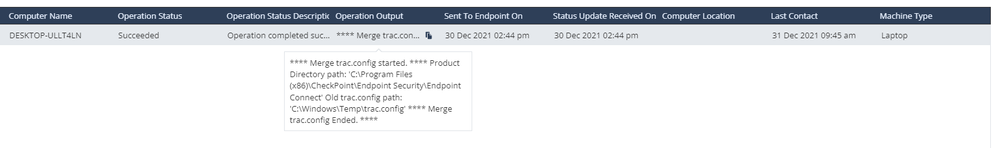
Of course, here's what I got. First image is the output of a successful operation. The push was done on Infinity Portal with a "Remote Command" operation.
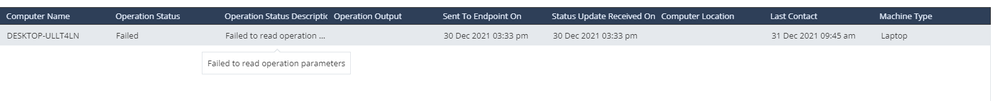
The second image is a Custom Push.
Here's the script I used, though I'm ommitting the contents of the "trac.config" file to save space.
Set-Service -Name TracSrvWrapper -StartupType disabled
Get-Service -Name TracSrvWrapper | Stop-Service
echo HereSitTheContentsOfTrac.Config | Out-File -FilePath c:\trac.config -Encoding default -NoNewline
attrib +A C:\trac.config
cp "C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Connect\trac.config" "C:\windows\temp\trac.config"
cp "C:\trac.config" "C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Connect\trac.config"
cd "C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Connect\" ; .\update_config_tool.exe "C:\Windows\Temp\trac.config" "C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Connect"
Set-Service -Name TracSrvWrapper -StartupType automatic
Get-Service -Name TracSrvWrapper | Start-Service
And here's the JSON I pushed through SmartEndpoint.
{
"Description": "Remote command push",
"Type": "powershellunsigned",
"Arguments": "",
"Parameters": "",
"Command": "T3V0LVN0cmluZyAtSW5wd=="
}The "Command" option was substituted with a base64 version of the script copied above, once again excluded to keep things down in size.
I got the base64 command by running, the operation was "type 109" as described by sk173414.
[Convert]::ToBase64String((gc C:\users\user.directory\Downloads\trac.ps1))
As far as restoring from quarantine goes, I performed the pushes through Infinity Portal, the file I was restoring was the EICAR test virus file, the original filepath of which was "C:\users\user.directory\Downloads\eicar.com".
I performed multiple restore operations using "C:\users\user.directory\Downloads\eicar.com" as the path, just "eicar.com" and finally "C:\ProgramData\CheckPoint\Endpoint Security\Anti-Malware\quarantine\b3c2adbc28791f0f.klq" as the paths.
In all cases the result was a successful push operation, however the status was always "0 files restored, 0 still infected, 1 files not found."
I'm really not clear which file location I should be specifying here. I'll open a case with TAC in case we don't figure something out within the context of checkmates, but I see quite a few forum posts asking vaguely the same sorts of questions regarding push operations; I think some more clarity with documentation might be nice.




