- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: Need help with CloudGuard remote access VPN on...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Solved: Need help with CloudGuard remote access VPN on Azure
I have a CloudGuard HA and management and my problem is remote access VPN is disconnecting roughly every 30 seconds. In the logs I can see "According to the policy the packet should not have been decrypted" is the reason tunnel test is being dropped.
Setup
- Frontend subnet has NSG allowing all inbound and outbound traffic
- image is R81.10
- frontend eth0 leads to "external"
- backend eth1 leads to "this network"
- office mode configured (10.255.255.0/24)
- remote access vpn domain does not contain office mode range
- anti-spoofing is off on both eth0 and eth1
- vpn link selection is statically NAT'd IP: public cluster VIP
- outgoing VPN link is private cluster VIP
Things I tried:
- Adding NAT rule as in sk106853 to translate tunnel test traffic to the public VIP to LocalGatewayExternal
- Adding policy rule as in sk44075 to accept tunnel test mapped to LocalGatewayExternal
- Modified (2) to also accept tunnel test to the public VIP
- Turned on anti-spoofing for office mode as in sk44075. Anti-spoofing for eth0 and eth1 still off
- Verified "accept control connections" and "accept remote access control connections" are checked
Solved: The public VIP has to be added to the remote access encryption domain. The other stuff in the "Things I tried" section are not needed except to make sure the implied rules in (5) are selected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @RickyDan i think the issue could be using the office mode configured (10.255.255.0/24). Try using another subnet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Changed it to 10.10.10.0/24 and it did not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
what did you choose under "VPN Link Selection" ?
it should be "NATTED IP" with the Public IP of your CLUSTER VIP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi, yes that is how it is configured. forgot to put that in the post. the outgoing link is set as the private VIP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it need to be the Public VIP , not the private VIP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
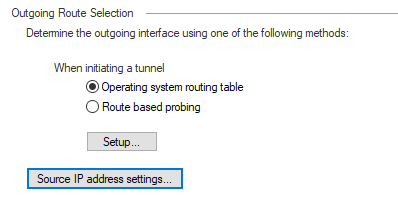
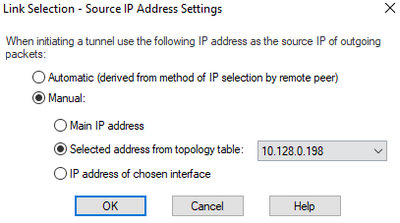
hi, these are the current config for outgoing route selection. what do you recommend?
outgoing route selection:
setup:
source ip address setting:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the outgoing is ok.
under the IPSEC VPN in the GW properties there's VPN LINK SELECTION.
what did you choose there ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
that is set to statically NAT'd IP: public cluster VIP