- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: About external interfaces
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
About external interfaces
Hi experts,
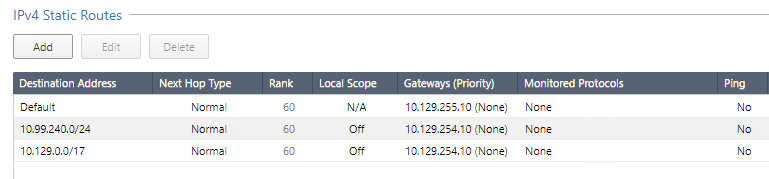
I have read this article Interface - Topology Settings but still I can't understand how an external interface is defined. When a new firewall is set up, or if I do a "Get interfaces with topology", the external interfaces are those which are gateways for static routes? For example, if I have this in GAIA:
Gateways for 10.129.254.10 and 10.129.255.10 are interfaces eth10 and eth11, respectively. Does this mean eth10 and eth11 will be external, and the rest of interfaces will be internal?
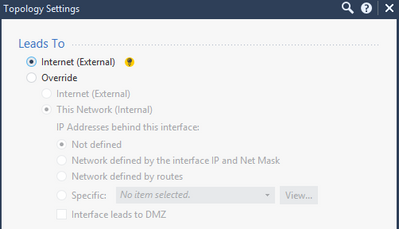
What exactly does it mean "...calculated from the topology of the gateway"?
Internet (External) or This Network (Internal) - This is the default setting. It is automatically calculated from the topology of the gateway.
Regards,
Julián
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you do Get Interfaces with Topology, whichever interface has the default route is set to External. Antispoofing groups are built for all the other interfaces containing network objects for the networks which route out that interface.
In most situations, you should only use External and Internal > Network Defined by Routes. Manually managing your antispoofing topology is a great way to shoot yourself in the foot over and over forever.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@fjulianom It's safe to do "get interfaces" in production. It won't take effect until you accept, publish and push the policy. Just make sure you don't publish anything and discard it. Usually, the only interface marked as "External" is the one linked to your default route. The logic is quite basic. I tend to switch most interfaces to "defined by routes".
External in this regard is in the context of the firewall. Is the traffic behind or in front of the firewall? On a firewall connected to the Internet, the external interface would normally be the one the firewall itself uses for outbound traffic. Even if you have DMZ networks with public IP addresses, you usually mark them as "Internal" and add the option "Interface Leads to DMZ". This ensures that Threat Prevention Policies will treat your DMZ subnets like they are external adding additional protection by default.
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you do Get Interfaces with Topology, whichever interface has the default route is set to External. Antispoofing groups are built for all the other interfaces containing network objects for the networks which route out that interface.
In most situations, you should only use External and Internal > Network Defined by Routes. Manually managing your antispoofing topology is a great way to shoot yourself in the foot over and over forever.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Bob,
Ok, but in my case only one interface has the default route (eth11), the other one (eth10) has static routes, and both of them appear as Internet (External):
Shouldn’t eth10 appear as Internal?
Regards,
Julian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Julian,
2 questions:
1) What happens if you click "get interfaces without topology"?
2) What IP is defined for internal interface?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Andy,
I don't understand your questions:
1. I can't do a "get interfaces...", the firewall is in production.
2. What internal interface do you refer to?
Regards,
Julián
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@fjulianom It's safe to do "get interfaces" in production. It won't take effect until you accept, publish and push the policy. Just make sure you don't publish anything and discard it. Usually, the only interface marked as "External" is the one linked to your default route. The logic is quite basic. I tend to switch most interfaces to "defined by routes".
External in this regard is in the context of the firewall. Is the traffic behind or in front of the firewall? On a firewall connected to the Internet, the external interface would normally be the one the firewall itself uses for outbound traffic. Even if you have DMZ networks with public IP addresses, you usually mark them as "Internal" and add the option "Interface Leads to DMZ". This ensures that Threat Prevention Policies will treat your DMZ subnets like they are external adding additional protection by default.
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi RamGuy239,
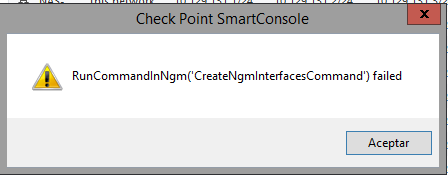
I didn't forget this topic. I wanted to do a "get interfaces" but I had this error because for some reason I have some interfaces locked:
So I open a TAC case to solve this. Anyway, I have been investigating my firewall configuration and I think I have two external interfaces because I have the default route via eth11, eth10 has static routes, but in the PBR section eth10 is used as default route, this makes more sense.
Regards,
Julián
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Hi RamGuy239,
I solved the problem. I was able to do "Get interfaces" and after doing it, both interfaces appeared as external. As said before, I think these two interfaces are external because I have the default route via eth11, eth10 has static routes, but in the PBR section eth10 is used as default route.
Regards,
Julián
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I saw your answer to my post just now, apologies. Well, this can be topic for discussion, but I will throw in my 2 cents. Personally, I always suggest to do get interfaces without topology, specially in production. Plus I believe its good idea to use option "network defined by routes", because thats CP recommended way to begin with. Please refer to below:
Cheers,
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 26 | |
| 22 | |
| 10 | |
| 9 | |
| 8 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 5 |
Upcoming Events
Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANThu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter