- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: HI All,Any one can guide ?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI All,Any one can guide ?
[Expert@CTSG3Firewall]# tcpdump -nni any host 172.20.106.234
tcpdump: WARNING: any: That device doesn't support promiscuous mode
(Promiscuous mode not supported on the "any" device)
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
19:17:40.710318 IP 10.25.153.3.49522 > 172.20.106.234.443: Flags [S], seq 2707150385, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
19:17:43.716807 IP 10.25.153.3.49522 > 172.20.106.234.443: Flags [S], seq 2707150385, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
19:17:49.722827 IP 10.25.153.3.49522 > 172.20.106.234.443: Flags [S], seq 2707150385, win 8192, options [mss 1460,nop,nop,sackOK], length 0
19:18:00.721660 IP 10.25.153.3.49523 > 172.20.106.234.443: Flags [S], seq 2812651852, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
19:18:03.731702 IP 10.25.153.3.49523 > 172.20.106.234.443: Flags [S], seq 2812651852, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
19:18:09.737746 IP 10.25.153.3.49523 > 172.20.106.234.443: Flags
Not receiving return traffic ,while bypass firewall able connect VPN client ,through firewall can not see return traffic ..
using firewall model Checkpoint 750 small Business.
Any one can guide on further troubleshooting ideas....
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please be more specific:
What kind of VPN? IPSec or SSL?
VPN from where to where?
When you are bypassing firewall, are you unloading the policy or are physically bypassing it?
If second, what IP is assigned to the client and by which device?
Describe the topology of your setup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI Vladimir ,
please find the topology..

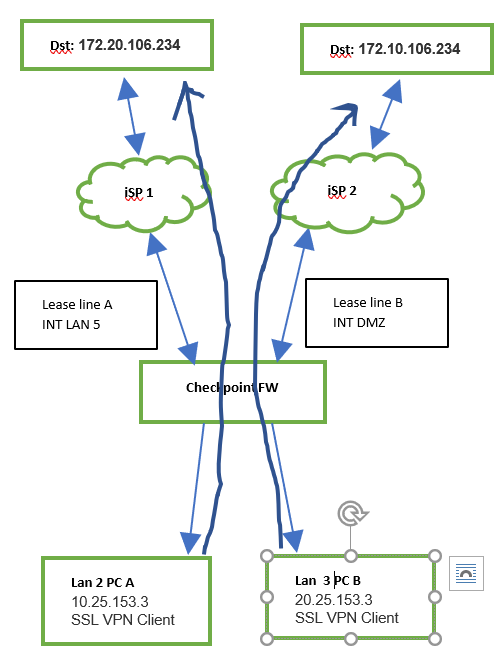
The Arrows segregating both network (2 different networks) .There is no internet connection,2 separate lease lines With Different brand FW VPN client able to connect , same implementation done with Checkpoint firewall instead of WAN int in fig 1 ,using LAN 5 as show in fig 5.
All required rules allowed(selected strict option) ,able to ping until ISP interfaces ,icmp not allowed dst ip ,while try to establish VPN connection can see out going traffic for ex: PC A to dst ip 172.20.106.234 as per logs which in shared to before .
same issue for both networks
Not able to find where the incoming traffic dropping ...SSL VPN client not connecting its showing not responded .
Firewall is Checkpoint 750 small business firewall ,R77.20.
kindly share if got any idea ....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"Strict" policy explicitly prohibits all internal networks from talking to each other, so we'll have to dig a bit to figure out what is going on.
the IP you are showing is the RFC1918 address, so you are not going over connections to ISPs, but private lines that should be connected to other internal interfaces.
To verify, please include screenshots of:
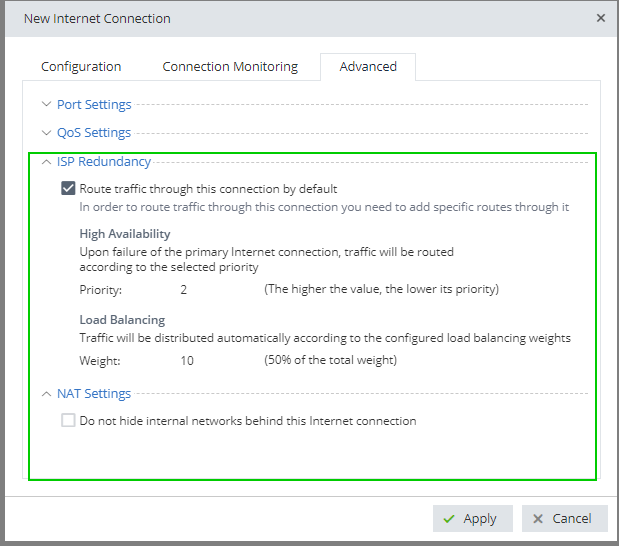
Your routing settings:

Your configuration for ISP redundancy and NAT for the gateway, i.e.:
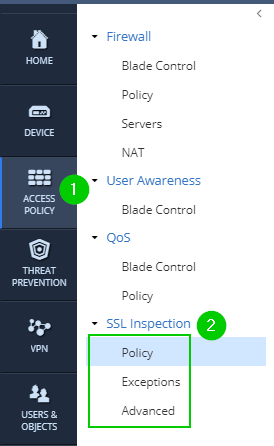
SSL Inspection Policy and Inspections:
And Firewall NAT policy settings (same screenshot as depicted here) and NAT Rules (3):
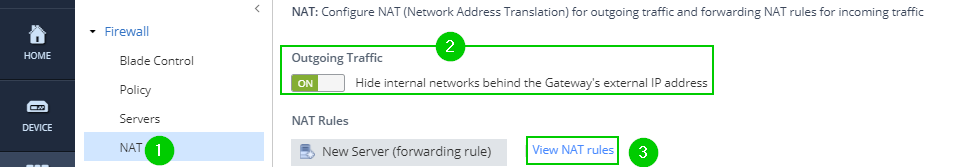
If the settings in the above section (2) are set to "On", turn it off, apply settings and try again.
Change Access Control Policy from "Strict" to "Standard" and attempt to establish SSL VPN.
For troubleshooting, use "fw monitor" command (please lookup sk describing its usage). The iIoO depicting traversal of the firewall's interfaces.
[Expert@drawbridge]# fw monitor -e "src=172.20.106.234 or dst=72.30.35.10 ,accept;"
fw: getting filter (from command line)
fw: compiling
monitorfilter:
Compiled OK.
fw: loading
fw: monitoring (control-C to stop)
[vs_0][fw_0] LAN1:i[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13357
ICMP: type=8 code=0 echo request id=1 seq=3195
[vs_0][fw_0] LAN1:I[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13357
ICMP: type=8 code=0 echo request id=1 seq=3195
[vs_0][fw_0] WAN:o[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13357
ICMP: type=8 code=0 echo request id=1 seq=3195
[vs_0][fw_0] WAN:O[60]: aaa.aaa.aaa.aaa -> 72.30.35.10 (ICMP) len=60 id=13357
ICMP: type=8 code=0 echo request id=12540 seq=3195
[vs_0][fw_0] LAN1:i[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13358
ICMP: type=8 code=0 echo request id=1 seq=3196
[vs_0][fw_0] LAN1:I[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13358
ICMP: type=8 code=0 echo request id=1 seq=3196
[vs_0][fw_0] WAN:o[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13358
ICMP: type=8 code=0 echo request id=1 seq=3196
[vs_0][fw_0] WAN:O[60]: aaa.aaa.aaa.aaa -> 72.30.35.10 (ICMP) len=60 id=13358
ICMP: type=8 code=0 echo request id=12540 seq=3196
[vs_0][fw_0] LAN1:i[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13359
ICMP: type=8 code=0 echo request id=1 seq=3197
[vs_0][fw_0] LAN1:I[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13359
ICMP: type=8 code=0 echo request id=1 seq=3197
[vs_0][fw_0] WAN:o[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13359
ICMP: type=8 code=0 echo request id=1 seq=3197
[vs_0][fw_0] WAN:O[60]: aaa.aaa.aaa.aaa -> 72.30.35.10 (ICMP) len=60 id=13359
ICMP: type=8 code=0 echo request id=12540 seq=3197
[vs_0][fw_0] LAN1:i[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13360
ICMP: type=8 code=0 echo request id=1 seq=3198
[vs_0][fw_0] LAN1:I[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13360
ICMP: type=8 code=0 echo request id=1 seq=3198
[vs_0][fw_0] WAN:o[60]: 192.168.7.148 -> 72.30.35.10 (ICMP) len=60 id=13360
ICMP: type=8 code=0 echo request id=1 seq=3198
[vs_0][fw_0] WAN:O[60]: aaa.aaa.aaa.aaa -> 72.30.35.10 (ICMP) len=60 id=13360
ICMP: type=8 code=0 echo request id=12540 seq=3198
If changing the policy from "Strict" to "Standard" worked, look closer at the rules you've created while using "Strict" policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
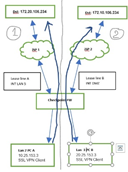
- In this scenario there is no ISP redundancy , here PC A,PC B should communicate respective dst as show in figure with arrows. ( as mention 1 and 2 in fig),here 1 and 2 are separated network .
- that's why implemented with LAN 5 ( separated from LAN Switch ),DMZ instead using WAN int ( for example 1 as shown fig ) .
- also tried with standard policy and with INT WAN (instead of LAN 5 ) for Network 1 able to ping to ISP 1 interface directly connected INTERFACE.Can not initiate VPN .
- Until Firewall interface only under my control from LAN PC's .
- Routing are directly connected ,
- NAT is turned off as you mentioned .
- The option which you mentioned SSL VPN inspection need to check with HTTPS categorization mode on my side weather how its working
- With same setup will check with Standard Policy .
Thanks for your valuable replies ..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
Does this rely to r80.10? Might be a bug
https://community.checkpoint.com/thread/7267-tcpdump-r8010
Thanks
Kim
Best Regards
Kim
Kim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do not think 750 appliance are capable of running R80.10.
My money is on simple configuration error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nah, those 700 SMB GW’a are running on Gaia embedded R77.20.x and not (yet) on R80.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just saw you were using tcpdump with parametre -Penni and it also generated an error. This Tim Hall found as a bug. I dont know if this could be the issue.
I would have removed the parametre to first see if traffic flows as expected.
I think Vladimir Yakovlev got a point about a misconfiguration.
Thanks
Kim
Best Regards
Kim
Kim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All , Thanks for giving valuable info ,Special thanks to Vladimir ..
The issue got resolved its because of anti spoofing dropping.And modified routing and policy configuration .Now it working with Strict mode.In Cli globally disable the anti spoofing.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 10 | |
| 10 | |
| 8 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


