- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: Static NAT in Azure Checkpoint
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Static NAT in Azure Checkpoint
Hi,
We have single checkpoint gateway installed in Azure environment. We want to do static NAT so that some IPs are publicly available but don't want to use gateway IP as a PAT.
I have attached one more IP to external interface of firewall which has public IP and followed steps given as below.
https://community.checkpoint.com/t5/CloudGuard-IaaS/STATIC-NAT-in-Azure-Checkpoint/td-p/75730
Done NAT configuration like below
Original source Original Dest Xlate source Xlate Des
Any 172.17.1.8 Any 172.17.7.24
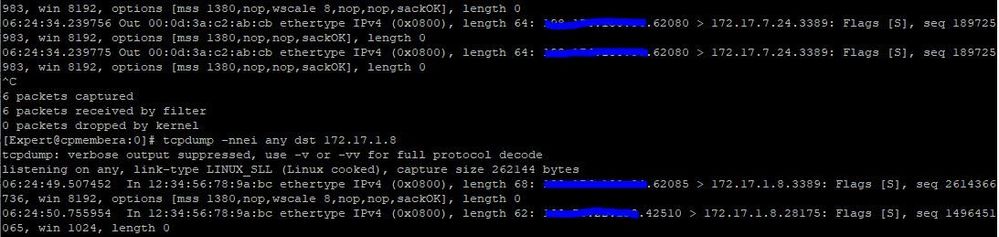
Please note that 172.17.1.8 has public IP and this NATing will be taken care by Azure. when I am trying to test traffic from outside, I am getting proper logs but not able to connect end machine 172.17.7.24. Please see logs.
Does anyone has any idea why it is not working. any setting is missing on firewall or azure side?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Gaurav_Pandya , if you have set up only a unidirectional manual NAT rules, it'll result in the behavior you are describing. Disable that rule and change the NAT properties of the object to configure static NAT.
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir.
Thanks for your response. I am doing manual NAT because I will map multiple IPs to public IP with different ports in future.
For testing purpose, I have done Object NAT as well but still it is not working. May be I am missing something on Azure side?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how is the NSG configured on the external side of the Check Point?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
Issue is resolved. There was no firewall configuration issue. It is the Azure security group which is blocking traffic. 😊
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Gaurav,
Am facing same issue.
Can you tell me what configuration you did the Security Group.
Regards,
Mitesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Mitesh,
You can define security group or ACL for each subnet in Azure, where you will define which source IP/subnet will access this subnet with particular port. So you need to open flow in security group or ACL as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Gaurav,
Thanks for the reply.
Just want to confirm, post assigning secondary interface to Checkpoint VM in Azure portal. Does we have attach secondary interface in Checkpoint topology as a external interface.
Regards,
Mitesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No. You do not need to add anything on Checkpoint except required NAT rule and policy.
Please note that we are using single gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Gaurav,
Am new in Azure.
We have deployed Checkpoint in Standalone mode.
Recently we added secondary ip address to Checkpoint External Interface.
| Private IP | Public IP | |
| Primary | 10.10.10.2 | 2.2.2.2 |
| Secondary | 10.10.10.3 | 3.3.3.3 |
Internal Server IP = 10.10.20.100
Our Requirement:-
We want to do Static NAT using Secondary Public IP. For that we created NAT & Firewall Policy as below.
Nat Policy:-
| Original Src | Original Dst | Original Service | Translated Src | Translated Dst | Translated Service |
| Any | 10.10.10.3 | Any | Original | 10.10.20.100 | Any |
| 10.10.20.100 | Any | Any | 10.10.10.3 | Original | Any |
Firewall Policy:-
| Source | Destination | Service | Action |
| Any | 3.3.3.3 | Any | Accept |
| 10.10.10.3 |
Hope till now am on right track.
Can you tell me what configuration needs to be done in Azure side.
Regards,
Mitesh Nandu