- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Workspace
- :
- Endpoint
- :
- Re: Official CP Endpoint Install / Windows Server ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Official CP Endpoint Install / Windows Server 2019 Defender AV / Firewall disable procedure?
Hi All,
I am about to deploy Check Point Endpoint Security client 80.30 with Antimalware Engine 2 (E2) on a number of Windows Server 2019 and 2016 Hyper-V Guest VMs and at least 1 bare metal server.
As of yet, I have not heard what the official installation procedure should be considering the content of this Knowledgebase article, which indicates that Server 2019 no longer plays nice by disabling it's internal antivirus and firewall components when 3rd party security clients are installed.
The SK mentions that you must disable Windows Defender Antivirus and Firewall BEFORE installing the CPEP client,
I had not seen or heard of this behavior before installing CPEP on a windows server 2019 VM hosting our Blackberry UEM MDM platform, so CPEP went in on top of the MS components. I have since only disabled the Windows Defender Firewall for just "domain" network profile for that VM.)
The SK also mentions that this can be done "via GPO" but does not cover how. (caveat, I have yet to, but will fully read through the whole admin guide and whatever other documentation I can find for the latest releases of CPEP to see if it is covered there and will report back if I have a definitive answer)
With that said,
The following Microsoft post:
Which suggests that a registry edit will make WD AV go "passive" is enough,
Is somewhat in conflict with this Microsoft post
Which somewhat ambiguously seems to state that you can uninstall windows defender completely using the add remove roles and features Wizard, after suggesting earlier in the post that removing the feature components only removes the user interface.
All very confusing.
Anyway, would anyone from Check Point proper like to suggest the specific steps one should take if we intend to deploy CPEP to even a newly built Windows 2016 or 2019 server with nothing but the OS installed yet?
What would be the GPO to which the SK refers?
Should we be uninstalling the whole feature as described in the second Microsoft link?
Also, regarding the aforementioned Blackberry UEM server: I deployed the client while actually working with CP support on a Zoom remote support session. I happened to notice that windows firewall was still running during the same remote session; I was told at that stage that the wscsvc service was removed in the OS and this is Microsoft's doing and by their design. At the end of the day I am therefore at a disadvantage in the case of this specific production server if I was supposed to turn off Windows Defender Anti-Malware BEFORE installing CPEP.
So, a specific question, did I break anything by having installed CPEP on a windows Server 2019 machine before "turning off" Windows Defender Anti-Malware? I would assume not if the TAC engineer did not indicate this, but I want to be sure. Once I know what the correct "turn off" method is for Defender per CP, I just hope there is nothing I need to worry about having done things in the wrong order.
I would be interested to hear anyone's experiences with CPEP and Windows Server 2016 / 2019 and whether you noticed any issues, or whether you realized that Windows Defender components were still running.
Thanks!
Chris.
EDIT:
This is Microsoft's Antivirus and antimalware software: FAQ for reference:
19 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Chris,
You should uninstall Windows Defender on windows server 2016+,
This is useful if you have a third-party antivirus product installed on the machine already. Multiple AV products can cause problems when installed and actively running on the same machine.
See instruction here: https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-antivirus/windo...
Using group policy: https://www.prajwaldesai.com/how-to-turn-off-windows-defender-using-group-policy/
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have also updated sk162735 with instructions for Windows Server 2016 and up.
The changes will be visible from tomorrow (28.10.19).
The changes will be visible from tomorrow (28.10.19).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The GPO does not address Windows Defender Firewall, as far as I can see.
I will do further testing to confirm.
If this is the case, then it seems the manual removal of the Windows Defender Feature is required if you are deploying Check Point Endpoint client's Firewall blade as well as Anti-Malware.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
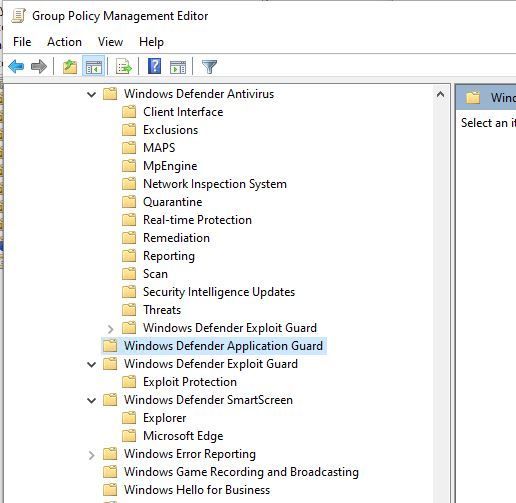
Yes, confirmed that Windows Defender Firewall is not disabled using the aforementioned GPO method.
Further, when I look at the Group Policy Management console from a fully updated Windows 10 Pro PC in the domain, there are a number of components to deal with.
I really want to make sure I do things right the first time.
What do you suggest I disable?
I have not tried removing the Windows Defender Feature yet. I will try that now, but if there is a best practice way of disabling any Windows based security client components that might interfere with any of the full set of CPEP blades (via GPO) I would like to know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would rather do this together with TAC !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
G_W, Absolutely.
Kiril is actually the technology leader for the Endpoint product line, I have been working with him on another Endpoint concern, and I hope to hear back from him again today.
Kiril has been awesome to work with, I will hopefully get a definitive answer so I can add it to my "runbook" of deployment procedures for new / reimaged PCs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Disabling Windows Defender Anti-Malware and Windows Defender Firewall is needed for Windows Server 2016/2019 machines only, if you plan to install Endpoint Security client on it with Anti-Malware and Firewall Blades.
I have added links to Microsoft instructions on disabling these two components for Windows Servers 2016\2019 for SK159373 and SK162735.
Reference to GPO was removed.
If you wish to mass disable Windows Defender Firewall\uninstall Windows Defender Anti-Malware - Powershell scripts can be used from the instructions above for all Windows Servers 2016\2019. The scripts can be applied via GPO.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the update Kiril!
Does this mean that Windows 10 will disable Windows Defender Firewall and Windows Defender Anti Malware automatically when the CPEP client is installed with FW and AM blades enabled?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, on Windows 10 machines, in case Endpoint Security Firewall or\and Endpoint Security Anti-Malware blades are installed - Windows Defender (AV) or\and Firewall will be turned off (this is done with wscsvc (Windows Security Service) service that must be running, which is absent in Windows Server 2016 and 2019, as per Solution section in SK159373 mentioned above).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great that's all I need to know to start deploying workstations!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kiril, We've recently started pushing out endpoint client upgrades to users who are on older version to E84.00 and some users have reported they are getting windows security popup after the update any idea why it might be coming?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
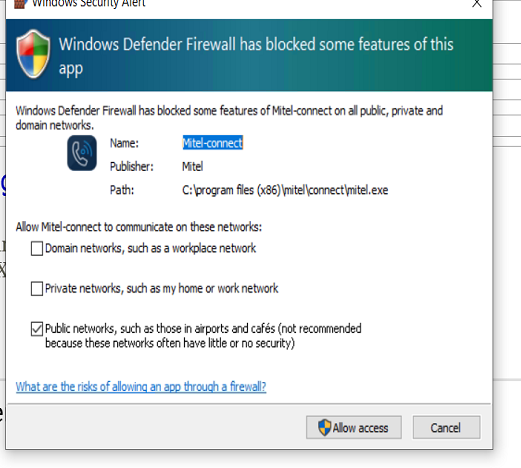
yes the popup is related to windows defender firewall and mitel connect application but is it not supposed to happen when endpoint client is installed? we thought windows firewall service is turned off by checkpoint endpoint client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have seen this behavior on Windows Server 2016 and 2019 because (from what both TAC and development has told me) Microsoft removed the API call to hand off control of firewall and antimalware to third party products at install time. You need to manually disable them. Windows 10 however still plays nice and the Windows Security panel will indicate who is providing firewall and antivirus services. Take a look at that and see if it mentions Check Point as providing firewall. If so, that is an even more strange occurrence considering the dialog box you saw.
It is troubling to hear that this behavior is showing up in an 84.xx build of EP on Windows 10 workstations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for updating this. Just a quick update on version 88.33.1009 I DID have to disable Windows Firewall manually. The client looked like it might have been trying to do it but just flashed and seem to get stuck in a loop. Disabling firewall allowed it to complete the install.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Was this on a Windows Server installation? or a Windows 10 / 11 machine?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It was a Windows Server 2019 physical server. Specifically, a HPE DL360 Gen 9 ProLiant.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the clarification.. I am about to do a refresh of our two boxes one is Security management/smartevent / logging / Endpoint management, the other is a gateway..
Going from R80.40 to R81.20 with an export, then wipe of the management box / Isomorphic install of R80.20 and import and then likely in place upgrade of the gateway from R80.40 to R81.20
From there going to completely revamp the Endpoint deployment and security policies with the latest capabilities and the latest version of the clients, which are supposed to be server OS and Server application aware, if I remember correctly (like knowing specifically how to handle an on premise exchange server, or a SQL server etc..
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter