- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: GotoAssist doesn't work when Inspection SSL is...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
GotoAssist doesn't work when Inspection SSL is enable
Hello,
We have a problem to acces at the website GoToAssist
We have identified the problem. The problem appears when the SSL inspextion is enable and we had to applicate a bypass rule but it worked before.
We had see for example in fortinet KB activate a bypass rule, sonicwall change the Cipher Method from Default to AES256-SHA or AES128-SHA or 3DES-SHA or RC4-MD5 to resolve this problem.
Have you an idea ?
Best Regard's
3 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume that GoToAssist is like GoToMeeting and this is mentioned here: Several HTTPS web sites and applications might not work properly when HTTPS Inspection is enabled on...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Greg,
On the App/URL Filter tab, go to Applications/Sites --> New --> Category. Name it SSL_Bypass.
Same tab, go to Applications/Sites --> New --> Application/Site. Name it GoToMeeting, click next.
On the next screen, add all of the URLs listed in the following support page:
https://support.logmeininc.com/gotomeeting
Make sure you use wildcards where indicated. On next screen give it a category of SSL_Bypass.
I did not find it necessary to whitelist any of the IPs or ports listed, just the URLs.
Create a rule under HTTPS Inspection policy. Make sure there are NO inspection rules above this bypass rule (all of your bypass rules should be at the top of your policy)
"Some Name" | src:Any | dst:Internet | services: http/https | site category: SSL_Bypass | action: Bypass
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It does not work because of certificate pinning.
Looks here and act accordingly: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume that GoToAssist is like GoToMeeting and this is mentioned here: Several HTTPS web sites and applications might not work properly when HTTPS Inspection is enabled on...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The proposed solution in Sk112214 did not address the situation with GoToMeeting. Has anyone come up with a work around apart from turning off HTTPS inspection?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm running into this issue to. Michael, did you have any luck?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Create an HTTPS inspection bypass, that should help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
While I see that as an option I'm trying to figure out if there is something else going on here. I was told that our apps team had no issues with GoToMeeting earlier in the week before I upgraded Checkpoint Management and Log Servers from R80.20 Take_87 -> Take_103. Would this possibly have had anything to do with it or just a coincidence?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You could easily go back to the older JHF take and test again to be sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is what I have in the log.
Date is Wed Jul 17 23:19:30 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPsuite-R80.20/fw1/lib/
implied_rules.def was updated
te.def was updated
===========================================================
Date is Wed Jul 17 23:21:48 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPR77CMP-R80.20/lib/
******* Warning : te.def had no signature file to compare to this will be considered as a match
vpn_table.def was updated
te.def was updated
===========================================================
Date is Mon Sep 30 12:27:04 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPsuite-R80.20/fw1/lib/
******** implied_rules.def was changed by user, signature didn't match!
===========================================================
Date is Mon Sep 30 12:30:06 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPR77CMP-R80.20/lib/
/opt/CPR77CMP-R80.20/lib//vpn_table.def wasn't backed up, the backup file already exists
/opt/CPR77CMP-R80.20/lib//te.def wasn't backed up, the backup file already exists
vpn_table.def was updated
te.def was updated
[Expert@GW-MGMT:0]#
Date is Wed Jul 17 23:19:30 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPsuite-R80.20/fw1/lib/
implied_rules.def was updated
te.def was updated
===========================================================
Date is Wed Jul 17 23:21:48 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPR77CMP-R80.20/lib/
******* Warning : te.def had no signature file to compare to this will be considered as a match
vpn_table.def was updated
te.def was updated
===========================================================
Date is Mon Sep 30 12:27:04 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPsuite-R80.20/fw1/lib/
******** implied_rules.def was changed by user, signature didn't match!
===========================================================
Date is Mon Sep 30 12:30:06 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPR77CMP-R80.20/lib/
/opt/CPR77CMP-R80.20/lib//vpn_table.def wasn't backed up, the backup file already exists
/opt/CPR77CMP-R80.20/lib//te.def wasn't backed up, the backup file already exists
vpn_table.def was updated
te.def was updated
[Expert@GW-MGMT:0]#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I received this notification after the take upgrade, but didn't think anything of it. I contacted Checkpoint Support and they didn't feel it was an issue.
• Additional Info:
fw1/bin/hook_fw1_wrapper_HOTFIX_R80_20_JUMBO_HF_MAIN: The updated inspect files were NOT installed due to signature mismatches or error. To process further please refer to sk116455.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Output of log below - Any concern here?
Date is Wed Jul 17 23:19:30 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPsuite-R80.20/fw1/lib/
implied_rules.def was updated
te.def was updated
===========================================================
Date is Wed Jul 17 23:21:48 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPR77CMP-R80.20/lib/
******* Warning : te.def had no signature file to compare to this will be considered as a match
vpn_table.def was updated
te.def was updated
===========================================================
Date is Mon Sep 30 12:27:04 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPsuite-R80.20/fw1/lib/
******** implied_rules.def was changed by user, signature didn't match!
===========================================================
Date is Mon Sep 30 12:30:06 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPR77CMP-R80.20/lib/
/opt/CPR77CMP-R80.20/lib//vpn_table.def wasn't backed up, the backup file already exists
/opt/CPR77CMP-R80.20/lib//te.def wasn't backed up, the backup file already exists
vpn_table.def was updated
te.def was updated
Date is Wed Jul 17 23:19:30 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPsuite-R80.20/fw1/lib/
implied_rules.def was updated
te.def was updated
===========================================================
Date is Wed Jul 17 23:21:48 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPR77CMP-R80.20/lib/
******* Warning : te.def had no signature file to compare to this will be considered as a match
vpn_table.def was updated
te.def was updated
===========================================================
Date is Mon Sep 30 12:27:04 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPsuite-R80.20/fw1/lib/
******** implied_rules.def was changed by user, signature didn't match!
===========================================================
Date is Mon Sep 30 12:30:06 2019
HFA index is R80_20_JUMBO_HF
Path is /opt/CPR77CMP-R80.20/lib/
/opt/CPR77CMP-R80.20/lib//vpn_table.def wasn't backed up, the backup file already exists
/opt/CPR77CMP-R80.20/lib//te.def wasn't backed up, the backup file already exists
vpn_table.def was updated
te.def was updated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Additionally, here are the changes I saw on the files it said were not backed up. Doesn't look like much of anything to me.
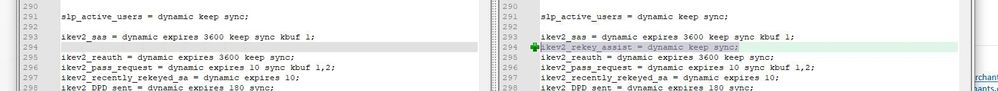

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Greg,
On the App/URL Filter tab, go to Applications/Sites --> New --> Category. Name it SSL_Bypass.
Same tab, go to Applications/Sites --> New --> Application/Site. Name it GoToMeeting, click next.
On the next screen, add all of the URLs listed in the following support page:
https://support.logmeininc.com/gotomeeting
Make sure you use wildcards where indicated. On next screen give it a category of SSL_Bypass.
I did not find it necessary to whitelist any of the IPs or ports listed, just the URLs.
Create a rule under HTTPS Inspection policy. Make sure there are NO inspection rules above this bypass rule (all of your bypass rules should be at the top of your policy)
"Some Name" | src:Any | dst:Internet | services: http/https | site category: SSL_Bypass | action: Bypass
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, I gotcha. We have some existing domain bypasses in by site already for other stuff. Going to severely limit the source on these though as I don't need everyone bypassing these domains.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It does not work because of certificate pinning.
Looks here and act accordingly: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 14 | |
| 10 | |
| 8 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


