- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Workspace
- :
- Endpoint
- :
- Re: EndPoint Security URL Filtering
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
EndPoint Security URL Filtering
URL Filtering for Endpoint Security. Presently this is how it's accomplished which is daunting and unmanageable when is this slated to be fixed:
Note: This procedure needs to be repeated after every URL filtering policy change.
Configuring URL Filtering - One-computer deployment
To prepare to deploy the URL Filtering blade as part of Endpoint Security clients:
- Install an R75.40 Security Gateway (R75.40 only). Can be a Virtual Machine.
Connect with SmartDashboard to the Security Management Server.
Open the R75.40 Security Gateway object properties.
Enable the URL Filtering blade - click on OK.
Go to the Application & URL Filtering tab - in the left tree, click on Policy - define the relevant rules.
Install the security policy on the R75.40 Security Gateway.
Connect to the command line on the Security Management Server.
Log in to the Expert mode.
Run one of these commands to fetch the URL Filtering into the Endpoint policy:
[Expert@HostName:0]# eps_policy_fetcher fetchlocal -g <Name of Security Gateway object>
For example,eps_policy_fetcher fetchlocal -g GW1[Expert@HostName:0]# eps_policy_fetcher fetchlocal -d $FWDIR/state/<Name of Security Gateway object>/FW1
For example,eps_policy_fetcher fetchlocal -d $FWDIR/state/GW1/FW1/
Connect with SmartEndpoint GUI to the Endpoint Security Server.
Go to the Policy tab.
In the URL Filtering rule, make sure that there is an indication that the Security Gateway policy is available for endpoints.
Example: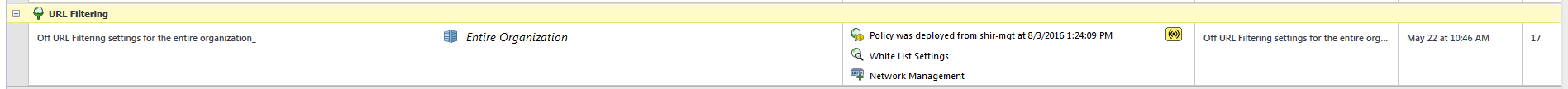
Configuring URL Filtering - Distributed deployment
To prepare to deploy the URL Filtering blade as part of Endpoint Security clients:
Connect with SmartDashboard to the Security Management Server.
Open the R75.40 Security Gateway object properties.
Note: Install an R75.40 Security Gateway (R75.40 only). Can be a Virtual Machine.Enable the URL Filtering blade - click on OK.
Go to the Application & URL Filtering tab - in the left tree, click on Policy - define the relevant rules.
Install the security policy on the R75.40 Security Gateway.
Copy all the files from the $FWDIR/state/<Name of Security Gateway object>/FW1/ directory on the Security Management Server to the $FWDIR/state/__tmp/FW1/directory on the Endpoint Security Management Server.
Important Note: If you copy these files via a Windows-based computer, then after transferring them to the Endpoint Security Management Server, it is necessary to run the following command:
dos2unix $FWDIR/state/__tmp/FW1/*Connect to the command line on the Endpoint Management Server.
Log in to the Expert mode.
Run the following command to fetch the URL Filtering into the Endpoint policy:
[Expert@HostName:0]# eps_policy_fetcher fetchlocal -d $FWDIR/state/__tmp/FW1Connect with SmartEndpoint GUI to the Endpoint Security Server.
Go to the Policy tab.
In the URL Filtering rule, make sure that there is an indication that the Security Gateway policy is available for endpoints.
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For that method, you MUST use R75.40 as this is the only compiled policy version that is supported.
The ISO can be found by enabling the check for unsupported versions after you've typed in your search terms.
That particular method was only in use by a handful of customers and has been deprecated in favor of Harmony Browse (formerly SandBlast Agent Plugin).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In addition to Phoneboy's comment above, we are now implementing a new URLF capabilities in Harmony Endpoint (former SandBlast Agent) Anti-bot blade.
By that, all Harmony Endpoint user will have URL Filtering functionality monitoring all the network traffic on the endpoint, working in full integration with the Harmony Browse browser extension.
Once we will do that, we will deprecate the old URL filtering solution based on R75.40 GW.
28 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One comment: the R75.40 gateway object needs to exist, but the R75.40 gateway itself need not be installed.
This just provides an acceptable target to compile the policy that is pushed to the Endpoint clients.
Either way, this does mean that you need to account for this dummy gateway object in your licensing (managed gateways).
If you exceed your licensed managed gateways as a result, your account team should be able to assist.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Still requires cli process also correct??
Thanks,
Juan Concepcion
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, the rest of the process is still required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Running R80.20 MGMT, R8020 GW and R8020EP
I am not sure if this is supported based on the SK and that I need to go back to R77.30.03 for GW and EP along with MGMT
I have created the dummy object in the R8020 MGMT for a R75.40 GW and everything works except for installation of policy as it is giving a error for not having a SIC. Since it is a dummy object, and not a GW setup, with could have us setup SIC during installation. What is the process or am I missing something?
The rest seems start forward except the create of the object or set up a R75.40 GW server itself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have to have to install a R75.40 gateway somewhere for this purpose.
It can be a VM and doesn't have to actually pass traffic.
That's indicated here: Installing and Configuring Endpoint Security URL Filtering
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is what I thought having read the Endpoint URL doc and SK article but your comment above made me second guess. Thanks for the clarification that it does need to be installed to push policy and fetch from.
***
One comment: the R75.40 gateway object needs to exist, but the R75.40 gateway itself need not be installed.
This just provides an acceptable target to compile the policy that is pushed to the Endpoint clients.
Either way, this does mean that you need to account for this dummy gateway object in your licensing (managed gateways).
If you exceed your licensed managed gateways as a result, your account team should be able to assist.
***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My previous understanding was incorrect.
Apologies for the confusion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have tried configuring and enabling the Endpoint URL Filtering policy using that SK article and also speaking with TAC, but it pretty much broke a lot of websites. As of now we have it disabled until this blade gets updated.
Has anyone been successful in enabling their URL Filtering policy?
I would also like to know when an updated release of the Endpoint URL Filtering will be.
Thank You
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Customer I was working with decided to route all traffic through gateway when folks were connected via VPN from a company asset.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes correct. To be affective of any feature like URL filtering, App control etc.. for remote VPN users, Traffic should route through Gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was able to configure as the process distribuited deployment and it works!! My schema it's Security Management-Network Gateway and Endpoint Management-Dummygateway. The only one issue I have is the licensing because of the dummy gateway. Does someone know how to solve it? Or it's mandatory to acquire a new license for this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A license is required for managing the dummy gateway, yes.
Your local office should be able to provide this at no cost.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you know if that should include the URL-Filtering license needed? Considering that it's just for install policies in dummy gateway and update database of URLs blocked on Endpoints.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For the dummy gateway, you can get the license for free. just contact your account manager/SE and they can provide it to you with no cost for this specific purpose.
but notice that the EP URLF itself is not part of the EP complete package and require a separate license.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot for your help, I will check internally with the pre-sales department for contacting the account manager/SE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great news Ricardo! What versions did you use for your successful deployment?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have Security Management R77.30.03, one dummy Security Gateway R75.40 version and endpoints E80.80 if I'm not wrong. I don't remember that exact version.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Awesome thanks Ricardo! Would you mind shooting me an email at eoakeson@checkpoint.com so I can discuss some details with you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure!
Best regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May I know if in the POC stage which one eval license can be used?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi DongYuan_Wu,
For URL Filtering license please open a ticket to the Solution Center.
Regards,
Doron Zuckerman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From what I gather from sk112932, the R75.40 gateway is no longer required for R80.20+ management, is this correct?
Is the same true for a Cloud Managment solution?
Thank you!
Steven.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately, this is incorrect.
I would like to clarify this in the SK. Can you please mention where was this explained in the SK?
Thanks,
Doron.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to clarify, there are now two methods for doing URL Filtering on Endpoint clients:
- Using the method described in sk112932 which requires a specific, non-pricelist SKU to utilize and does require configuring an R75.40 gateway. Only a small number of customers are using this.
- Using the plugins available from E83.20 Endpoint Security Client and managed by web management (either EPMaaS (Cloud) or R81 (on-prem)) that are included with all current SBA SKUs. This is the recommended approach for all customers moving forward. See also this thread: https://community.checkpoint.com/t5/SandBlast-Agent/URL-Filtering-with-Endpoint-Security-Only/m-p/81...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi PhoneBoy,
I've tried in a lab environment to use a R80.20 GW instead of R75.40 GW since I can't find the R75.40 ISO in order to create a VM.
Is this path feasible ? I can see the URLF policy in smartendpoint (I used sk112932).
Could you tell me if also this might be a good pathway?
Many thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For that method, you MUST use R75.40 as this is the only compiled policy version that is supported.
The ISO can be found by enabling the check for unsupported versions after you've typed in your search terms.
That particular method was only in use by a handful of customers and has been deprecated in favor of Harmony Browse (formerly SandBlast Agent Plugin).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many Thanks for your reply PhoneBoy, I appreciate.
Regards
Davide
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In addition to Phoneboy's comment above, we are now implementing a new URLF capabilities in Harmony Endpoint (former SandBlast Agent) Anti-bot blade.
By that, all Harmony Endpoint user will have URL Filtering functionality monitoring all the network traffic on the endpoint, working in full integration with the Harmony Browse browser extension.
Once we will do that, we will deprecate the old URL filtering solution based on R75.40 GW.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 3 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


