- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Workspace
- :
- Endpoint
- :
- Re: Harmony Endpoint - Roadmap Survey
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Harmony Endpoint - Roadmap Survey
Hi All
We appreciate the CheckMates community, and it is very important for us to hear your feedback about Harmony Endpoint.
Please let us know in the comments regarding the following:
1. What is your most wanted feature / security capability?
2. What are the most urgent product improvements?
We in the product management team will analyze the feedback and will do our best to add those features to our product roadmap.
42 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Some enhancement requests I have come across:
Support for AzureAD (as a directory for groups, FDE user acquisition etc.)
URL filtering/Browse - logging allowed sites for reporting or ability to mix block and detect categories to log specifics. Additional actions on categories (Ask/Inform as per gateway options).
Ability to granularly allow which components are disabled when troubleshooting, with password or some other override so it can be better controlled.
Endpoint VPN integration with Smartconsole (mainly i'm working with Cloud Endpoint), simpler template site settings from trac.config .defaults etc. Simpler compliance control enforcing only full Endpoint client deployed from specific Endpoint Server to connect to RA VPN gw.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1.1If there would be more predefined categories in Port Protection. For example, smartphones, digital cameras, etc.
1.2 it would be easier to handle the manulally created Devices when you could create manually groups for port protection. Currently you can only create groups for storage devices
1.3 Also that you could only enable individual device categories in Bluetooth, such as Bluetooth is only enabled for Bluetooth headphones, and transferring files is not possible.
1.4 The Feature to disable the agent directly on the client would be good. Maybe over a right click on the lock icon, with an option to disable the agent with a request to tipe in the configured uninstall password.
2.1 A difficulty, as others have already mentioned, that the Harmony's services often use all of the computer's resources, mostly CPU. Often it's either forensics or threat emulation that use a lot of the cpu consumption. Most of the time we had to exclude many processes of the monitoring, after that the services from Harmony are using noticebaly less. But I dont think that is a solution for all time. In the last versions of the client its got better, examble with Windows Updates, but there still work to do.
2.2 Also, the Harmony often detects false/positives, leading to a long list of exclusions. Maybe can the Security-Engine better set up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Daniel
I will check it as well, appreciate the feedback.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another point where much room for improvement is the releasing of files that are curently in qurantine in Infinity Portal. At the moment the Incident ID or the file path must be entered, to release the file. It would be better to get a current view of the locked files on the client over Infinity Portal and then to have the possibility to decide which file I want to unlock.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great idea. Also to collect logs. We have to push an operation to collect logs, however we need to ask the user or someone from the customer's IT dept. to go to the machine and collect the files. Wouldn't it be easier if it automatically uploaded the files to Infinity Portal and then we could download it from the push operation that was sent?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I got another idea for a new feature for Harmony. Over time you create a lot of exclusions and you often no longer know what you have excluded or whether you still need it. A hit counter for the exclusions could show whether this exclusion still brings anything or whether the file may have been deleted. So you can clean the exclusions .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi BarYassure!
I just became a Chck Point user after the new interface, so excuse me if you guys already exausted all questions about:
*- When double clicking the Endpoint icon be able to choose what to see: Many times, I am interested into seeing what blades are installed by using the overview or the installed policies in the advanced options. VPN is my less used option, but I used it and is at hand with one right click on the icon.
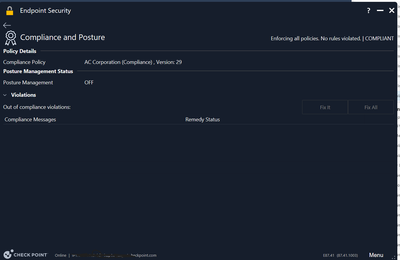
*- When a compliance and posture alert happen, I would like to see the alert on its dashboard. I have never seen a thing in here. Always is needed to open all the logs and it's a little bit bothering.
drive:/ ProgramData / CheckPoint / DBStore / Events / index.html
*- In this folder where are all the events:
drive:/ ProgramData / CheckPoint / DBStore / Events / index.html
the Index file takes forever to load!
"Please wait while the report is being generated." <--- stays waiting forever! I have to choose each event separately by surfing in the folders of each event.
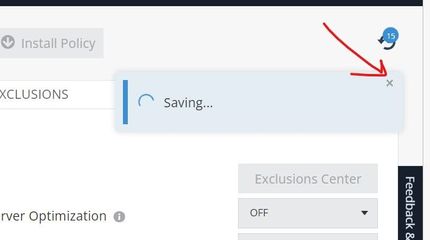
*- In the infinity portal: There are some notices that appears over the right side of the screen when applying changes, OMG, please allows the whole little square to be a button and not only the "x" on the top corners. sometimes I am using a small screen and its stressing trying to hit that x. Plus, in certain occasions you need to click in the same area to apply another change and it's not easy.
this picture is just an example of which "x" I am talking about. Not this particular screenshot.
*- When is about blocking URLs in the URL Filtering in the Infinitum console for the Harmony client and when using a Check Point Firewall: I have not seen an option about how to is in the control of the URL, if the Endpoint Client or the Firewall. When unblocking or blocking site I have to do it in both places. Could be possible to improve this? no idea if this is feasible.
thanks!
Regards,
Oscar Catana
https://ipthub.com
Cyber Sec Passionate!
Oscar Catana
https://ipthub.com
Cyber Sec Passionate!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
and I would like to suggest that the Web Advertisements is not cataloged as "Critical" in the logs. unless there is an option to fix that and I have not seen it.
Regards,
Oscar Catana
https://ipthub.com
Cyber Sec Passionate!
Oscar Catana
https://ipthub.com
Cyber Sec Passionate!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. What is your most wanted feature / security capability?
* Configuration reporting (Policy / Exclusions) in a readable format. There are regulatory requirements about this
Even better would be reports that can be scheduled
* Ability to turn off a protection component for a single client, for diagnostic purpose
* Better integration between detection and exclusions. Now deciding which exclusions must be enabled in which module is an esoteric art form
* Better documentation. Please go further than "these are the items in the interface" to "this is how they work"
2. What are the most urgent product improvements?
* The client for server is, in my experience, quite instable and a real resource hog.
* Server exclusions, which you have released, would be great if we had a way to know what is excluded for which module
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agent Size
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
- What is your most wanted feature / security capability?
- Kaspersky antivirus for servers offers a very interesting feature: the locking of processes and files running on the server. For a week or more, the server is in "detection" mode. All processes, in addition to the default Windows processes, all scripts, executed files, services, etc., are collected according to their signature. Once we've collected all this information on the server, we authorize everything that needs to be authorized (or that we wish to authorize) and block everything else. This approach greatly enhances server security, as anything that hasn't been previously authorized is automatically blocked, be it new applications, new scripts or modifications to an existing script. It goes without saying that the server must be considered secure from the outset. The disadvantage of this method is that the slightest modification, such as adding an application or modifying a script, requires the addition of its signature to the database. However, this approach offers a significant advantage in terms of performance, as fewer analyses need to be performed on added processes, since they are considered authorized. Activating and deactivating this mode is quick and easy, as is database management (retrieval of new signatures).
- MFA Azure directly integrated into the VPN client (without overly specific gateway configuration), and a redesign of the VPN client interface to bring it more into line with the EDR interface.
- Perhaps creating a dedicated server agent with its own blades and operation would be more appropriate?
- What are the most urgent product improvements?
- Urgent optimization of resource utilization, whether on workstations or Windows servers. RAM and CPU usage is far too high. The forensics blade on more than 400 Windows servers was too greedy and random, several TAC cases and correction/configuration attempts with our local Check Point Team were unsuccessful, and the blade was uninstalled.
- Better separation of computer and server assets (Windows and Linux) in the reporting console.
- Easier management of devices to be authorized or prohibited.
Kind regards,
Gwendal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
our customer wants to be alerted about out of date clients. The provided alert functionality is more general and the possibility to customize the trigger points for the alerts is very limited.
Please allow cutomized trigger points for example:
- send an alert/report for all clients not connect for <x> days
- send an alert/report for all DAT files older than <x> days
- send an alert/report for all clients with no full scan in the last <x> days
Allow to choose a field out of the database and the timeframe for an alert.
Thank You
Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As far as I know, the 'Reuse Password' function checks password hashes to see if the user is using a corporate password on a site outside the organization. It would also be interesting to check if the email they use to log in to a site outside the organization belongs to the corporation's domain, indicating the use of Shadow IT.
- « Previous
-
- 1
- 2
- Next »
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 8 | |
| 4 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter