- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure the Workspace)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Endpoint Security -
Best Practices for 2024
Check Point Named Leader
In Mobile Threat Defense
Regulatory Compliance Update
For Non-US DoC Versions
Customer Threat Prevention
& Vulnerability Management Survey
CheckMates Toolbox Contest 2024
Make Your Submission for a Chance to WIN up to $300 Gift Card!
CheckMates Go:
Infinity AI Co-Pilot
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Blocking for specific file types in Check Poin...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Blocking for specific file types in Check Point Firewall
Hi there,
I wish to block for a range of specific file extensions in a Check Point Firewall. The way I have done it now is by making individual "File Attribues" (sub category to "Data Types") and then in the field "The file name contains" under "File Properties" the actual file extension, e.g. ".com" (without the quotes).
However, this doesn't seem to be a bullet proof solution because the field interprets it as RegEx. So if a file name is named something with "com" in it it will block for the file even it is a allowed file type.
So my question is two fold:
1. I can define the field "The file name contains" in RegEx as "^.*\.(com)$", which seems to work, however, is that something that will effect perfomance on the firewall? We have araound 30 specific file types we want to block. I've made a "Data Type Group" with all the individual made "File Attributes" and then a rule that drops traffic if "Content" matches any of them.
2. Is there a smarter to accomplish this? I.e. blocking for specific file types.
I hope it makes sense and you are able to help.
Thanks
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We use the following syntax and also use multiple DataTypes in a group:
(?i).*\.(exe|msi|cmd|bat)$
No noticable performance impact and it should only match a file extension and is also case insensitive (.eXe will also be blocked). In total we block around 20-30 different file types and also apply different rule to specific users (e.g. Developers).
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
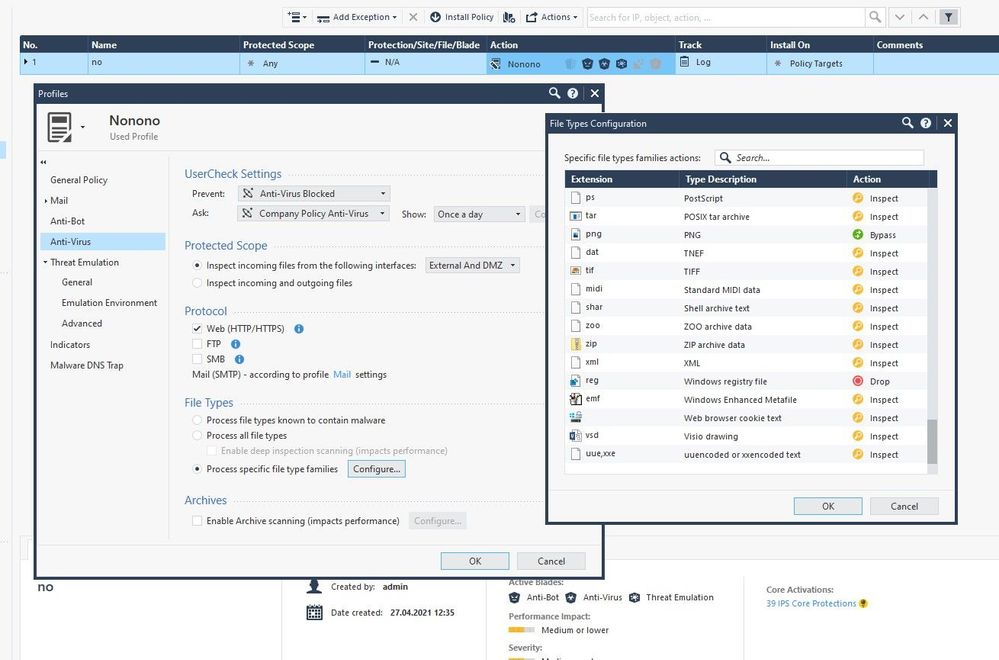
RegEx can effect the performance rather much when frequently used. I do not use Content Awareness but the file types in TP policy - in AntiVirus, i can select Block. Inspect or Bypass for every file type, scope and protocol:
So if you have NGTP services, this will be very easy.
CCSE / CCTE / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, and thanks for the input,
We don't use the Antivirus, but will start using it soon. I am blocking file types via the Content Blade (sorry, I probably should have been more specific on that). I will have a look into whether it suits the purpose. however, will it scan all files when a user browses? Or does the antivirus only work when a user specifically downloads files?
Hope it makes sense.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As seen on the left of the screenshot, you can select the following:
- Scope: incoming (by interface) or incoming & outgoing
- Protocol: http(s) FTP SMB SMTP
CCSE / CCTE / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I use content awareness blade for that, little tricky to make it work, but does the job.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, we're also using Content Awareness. The only issue is whether having 30-ish individual File Attributes using RegEx will affect the overall performance. Do you use RegEx to define file types?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Version/JHF level?
Are you doing this with DLP or are you doing this with Content Awareness?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Version R81 and Take 81.
We are doing these via Content Awareness, and not DLP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Content Awareness is the right tool for this job, but in any rule invoking content objects be very sure that it is only being applied to traffic to and from the Internet, and not trying to inspect high-speed traffic between internal networks or between internal networks and DMZs. Some of Content Awareness happens in user space daemons which can definitely impact performance.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply.
Good point about only applying it on traffic from the Internet.
Is trying it out with some RegEx like Marcel_Gramalla has suggested below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To also add to what @Timothy_Hall mentioned, which are all valid points, I will give you something to think about, so you are not shocked :-).With content awareness, you need to have https inspection enabled, otherwise, it will never work. Now, once thats configured, you will NEVER get blocked page when file is blocked, simply does not work. Also, something to consider is that as Tim said, do NOT put any in those rules, but ensure Internet is set as destination. Last, but not least, MAKE SURE that if content awareness is enabled, if whatever you are bypassing in https inspection policy, dont expect it to work correctly with content awareness layer, as that traffic has to be inspected.
Just some pointers from my experience working on this with a customer and having case on it with TAC escalations for more than a month.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The point about block pages is wrong. This works with Content Awareness and HTTPS Inspection (how would a block page work without inspection?). As long as you are in a browser this works very good. If working from CLI you could use the UserCheck client as well (we only have it installed for troubleshooting).
Maybe you mean something different?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Its not wrong, TRUST ME, it does not work : - ). What I mean is this...so the way you get user check block page for https inspection is fine, but same fails if file is blocked via content awareness, just gives network error notification at the very bottom. Even esc. guy told us that never worked properly and they have no idea why. He even said they raised task with R&D about it, but it never got fixed.
You can also refer to below post by Vladimir:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe exe file, but we did msi and it never worked. Would you mind send a screenshot of the rule?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There you go. I initially thought about a different issue reading your message but I remember we had this issue where it would start the download and just fail at the end. We had this mainly with archives (that we inspect) and it had something to do with strict hold etc..
We use R81.10 and also increase file size limits for both Content Awareness and Anti-Virus (both with archive scanning enabled). We somehow ended with this state where block pages are working also for the most archives (and it blocks the .exe or .msi inside it).
The second screenshot shows the putty-0.78.tar.gz which gets blocked correctly as well (with a custom RegEx filetype).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
K, fair enough, maybe things changed since almost a year ago when we did this. User check page you have there, did you create custom one just for content awareness blade?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, we have different ones for URL Filtering, Content Awareness etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I thought there was built in one for content awareness, but I guess not, cant see one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We use the following syntax and also use multiple DataTypes in a group:
(?i).*\.(exe|msi|cmd|bat)$
No noticable performance impact and it should only match a file extension and is also case insensitive (.eXe will also be blocked). In total we block around 20-30 different file types and also apply different rule to specific users (e.g. Developers).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply.
I will be trying something similar and keep on eye on performance, though, so far, it doesn't seem to affect it negativaly.
Logically, it wouldn't really make sense if it did (compared to how I did before), since it already interpreted all the individual File Attributes objects I had made before as RegEx. In fact, that might even result in more negative performance.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 21 | |
| 11 | |
| 10 | |
| 5 | |
| 5 | |
| 5 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Thu 01 Aug 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: What's new on Check Point CloudGuard!Tue 06 Aug 2024 @ 05:00 PM (CEST)
Americas CheckMates Live - Infinity XDR/XPR Q2 Product UpdatesThu 01 Aug 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: What's new on Check Point CloudGuard!Tue 06 Aug 2024 @ 05:00 PM (CEST)
Americas CheckMates Live - Infinity XDR/XPR Q2 Product UpdatesWed 14 Aug 2024 @ 05:00 PM (CEST)
Transform Your Data Center Management: The Power of Check Point’s Managed-Firewall-as-a-ServiceAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter