Hi all,
We are happy to announce the release of Endpoint Security Client E82.50.
E82.50 introduce new functionalities and quality improvements.
The complete list of improvements can be found in the version release’s Secure Knowledge sk165515
Dynamic Package Size
Follow up the improvement in agent package size which introduced in E81.10, the threat prevention package was reduced by >60% we are happy to introduce additional enhancement in SandBlast Agent package size optimization.
Dynamic Package enables optimized package size for Agent software updates.
The dynamic package contains only the delta incremental changes from the installed agent version and not the full package size. The result is much smaller package size needed for the agent upgrade which now reduced to ~160MB compared to ~680MB required for a complete package.
The new dynamic package will reduce network traffic and will enable faster agent upgrades.
This is very important in big organizations with thousands of deployed endpoints and specially today due to the COVID-19 virus where employees are working remotely, the dynamic package will assure safe and fast agent upgrades.
Additional information can be found in the administration guide
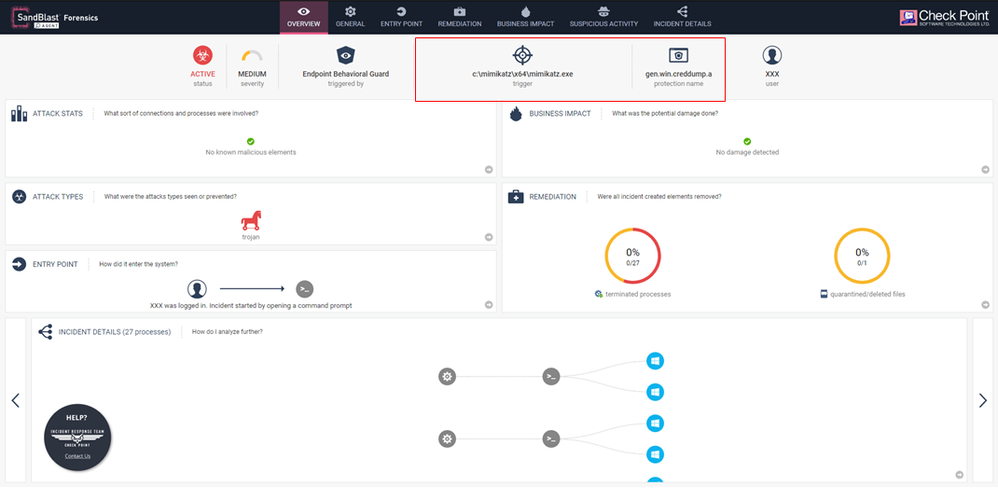
Credential Dumping Protection
Credential dumping is the process of obtaining account login and password information, normally in the form of a hash or a clear text password, from the operating system and software.
Credentials can then be used to perform Lateral Movement and access restricted information.
Behavioral Guard is now able to detect and prevent credential dumping.
Virtual Desktop Infrastructure (VDI) Non-Persistent for VMware Horizon – Early Availability
Virtual desktop infrastructure (VDI) is a virtualization technology that hosts a desktop operating system on a centralized server.
Non-persistent VDI creates a generic desktop that always reverts to the same original setup after a user logs out. Additionally a non-persistent desktop does not allow a user to install an application and retain it across logons.
We are looking for customers who would like to participate in the Early Availability version of the VDI non-persistent mode for VMware.
For customers who are interesting please contact E81_EA@checkpoint.com
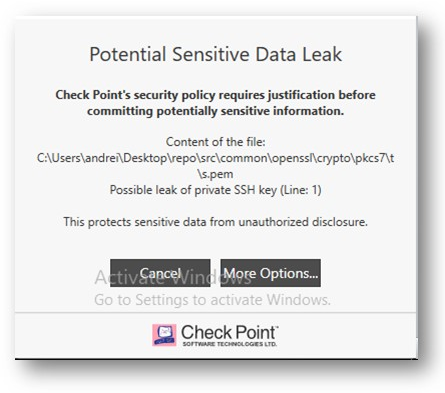
Developer Protection
Developer Protection is a new features in the Application Control blade which prevent leakage of sensitive information (RSA keys, passwords, access tokens) through Git version control system.
It also can warn user when vulnerable external dependencies are used in AWS lambda.
Developer Protection intercepts "git commit" commands issued by user and scan all modified files in a Git repository.
Additional information can be found in sk165615
Additional Enhancements
Threat prevention
- Forensics can now report the URL for the file source, when the SandBlast Agent Browser Extension is active.
- Machine type, roles and features now show in the Forensics report.
- Fixes a rare BSOD, related to Anti-Exploit infrastructure
- Reduces repeated logs for specific errors to improve Behavioral Guard performance.
- Adds a default exclusion to prevent a known case of an Anti-Ransomware false positive.
- Forensics and Anti-Exploit now correctly identify the latest versions of Microsoft Edge (based on Chromium) as a browser.
- SandBlast Agent browser extensions now report the URLs used to download files to Forensics. This information now displays in the Entry Point view in the Forensics report, when it is present.
- Fixes an issue where the Behavioral Guard log and the equivalent Forensics log show different levels of confidence.
- Fixes a rare race condition that can override the current Forensics policy with the default policy.
- Fixes an issue where Forensics generates "Analysis Failed" reports, when policy disables Forensics Analysis.
- Fixes an issue that can cause DNS sensor information to be withheld from Forensics.
- Fixes an issue in the Forensics report, where trigger processes incorrectly show as remotely executed by Windows Management Instrumentation (WMI).
- The Overview screen Entry Point tool-tip now displays correctly for Windows Management Instrumentation (WMI) executions.
- Adds the type of the machine to the General View of the Forensics Report. The type can be a desktop, a laptop, a Virtual Machine, or a server.
- Machines Roles and Features, as defined by Windows, are now available in the General view of the Forensics Report.
- The Reputation view in the Forensics report now has an option to select and copy Hashes, URLs and IPs.
- Resolves a possible issue, where the server does not display the latest Anti-Malware signature version of the Endpoint Security clients.
- Resolves an issue, where the policy state displays as "Unknown" in the client User Interface.
Data and Access Control
- Improves compatibility with 3rd-party VPN software.
- The firmware logo wallpaper now shows, when Windows loads after the Full Disk Encryption pre-boot.
- Fixes dual recovery file delivery on fresh installations, on UEFI machines.
- Resolves an issue, where allowed non-storage devices can show as blocked in SmartEndpoint Media Encryption and Port Protection reports.
- Resolves an issue, where the user does not see an option to override company encryption policy to copy data from network shared folders.
- Resolves an issue where the wrong authorization status shows in the Media Encryption UI.
- Resolves a possible system freeze from corrupted settings of the Media Encryption blade.
Installation & Infrastructure
- Resolves an issue, where the Endpoint Security installation may fail after a miscalculation of the required disk space.
- No longer displays a redundant user check pop-up on an installation retry.
- Resolves an issue, where the client may report logs incorrectly, if the username contains non-ANSI symbols.
- Resolves a rare issue with policy corruption that may put some blades in non-running states.
- Resolves an issue where the VPN client automatically reappears in Automatic Start, although it is disabled by the Task Manager.
- Fixes the vulnerability to "RobinHood" (CVE-2018-19320).
Best
AmiB




