- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- Cloud Firewall
- :
- Discussion
- :
- Re: CloudGuard Connect SSL Error Azure
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CloudGuard Connect SSL Error Azure
Hi,
we sometimes see connecting errors from the CloudGuard Controller to Azure and it seems to be an SSL issue.
According zu https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...it is an HTTPS Inspection issue but we have no https inspection in place.
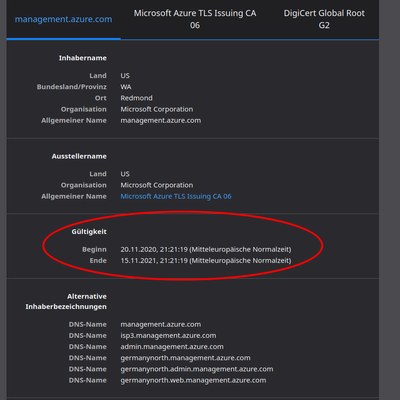
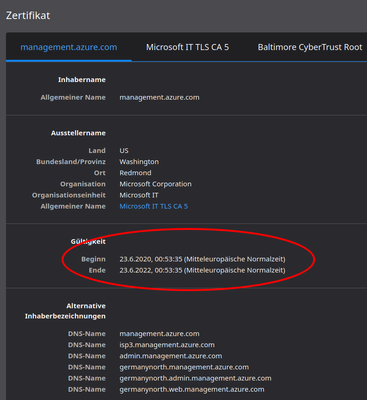
So we assume it is because sometimes https://management.azure.com replies with a new cert from the 20th of Nov.
Can someone confirm and how we can fix this?
Kind Regards,
David
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fix is now available, and is documented in sk170660 - Authentication failure to Microsoft Azure for Check Point CloudGuard Controller, CME and Check Point HA gateways.
You will need to contact support to receive an updated SSL certificate bundle, together with instructions how to deploy it on your SmartCenter/MDS or HA Gateways.
Once you deploy an updated certificate bundle, and verify that you've installed it correctly, you will need to restart the services:
- Smart Center/MDS- CME:
- Test cme service by running service cme test and see if connection succeeds. If not a restart cme is needed. to restart cme run the command: service cme restart - Smart Center/MDS- DataCenter objects:
- Test connection and see if connection succeeds. If not a restart controller is needed. Command: vsec_controller_stop; vsec_controller_start - HA or Cluster Gateway:
- no restart of services required. Confirm with running the command azure_ta_test.py
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.40 Jumbo T172:
UPDATE: Previously, because of connectivity issues with Azure, CloudGuard Controller was deleting IP addresses of Data Center objects from the Security Gateway. CloudGuard Controller will now show an error message instead of revoking identities from the Security Gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If it were HTTPS Inspection you wouldn’t see Microsoft as the certificate signer.
That said maybe they’re using a different CA than we have in the certificate store used by the CloudGuard Controller.
Recommend a recommend a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi PhoneBoy we are looking into a similar Azure deployment using Cloudguard Controller, but isn't there a better design that would prevent a Azure connectivity issue resulting in rule mismatching on the gateways, that would be a huge Single Point of Failure (SPOF). What would be your recommendation, is there a way to cache this "identities" on the gateway to prevent rule mismatching for some hours? Should I open another feed on this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.40 Jumbo T172:
UPDATE: Previously, because of connectivity issues with Azure, CloudGuard Controller was deleting IP addresses of Data Center objects from the Security Gateway. CloudGuard Controller will now show an error message instead of revoking identities from the Security Gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great! And is this behavior fix embedded in R81.10 by default? So, it basically means that identities will not be cleared when datacenter connection is lost, how long will these identities remain on the gateway, would that be unlimited until datacenter connection is restored?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's available in JHF T75 (ongoing) for R81.10.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We actually do cache things locally for a period of time.
If I'm understanding this SK correctly, it should be 72 hours.
Looks like you can configure the cache and other things as described here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Commencing November 20th in various regions, Microsoft deployed a new SSL certificate that is causing Check Point CloudGuard Controller to not able to authenticate to the Azure environment.
This will impact all customers who are using Cloud Objects that are learned from Microsoft Azure.
Symptoms:
- Microsoft DataCenter object is unable to communicate to Azure in Smart Console.
- Cloud_proxy.elg logs show o rest.CurlException: b'curl: (60) SSL certificate problem: unable to get local issuer certificate\nMore details here: https://curl.haxx.se/docs/sslcerts.html\n\ncurl failed to verify the legitimacy of the server and therefore could not\nestablish a secure connection to it. To learn more about this situation and\nhow to fix it, please visit the web page mentioned above.\n'
- DataCenter objects are no longer being populated on the gateway or in the rule base
- Connections that used to match a rule that used DataCenter objects now being dropped on the cleanup rule.
- PDP is not showing any DataCenter learned objects.
Solution:
Check Point R&D is currently working closely with Microsoft on a fix. We expect a fix in a way of a hotfix, shortly. Please open a TAC case or in case of Diamond Services, please contact your Diamond engineer, if you would like to be notified of a solution once it is available.
Caution:
Do not reboot the Check Point Management station or gateways if they are experiencing this issue. This will lose all learned Cloud objects from Azure Datacenter and there is no way to recover this until the communication issue has been resolved.
Reference SK:
sk169983: Microsoft Azure: Action required: Review your Azure Services Certificate Authorities
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A fix is being validated and will be shared with Check Point Support. Customers with this issue can contact Support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fix is now available, and is documented in sk170660 - Authentication failure to Microsoft Azure for Check Point CloudGuard Controller, CME and Check Point HA gateways.
You will need to contact support to receive an updated SSL certificate bundle, together with instructions how to deploy it on your SmartCenter/MDS or HA Gateways.
Once you deploy an updated certificate bundle, and verify that you've installed it correctly, you will need to restart the services:
- Smart Center/MDS- CME:
- Test cme service by running service cme test and see if connection succeeds. If not a restart cme is needed. to restart cme run the command: service cme restart - Smart Center/MDS- DataCenter objects:
- Test connection and see if connection succeeds. If not a restart controller is needed. Command: vsec_controller_stop; vsec_controller_start - HA or Cluster Gateway:
- no restart of services required. Confirm with running the command azure_ta_test.py