- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: CheckPoint TLS 1.3 support: When?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
CheckPoint TLS 1.3 support: When?
I just finished reading the Gartner 2019 "Magic Quadrant for Network Firewalls", courtesy of CheckPoint Marketing.
One of the specific "Cautions" they called out for CheckPoint is the lack of TLS 1.3 support, something apparently both Fortinet and Palo Alto already have. BTW: Fortinet and Palo Alto both scored higher and more to the right than CheckPoint in the Leaders quadrant, Palo Alto significantly so.
Does anyone have any knowledge of the timeline for support of TLS 1.3, especially in regards to Threat Prevention / HTTPS inspection? The only info I can find from the Community is a post that's over a year old: https://community.checkpoint.com/t5/General-Management-Topics/Impact-of-upcoming-ESNI-with-TLS-1-3-o..., where Phoneboy said it was to early to say.
Any updates on the topic?
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @LCarrau808,
While support for TLS 1.3 in HTTPS Inspection is planned for next year, the Gateway is fully capable of downgrading TLS sessions to TLS 1.2. Because of this, inspection is expected to fail only in cases where websites don't support TLS 1.2 (or below).
TLS 1.2 is supported everywhere and considered secure, so websites and browsers aren't expected to disable it anytime soon. If you see an error screen, it may be because of something else.
Thanks,
Dor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Dale_Lobb,
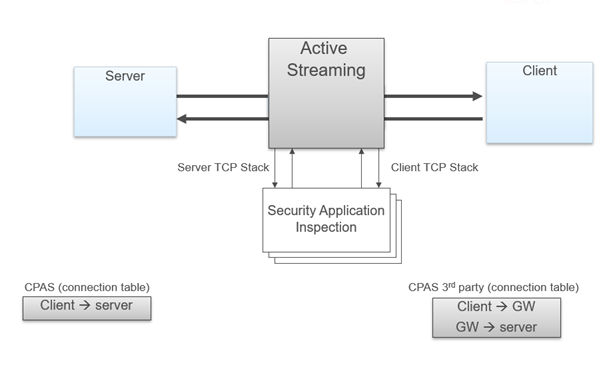
Active Streaming (CPAS) - Check Point Active Streaming active streaming allow the changing of data, we play the role of “man in the middle”. CPAS breaks the connection into two parts using our own stack – this mean, we are responsible for all the stack work (dealing with options, retransmissions, timers etc.).
General overview:
- CPAS breaks the connection into two parts using our own stack – this mean, we are responsible for all the stack work (dealing with options, retransmissions, timers etc.)
- An application is register to CPAS when a connection start and supply callbacks for event handler and read handler.
- On each packet, CPAS send the application the packet data with cpas_read, allow the application to change the data as it like, and send the data forward with cpas_write.
- CPAS server side stack negotiates the TLS version with the web server. If the highest version of TLS 1.3 is used by the web server, CPAS will try to negotiate a lower TLS version for example TLS 1.2 or TLS 1.1 if the Web server supports this.
Active Streaming – https content step by step:
Packets of SSL handshake are passed to the SSL engine to exchange keys. When the connection and the SSL handshake is fully established, an hook will be register for this connection to handle the decrypt / encrypt of the packets. When a packet arrive to CPAS, a trap will be sent and the SSL engine will receive the encrypted packet, decode the packet and return it to CPAS. The packet will enter the receive queue and the application will be able to work on it, once he done he will send it to the write queue. The packet will pass to the SSL engine for encryption and pass to the other side (Client, Server).
More read here:
R80.x - Security Gateway Architecture (Content Inspection)
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Keep in mind that the majority of sites (around 85%) don't even support TLS 1.3 yet.
It's planned for next year.
It's planned for next year.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @PhoneBoy .
Is there a way to configure a Bypass only to websites with TLS 1.3 or a way to prevent the Error Screen on Browsers?
Thanks in advanced.
Lanello
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Possible that this will work better in R80.30.
But as far as I know, you can't just bypass a site that has TLS 1.3 unless you happen to know what IP it has.
But as far as I know, you can't just bypass a site that has TLS 1.3 unless you happen to know what IP it has.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We were "lucky" enough to find a site requiring TLS 1.3 and not lowering to a different cipher if that did not work.
HTTPS Inspection bypass (even knowing the IP of the site) does not resolve the problem.
What can we do in order to allow this site through the firewall in R80.40? I am probably missing something very simple (or I hope so).
This thread is from 2019, but in 2021 here we are with the same problem and upgrading to R81 is not an option at this time.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bypassing by IP should be sufficient.
This probably require a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @LCarrau808,
While support for TLS 1.3 in HTTPS Inspection is planned for next year, the Gateway is fully capable of downgrading TLS sessions to TLS 1.2. Because of this, inspection is expected to fail only in cases where websites don't support TLS 1.2 (or below).
TLS 1.2 is supported everywhere and considered secure, so websites and browsers aren't expected to disable it anytime soon. If you see an error screen, it may be because of something else.
Thanks,
Dor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Dale_Lobb,
Active Streaming (CPAS) - Check Point Active Streaming active streaming allow the changing of data, we play the role of “man in the middle”. CPAS breaks the connection into two parts using our own stack – this mean, we are responsible for all the stack work (dealing with options, retransmissions, timers etc.).
General overview:
- CPAS breaks the connection into two parts using our own stack – this mean, we are responsible for all the stack work (dealing with options, retransmissions, timers etc.)
- An application is register to CPAS when a connection start and supply callbacks for event handler and read handler.
- On each packet, CPAS send the application the packet data with cpas_read, allow the application to change the data as it like, and send the data forward with cpas_write.
- CPAS server side stack negotiates the TLS version with the web server. If the highest version of TLS 1.3 is used by the web server, CPAS will try to negotiate a lower TLS version for example TLS 1.2 or TLS 1.1 if the Web server supports this.
Active Streaming – https content step by step:
Packets of SSL handshake are passed to the SSL engine to exchange keys. When the connection and the SSL handshake is fully established, an hook will be register for this connection to handle the decrypt / encrypt of the packets. When a packet arrive to CPAS, a trap will be sent and the SSL engine will receive the encrypted packet, decode the packet and return it to CPAS. The packet will enter the receive queue and the application will be able to work on it, once he done he will send it to the write queue. The packet will pass to the SSL engine for encryption and pass to the other side (Client, Server).
More read here:
R80.x - Security Gateway Architecture (Content Inspection)
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice information @HeikoAnkenbrand.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 20 | |
| 15 | |
| 10 | |
| 8 | |
| 8 | |
| 6 | |
| 6 | |
| 6 | |
| 6 |
Trending Discussions
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter