admins commonly make?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yep, I remember, I had it as well but can't find anymore, probably someone 'borrowed' .I still have the follow up 
book by Barry (R.I.P.) .
Pity no one dares to write a book anymore (correction: How could I forget that Tim Hall did write a book about Checkpoint...).
Yes, that is what I meant. In the article I linked to I give my list with the real life examples of (working 10 years for CSP provided me with lots of examples of 'not smart things people do with firewalls'):
- Removing object that is being used in Security Rules, ignoring the warning
- Using Dynamic Object as URL filter to block access to some website(s)
- Not checking available disk space before doing any debug
- Using easy to brute-force OS/ssh passwords (especially given the capability of changing default admin OS username during install appearing and disappearing intermittently, depending on the version of the firewall)
- Forgetting to disable SecureXL before doing debug
- Not using so easy to use Database Revision Control as 'insurance' against disaster
- Installing the wrong Security Policy on the wrong firewall (usually ending up in black-out/downtime)
- Using Reject instead of Drop in Security Rules
- Restarting the whole Standalone firewall when needed to restart only the SmartCenter
- Not using NTP for clock synchronization (and as a consequence lessened value or complete uselessness of logs)
- Not verifying saved back ups
https://www.linkedin.com/in/yurislobodyanyuk/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In regard to your statement "Pity no one dares to write a book anymore" I can be the first to tell you that writing a book is hard. Your picture though did remind me of some old Check Point books I bought while writing Max Power for pennies on the dollar because they were so outdated. I wasn't looking for content really, just wanted to see how concepts were presented and what content structures worked and which didn't. Dameon's book was by far the most helpful in that regard, and part of the reason I asked him to write the foreword for Max Power. I have attached a picture of all those old Check Point books I was able to find and buy for research purposes:

--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First - my bad, I corrected my post about no one writing books anymore ![]() .
.
Second,I dug a bit about technical book writing and indeed the picture in general is not rosy (as taken from the Internet):
- For a technical book 30000-35000 sold copies is considered a sound success (we are talking about general technical writing - not insanely priced franchises for Universities / exclusive access to technology books a la C# 8 preview)
- Most books never reach such sales
- As a consequence of above the simplistic ROI calculation doesn't justify writing books for money ( a year/two work on a book), as professional hire-for-money employment will bring much more money
- Main driving reasons for writing a book are establishing the author's expert status / generating consulting| training work / possible public speaking engagements
- Prolonged editing/traditional publishing process makes fast changing technology books outdated before the release
- In many publishing houses the author is supposed to do the bulk of promotion by her/himself
- My personal observation: some previously published authors of technical books re-purpose their work into video/streaming courses, online training labs.
https://www.linkedin.com/in/yurislobodyanyuk/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All the above is quite accurate. Another dirty little secret is that by signing on with a publisher, you'll MAYBE get 10-15% in royalties and that is only after any cash advance has been extinguished. Also that publisher can re-use elements from your work for practically nothing, and also owns a stake on any of the author's future works on that topic.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds fun 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yep, that's why Max Power was self-published through CreateSpace and Amazon. 🙂 I did get approached by a "real" publisher after the book was released. Reading their proposed contract was quite the eye-opener, but at least I got to find out about all these onerous details the easy way (by just reading about them) and not the hard way.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Two comments on writing a book:
1. It's a lot of work (first one took me two years).
2. Keeping it up to date is also a constant challenge, especially today, as things evolve at a much more rapid pace than they did in the early 2000s.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yuri Slobodyanyuk wrote:
Yes, that is what I meant. In the article I linked to I give my list with the real life examples of (working 10 years for CSP provided me with lots of examples of 'not smart things people do with firewalls'):
- Using Dynamic Object as URL filter to block access to some website(s)
- Using easy to brute-force OS/ssh passwords (especially given the capability of changing default admin OS username during install appearing and disappearing intermittently, depending on the version of the firewall)
- Using Reject instead of Drop in Security Rules
- Not using NTP for clock synchronization (and as a consequence lessened value or complete uselessness of logs)
- Not verifying saved back ups
stay tuned
Yuri Slobodyanyuk wrote:
- Removing object that is being used in Security Rules, ignoring the warning
- Not using so easy to use Database Revision Control as 'insurance' against disaster
With R80.10 automatic revisions and session live validations (even when going command-line), these things can no longer happen.
Yuri Slobodyanyuk wrote:
- Installing the wrong Security Policy on the wrong firewall (usually ending up in black-out/downtime)
Tip: Open SmartConsole.exe.config and change <add key="OverridePolicyWarningEnable" value="false"/> from false to true ![]()
Am I diverging?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 22 | |
| 12 | |
| 9 | |
| 9 | |
| 9 | |
| 8 | |
| 8 | |
| 7 | |
| 7 |
Trending Discussions
Upcoming Events
Thu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter