- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CloudMates General
- :
- How to force MFA with Microsoft Authenticator toke...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to force MFA with Microsoft Authenticator token or code? (SAML + MFA MS Authenticator)
Hello everyone!
I hope you are all feeling great.
I am here to ask you about a requirement that a customer sent us some time ago.
The customer currently has a Remote Access VPN where they use mainly two authentication methods:
-They use local Check Point users for VPN authentication.
-They use LDAP On-Premises users (however, with this authentication method they have a problem: a user Example "John.Dao" exists in a LDAP of a branch and coincidentally there is another "John Dao" in another branch with another LDAP, which is a case that repeats itself a lot in their LDAP)
To solve this issue about duplicate users in LDAP, the customer asked us to make a roadmap to change this authentication method and use Microsoft Azure AD authentication (now called Microsoft Entra ID).
Here, each user will be signed in his own Microsoft Azure AD domain and will not have duplicity problems in different LDAPs.
I have created a lab with a SMS and GW on R81.20 with the latest patch and followed the step by step of this guide:
https://sc1.checkpoint.com/documents/R81.20/WebAdminGuides/EN/CP_R81.20_RemoteAccessVPN_AdminGuide/C...
Also, I followed this video:
https://www.youtube.com/watch?v=yZVB3sJ3fZ8
Basically I did the following:
1- Configure Remote Access VPN on the GW
2- Create a MS Entra ID application for user authorization (this app has read-only permissions to all users, groups and devices in the entire Microsoft Entra ID tree (aka Microsoft Azure AD).
3- Based on this MS Entra ID, create a Check Point object of type "Azure AD" and place the app data. This will allow the Check Point SMS to read the Microsoft Azure AD users.
4- Then, create another MS Entra ID application using a Check Point template located in the application marketplace. This app is called "Check Point Remote Secure Access VPN". With this application configure the data for SSO authentication with SAML.
5- Create a Check Point object of type "Identity Provider" and place the data of this application and with this I achieve the authentication of the users using the Azure AD credentials.
6- Generate a new authentication method, where select the Identity Provider object as authentication method and in "User Directories" check authentication with "External User Profiles".
7- Open Check Point SmartDashboard for Mobile Access and create a new External User Profile named "generic*".
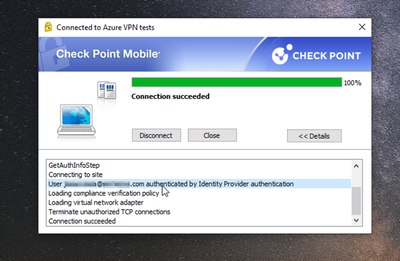
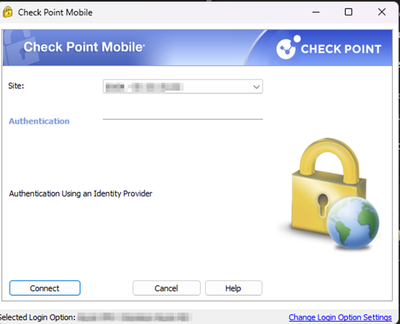
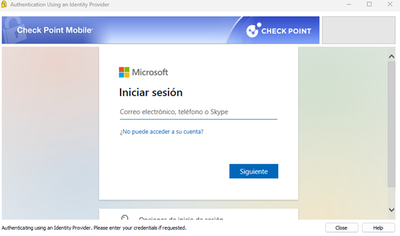
8- I installed policies and reach to authenticate using the Identity Provider information.
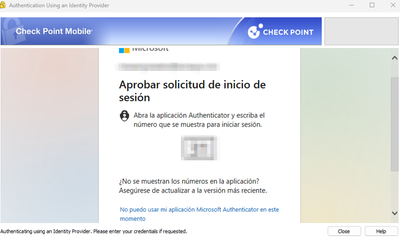
I add some captures of evidence:

At this point, everything is OK:
-The VPN client uses Azure AD for authentication and the problem of duplicate users in LDAP's on-premise is solved.
However, we have not yet complied with the requirement:
-Authentication must use Azure AD but in addition it must force the user to place the token shown in your Microsoft Authenticator application.
In other words, the VPN authentication must prompt the user for their Azure AD credentials and the user must also place the Microsoft token to fulfill a 2-factor authentication function.
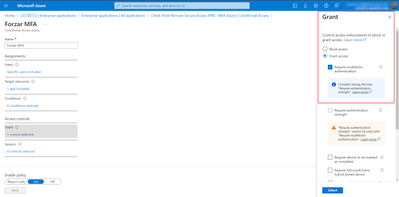
I have tried to force the MFA request for the end user through a "Conditional Access" rule applied directly in the MS Entra ID Application for Check Point authentication, which I show below:
However, this setting is not applied correctly or does not cause any effect.
I would like to know if there is a way to achieve this requirement: force the user to tokenize his MS Authenticator application and perform a 2FA authentication.
My theory is that the VPN client takes the credentials that live in the end user's PC settings (device registered in the Azure AD MDM) and that's why it doesn't ask for authentication again and doesn't even try to ask for a token for 2FA.
I know this may look like maybe some configuration on the Azure side but I would like to know what I could do in Azure or Check Point to accomplish this.
Greetings to all!
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please review the following SK and see if it assists with your scenario:
sk180948: SAML Force authentication every time for Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Chris_Atkinson,
Thank you very much, that was the solution!! 😀
I edit the configuration file referenced in the SK and after that, the goal is achieved: the end user is prompted for his 2FA credentials and token with Microsoft Authenticator every time the user logs in with his account.
I attach some evidence:
Thank you for your help.
Greetings!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please review the following SK and see if it assists with your scenario:
sk180948: SAML Force authentication every time for Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Chris_Atkinson,
Thank you very much, that was the solution!! 😀
I edit the configuration file referenced in the SK and after that, the goal is achieved: the end user is prompted for his 2FA credentials and token with Microsoft Authenticator every time the user logs in with his account.
I attach some evidence:
Thank you for your help.
Greetings!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I've followed the instructions and everything is working. However, if the user is already signed in to their Microsoft account in Microsoft Edge, it doesn't prompt for two-factor authentication on their phone.
If I change their default browser or sign them out of their Microsoft account in Edge, then everything works fine.
Can anyone test this and let me know if you're seeing the same behavior?
Edit:
Ive find out that if you wait 4 minutes or more it will ask the double authentification again. Ive wait 3 minutes and it did not ask me for double authentification so i guess Microsoft keep some info during 3 to 4 minutes before it asked again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Jean-Francois_G
I went through something similar in some tests I did some time ago: my PC was already authenticated and registered to the Microsoft business account (with my company account).
This caused that, every time I tried to authenticate with the Check Point VPN client, I was not asked for user credentials or token and the access was “direct”.
I think the VPN client was taking the authentication from my PC to the Microsoft account and maybe for that reason the VPN client was not asking for authentication again.
I solved this problem by applying the solution described in https://support.checkpoint.com/results/sk/sk180948
Basically, edit the values in the /opt/CPSamlPortal/phpincs/simplesamlphp/config/authsources.php file, as indicated in the solution.
My environment was R81.20, I don't remember what JHF I had but it was definitely a pre JHF 89.
*******
On the sk I see an update of May 20, 2025:
For R81.20 with Jumbo Hotfix Take 89 and higher and for R82, this solution has changed; see sk182042
What version and JHF do you have in your environment?
If it is equal or higher than R81.20 JHF 89 or R82, check sk182042.
Maybe this is the solution you need.
I hope I helped.
Greetings!!!