- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: CheckPoint R80.40 FQDNs filtering
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CheckPoint R80.40 FQDNs filtering
Hi CheckMates,
My organization is looking at deploying CheckPoint HA cluster R80.40 in Azure to replace Azure firewall.
One of our requirements for the Checkpoint gateways in Azure is to be able to do URLs/FQDNs filtering.
The current state of our environment in Azure:
- The web based traffic in Azure use the on-prem web proxies, and then traffic get routed out via on-prem gateways to the Internet.
- The non-web based traffic send the traffic to the Microsoft Azure Internet link directly. These are Microsoft services, updates, etc traffic. This is the bit that we want to filter. The requirement is to allow only HTTPS traffic to a small set of URLs (Microsoft services) and block the rest. Examples of the current rules in the Azure firewall is attached.
I’ve done some reading on how to do this in CheckPoint. It looks like you would do it using Domain objects? And to be able to do the URL filtering using wildcard to also match the subdomains you would use Non-FQDN Domain objects. However, it appears that:
- Non-FQDN Domain objects must have DNS reverse lookup entry
- Non-FQDN Domain objects affect the gateways performance greatly since it’s doing the DNS reverse lookup for every packet the hit the rules– is this only pre-R80.10 or also for R80.10 and above?
Could anyone please help clarify no. 1 and 2 above if my understandings are correct?
Also I’d like to know if Domain objects are the way to achieve what we need to filter the URLs, or if there are any other (better) ways to do this in CheckPoint? As not all non-FQDN domain objects have DNS reverse lookup entry and this would cause the gateways to drop the traffic.
Any help here is appreciated.
My references: sk120633, sk90401, sk155592
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
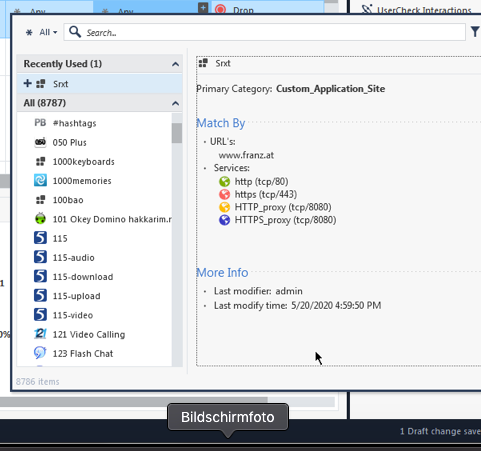
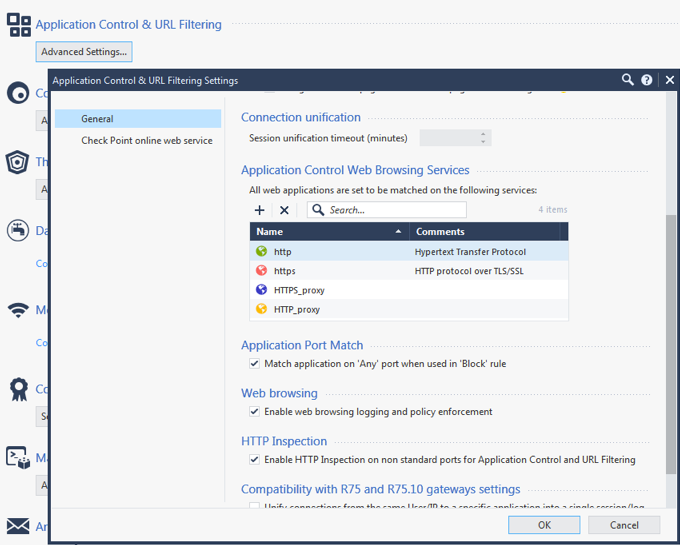
See the screenshots:
See the services ? If you want to change them, you have to change them for the Blade:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
They probably won't work in this case as I doubt these sites will reverse-resolve in the right way.
What you should do is create a Custom Applications/Sites for these domains.
This should work because the traffic is HTTPS and R80.40 has support for filtering based on Verified SNI.
This will require enabling App Control if it's not already enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the recommendation.
I've enabled both application control and URL filtering blades, and created a Custom Application/Site , however I couldn't figure out how to specify that it should only allow HTTPS (TCP/443) traffic.
There's no option to do this (configure a service) within the Custom Application/Site object itself.
Any ideas how to do this? Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
See the screenshots:
See the services ? If you want to change them, you have to change them for the Blade: