- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Who rated this post
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to force MFA with Microsoft Authenticator token or code? (SAML + MFA MS Authenticator)
Hello everyone!
I hope you are all feeling great.
I am here to ask you about a requirement that a customer sent us some time ago.
The customer currently has a Remote Access VPN where they use mainly two authentication methods:
-They use local Check Point users for VPN authentication.
-They use LDAP On-Premises users (however, with this authentication method they have a problem: a user Example "John.Dao" exists in a LDAP of a branch and coincidentally there is another "John Dao" in another branch with another LDAP, which is a case that repeats itself a lot in their LDAP)
To solve this issue about duplicate users in LDAP, the customer asked us to make a roadmap to change this authentication method and use Microsoft Azure AD authentication (now called Microsoft Entra ID).
Here, each user will be signed in his own Microsoft Azure AD domain and will not have duplicity problems in different LDAPs.
I have created a lab with a SMS and GW on R81.20 with the latest patch and followed the step by step of this guide:
https://sc1.checkpoint.com/documents/R81.20/WebAdminGuides/EN/CP_R81.20_RemoteAccessVPN_AdminGuide/C...
Also, I followed this video:
https://www.youtube.com/watch?v=yZVB3sJ3fZ8
Basically I did the following:
1- Configure Remote Access VPN on the GW
2- Create a MS Entra ID application for user authorization (this app has read-only permissions to all users, groups and devices in the entire Microsoft Entra ID tree (aka Microsoft Azure AD).
3- Based on this MS Entra ID, create a Check Point object of type "Azure AD" and place the app data. This will allow the Check Point SMS to read the Microsoft Azure AD users.
4- Then, create another MS Entra ID application using a Check Point template located in the application marketplace. This app is called "Check Point Remote Secure Access VPN". With this application configure the data for SSO authentication with SAML.
5- Create a Check Point object of type "Identity Provider" and place the data of this application and with this I achieve the authentication of the users using the Azure AD credentials.
6- Generate a new authentication method, where select the Identity Provider object as authentication method and in "User Directories" check authentication with "External User Profiles".
7- Open Check Point SmartDashboard for Mobile Access and create a new External User Profile named "generic*".
8- I installed policies and reach to authenticate using the Identity Provider information.
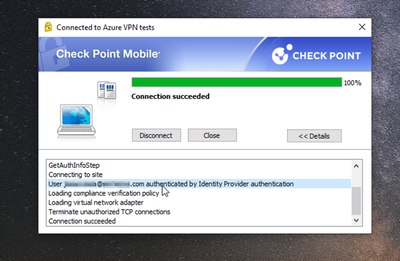
I add some captures of evidence:

At this point, everything is OK:
-The VPN client uses Azure AD for authentication and the problem of duplicate users in LDAP's on-premise is solved.
However, we have not yet complied with the requirement:
-Authentication must use Azure AD but in addition it must force the user to place the token shown in your Microsoft Authenticator application.
In other words, the VPN authentication must prompt the user for their Azure AD credentials and the user must also place the Microsoft token to fulfill a 2-factor authentication function.
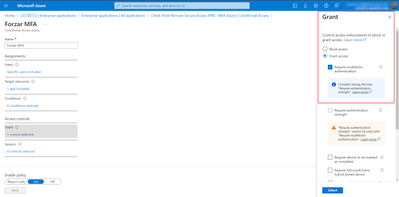
I have tried to force the MFA request for the end user through a "Conditional Access" rule applied directly in the MS Entra ID Application for Check Point authentication, which I show below:
However, this setting is not applied correctly or does not cause any effect.
I would like to know if there is a way to achieve this requirement: force the user to tokenize his MS Authenticator application and perform a 2FA authentication.
My theory is that the VPN client takes the credentials that live in the end user's PC settings (device registered in the Azure AD MDM) and that's why it doesn't ask for authentication again and doesn't even try to ask for a token for 2FA.
I know this may look like maybe some configuration on the Azure side but I would like to know what I could do in Azure or Check Point to accomplish this.
Greetings to all!
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter