- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Share your Cyber Security Insights
On-Stage at CPX 2025
Simplifying Zero Trust Security
with Infinity Identity!
CheckMates Toolbox Contest 2024
Make Your Submission for a Chance to WIN up to $300 Gift Card!
CheckMates Go:
What's New in R82
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Harmony
- :
- Endpoint
- :
- Re: Change "Enable Always-Connect" always grey
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Change "Enable Always-Connect" always grey
Hi!
I have E82.40.
When trying to disable the "Enable Always-Connect" for users that are mostly at office I can't because it is always greyed.
Previously, I was able to change it.
Welll... It required to perform a connection first in order to the checkbox to appear selectable but now is always grey.
By default the "Enable Always-Connect" is checked and I need to uncheck. 🙂
How may I change it?
Best Regards,
Paulo Balau
17 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seems is very usefull for future deployments, indeed.
For the already installed/deployed how may I change it?
Best Regards,
Balau
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
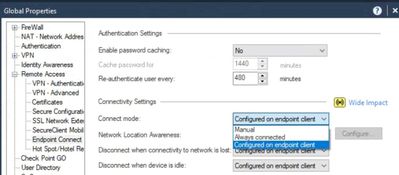
It's controlled via a Global Properties setting.
Change as appropriate and push Access Policy.
The existing clients should be updated once they connect again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, I have the same problem, but I can't find Global Properties. This is my screen. Is there any other option to disable the "Always Connect" check?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As an end user, if your admin does not allow you to configure this setting, you can not disable it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the quick reply. The only problem is that Check Point is installed in my personal computer. Is there any other way to prevent the software starts when I turn on my computer? I tried to uncheck it using Msconfig, but when I apply the changes, the check does not disappear
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This not allowing the client to be disabled behavior is likely part of our self-protection mechanisms.
Short of getting your admin to disable this option or to change to allow it to be configured on the client, your only option is to uninstall the client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello PhoneBoy...
I have it that way but is does not work as well. 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This Global Properties are not on the client itself but on the SmartConsole (were you define fw policies, etc, etc.)
One may say it could be useful to be on the SmarEndpoit console but it is not as well 😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi! I have it as you mentioned from start. But, even on recently updated Endpoint Security clients (as mine) continue to show the option on grey.
It seeams they do not care of this global option 😞
Any other way?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Edit the clients trac.defaults file in a text editor, see sk108982.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The only problem with this approach (and of course it is the prescribed approach) is the unfriendly nature of it. I have often wondered why, when using the full endpoint management server, that there isn't a better way.
In an enterprise estate, there are several user classes (sales, technical, accounts, executives), and these may require different VPN configurations. There is not a simple way to create a VPN policy for these user communities from the central management point, and that seems very strange. One size fits all does not work in large estates.
For example, in our own business - I want my sales team to have an always-on configuration. They need to connect if they are out of the office, so I want to give them a sales VPN profile (ideally with transparent machine authentication because they are sales people). But our technical teams need to log on to a completely different VPN gateway, but they are technical and they know when they need a VPN and when they don't. They have access to customer systems from the VPN, so 2-factor authentication is preferable.
These user groups have config needs that are completely different and whilst I can manage a user base with 2 or 3 different trac.defaults configurations across around 40 machines, it's clunky and for no good reason. @PhoneBoy it's time for EndPoint to grow up a little more and remember that unlike gateways, endpoints are managed by the desktop team where clunky fixes to text files that are not accessible via the management interface are a blocker to acceptability and ultimately to sales success. Engineers may love to hate the "just edit this file in vi" type of SK, but frankly it's a killer for most endpoint administrators and needs to evolve. Can it be in R81 endpoint management please ? 😄
Long term technology addict and occasional Check Point consultant.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81 is in Public EA now, so if that feature isn’t there already, it won’t be in R81.
Agree that editing manual files on a specific gateway is a less than optimal solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this setting available on the Harmony platform ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The reason this is not configured in Endpoint Management is because there are gateway-specific dependencies required to implement this feature.
As such, enabling in Endpoint Management without that configuration wouldn't be terribly useful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I edited trac.defaults with notepad.
Find line "neo_always_connected STRING true GW_USER 1" and change it from true to false and save file. It works for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The only simple solution, thanks.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 05 Nov 2024 @ 10:00 AM (CET)
EMEA CM LIVE: 30 Years for the CISSP certification - why it is still on topTue 05 Nov 2024 @ 05:00 PM (CET)
Americas CM LIVE: - 30 Years for the CISSP certification - why it is still on topThu 07 Nov 2024 @ 05:00 PM (CET)
What's New in CloudGuard - Priorities, Trends and Roadmap InnovationsTue 05 Nov 2024 @ 10:00 AM (CET)
EMEA CM LIVE: 30 Years for the CISSP certification - why it is still on topTue 05 Nov 2024 @ 05:00 PM (CET)
Americas CM LIVE: - 30 Years for the CISSP certification - why it is still on topTue 12 Nov 2024 @ 03:00 PM (AEDT)
No Suits, No Ties: From Calm to Chaos: the sudden impact of ransomware and its effects (APAC)Tue 12 Nov 2024 @ 10:00 AM (CET)
No Suits, No Ties: From Calm to Chaos: the sudden impact of ransomware and its effects (EMEA)Tue 19 Nov 2024 @ 12:00 PM (MST)
Salt Lake City: Infinity External Risk Management and Harmony SaaSWed 20 Nov 2024 @ 02:00 PM (MST)
Denver South: Infinity External Risk Management and Harmony SaaSAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter