- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Harmony
- :
- Endpoint
- :
- Re: Identify Threat Emulation Event - Details
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Identify Threat Emulation Event - Details
Hello tech´s,
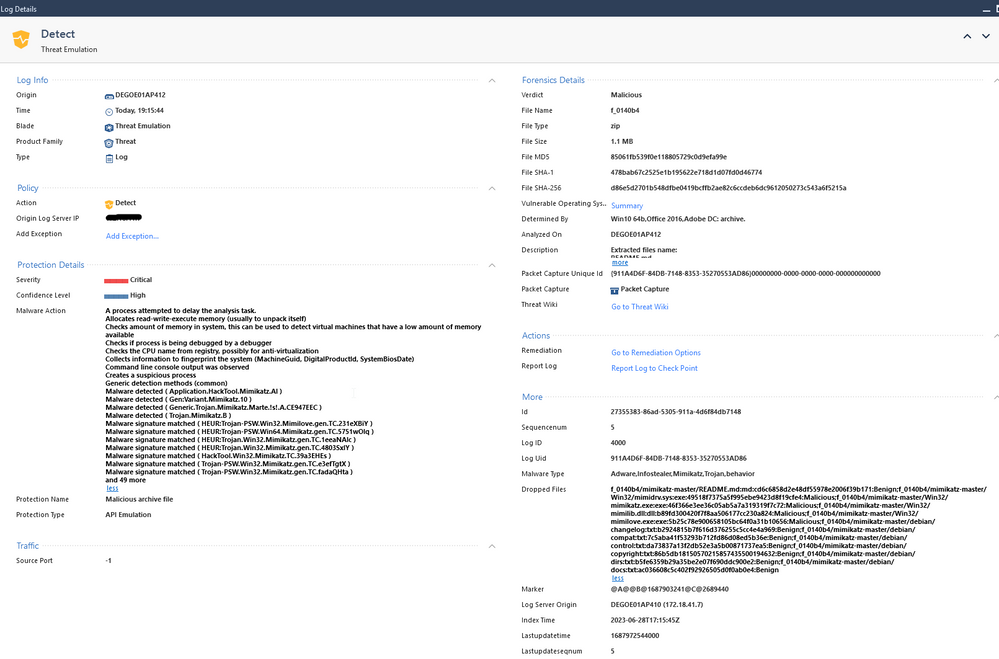
I can regulary see these events:
In the details I see that the Threat Emulation is doing fine and all malicious files have been droppt.
But I am more than interested of knowing where the emulation has been initiated from to inspect this specific device deeper.
I spent already some time in that but cannot find more information on that.
Hope my case is clear.
Cheers,
Oliver
CCES / CCSA / CCSE
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"API Emulation" implies another system / product (e.g. Browser extension) is submitting the files for evaluation so there will likely be details there to review.
But to start I would suggest reviewing the forensic report for more information if you've not already?
In the log window, under Forensic Details refer to the Vulnerable Operating Systems row - click on the Summary link.
If the browser extension is used verify the logging options are set per:
https://support.checkpoint.com/results/sk/sk108695
https://support.checkpoint.com/results/sk/sk171179
*Note: The Log is "Detect" not "Prevent" and the reference to dropped files is not in this context hence further investigation is warranted.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Chris,
thank you for getting in touch on this.
In the log window, under Forensic Details refer to the Vulnerable Operating Systems row - click on the Summary link.
-> I can see what happened on the emulated OS incl. the Emulation Video. but I cannot identify from which client the emulation came from.
If the browser extension is used verify the logging options are set per:
-> I´ve checked the log settings in the registry and all
CCES / CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you check the corresponding gateway setting to receive them?
What Endpoint client version is deployed and how is it managed?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you provide more informations on your last post?
CCES / CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Endpoint solution is either cloud managed or On-Prem.
Version wise is the client E86.80 or higher?
The SK article with the logs_enabled parameter also states:
The option needs to be enabled on the Security Gateway as well, logs_api_enabled needs to be set to TRUE under /opt/CPUserCheckPortal/phpincs/conf/TPAPI.ini
For faster resolution perhaps a remote session with TAC would be helpful.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chris,
our entire environment is On-Prem including TE Appliance.
Version is E86.50. We have a few test clients running on E87.20 as well.
Security Gateway = TE Appliance or is that our Endpoint Management Server?
CCES / CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TE appliance in this instance.
(Though obviously also worthwhile reviewing your Endpoint logs for the same time period aswell)
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, I checked the TPAPI.ini and the logs_api_enabled was set to TRUE.
CCES / CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK Good. Please contact TAC to investigate further.
Very conscious of the time spent here versus actually investigating the endpoint itself.
With respect to that element note we do have an Incident Response service you can engage where needed.
CCSM R77/R80/ELITE
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 21 Jan 2025 @ 04:00 PM (CET)
Boosting Network Performance with New R82 Software and AI-Powered Gateways - EMEATue 21 Jan 2025 @ 03:00 PM (EST)
Boosting Network Performance with New R82 Software and AI-Powered Gateways - AmericasTue 21 Jan 2025 @ 04:00 PM (CET)
Boosting Network Performance with New R82 Software and AI-Powered Gateways - EMEATue 21 Jan 2025 @ 03:00 PM (EST)
Boosting Network Performance with New R82 Software and AI-Powered Gateways - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter