- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: BGP configuration for Expressroute
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
BGP configuration for Expressroute
Looking for advice on BGP configuration on checkpoint for Azure ExpressRoute, we are using two checkpoint devices and it is working as a cluster
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
With or without VPN and are there specific elements of the config that you need help with or all of it?
Note the BGP Router-ID needs to be configured with the same value on both cluster members, also Graceful restart is recommended.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Chis for your quick response.
I am looking for complete steps, it is without VPN.
Some of the points I have noted. RID should be the VIP and configure eBGP multi-hop option and define the TTL value...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For those reading and able to offer assistance, which side of the connection are the Check Point gateways located: on-prem | cloud | both ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chris,
Gateway is located on-prem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have customer using exact this setup and has been working for 2 years without issues. I can give you some screenshots of how its configured, will just need to blur out the sensitive info.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Rock,
Could you please share the screenshots, if possible. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will see what I can send tomorrow.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Heya @HBK
I had a quick look at customer's config and honestly, as I thought, there is no special instructions we followed, its literally from the link I gave you, so I am sure screenshots wont help. You just need to make sure that BGP peer settings match on the other side and then verify by running show bgp commands in clish what the state is. IF you cant get it going, you can run zdebug for affected peer IP and port 179.
If you need help, let me know, happy to do remote.
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Btw, to add to my previous response, we never really followed any special steps, simply whats outlined below and it worked fine.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We will be considering an ER backup link as well to Azure through BGP. AS number is the same, but we will be having 2 connections to Azure, so how it would be the configuration in this scenario?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Should not be a problem and worked well; I configured at least couple scenarios with Express route and DX connectivity with AWS. Yes BGP listens on cluster interface. You need to define a rule specifically open port 179 and this needs to be added above stealth rule. You can can define neighbor IPs though in rule base. And then you will have to add inbound route-filter else CP will not accept and install routes.
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Blason,
Thank you very much for your response.
If you don't mind, can I have the relevant screenshots for the same?
The second peer details also we will mentioned in the peer group as a secondary IP ?
what about the peer IP in the CP side, since the CPs are clustered we have to use the VIP as peer IP right.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is the config - This should give you hint. As I said before ensure to add a rule above stealth rule where source is your Peer IP and destination is your Cluster Object and port is TCP/179
I enabled ECMP here; it may or may not needed in your scenario
set bgp ecmp on
set bgp external remote-as 97xxx on
set bgp external remote-as 97xxx import-routemap "ACCEPTAWSDX" preference 10 on
set bgp external remote-as 97xxx peer 172.43.xx.xx on
set bgp external remote-as 97xxx peer 172.43.xx.xx holdtime 15
set bgp external remote-as 97xxx peer 172.43.xx.xx keepalive 5
set bgp external remote-as 65001 on
set bgp external remote-as 65001 peer 192.168.xx.xx on
set bgp external remote-as 65001 peer 192.168.xx.xx allowas-in-count 5
set bgp external remote-as 65001 peer 192.168.xx.xx holdtime 15
set bgp external remote-as 65001 peer 192.168.xx.xx keepalive 5
set route-redistribution to bgp-as 97xxx from static-route 10.30.10.0/28 on
set route-redistribution to bgp-as 97xxx from static-route 172.16.0.0/12 on
set route-redistribution to bgp-as 97xxx from static-route 192.168.0.0/16 on
set route-redistribution to bgp-as 65001 from static-route 10.30.10.0/28 on
set route-redistribution to bgp-as 65001 from static-route 172.16.0.0/12 on
set route-redistribution to bgp-as 65001 from static-route 192.168.0.0/16 on
set routemap ACCEPTAWSDX id 10 on
set routemap ACCEPTAWSDX id 10 allow
set routemap ACCEPTAWSDX id 10 match network 10.100.0.0/16 exact
set routemap ACCEPTAWSDX id 30 on
set routemap ACCEPTAWSDX id 30 allow
set routemap ACCEPTAWSDX id 30 match network 10.120.10.0/24 exact
set routemap ACCEPTAWSDX id 35 on
set routemap ACCEPTAWSDX id 35 allow
set routemap ACCEPTAWSDX id 35 match network 10.120.11.0/24 exact
set routemap ACCEPTAWSDX id 50 on
set routemap ACCEPTAWSDX id 50 restrict
set inbound-route-filter bgp-policy 512 based-on-as as 97xxx on
set inbound-route-filter bgp-policy 512 accept-all-ipv4
set inbound-route-filter bgp-policy 516 based-on-as as 65001 on
set inbound-route-filter bgp-policy 516 accept-all-ipv4
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Blason,
Thank you very much for sharing the configurations.
Currently we are not enabling ECMP and the second link will only for the redundancy if incase of any failure.
As i mentioned in the previous chat, still i have confussion about RID which IP should we need to define, I saw in many post, if the CPs are clusterd the RID must be VIP, in my sceanario i will be having two VIPs. In addition the back up peer ip details where should i need to define. If you will be able to share screen shot, it would be much appreciated.
In cisco I know that, we can create one loop and define the update source as loop back interface, it is bit easy.
Thanks,
to
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I also have some examples if needed.
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can, but it all depends what part specifically you need? Prefix-list, routemaps?
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
As I mentioned in the previous conversation, which IP should be my RID? can I create a loopback and assign the loop back as RID?
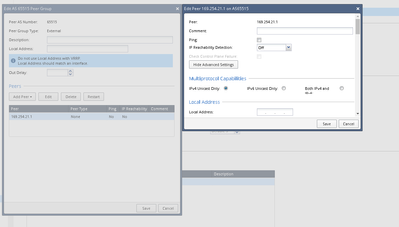
Since we have two IP for peering where should I need to add the secondary IP? Advanced routing-> BGP-> under the peer group -> add both peer IPs its it right way ? Screenshot attached.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You dont assign loopback IP to anything here at all. Just follow below section, it explains it there.
Andy
Here is an example from my lab:
[Expert@quantum-firewall:0]# clish
quantum-firewall> show bgp summary
Routing Process BGP
State is on
Local Autonomous System is 65514
Default Weight is 0
IPv4 BGP Route Rank is 170
IPv6 BGP Route Rank is 170
ECMP is off
IGP Synchronization is off
quantum-firewall> show bgp peers
Flags: R - Peer restarted, W - Waiting for End-Of-RIB from Peer
PeerID AS Routes ActRts State InUpds OutUpds Uptime
169.254.21.1 65515 0 0 Active 0 0 00:00:00
quantum-firewall> show bgp
errors - Show error notifications received from BGP peers
groups - Show summary of all BGP peer groups
memory - Show detailed breakdown of BGP memory usage
paths - Show summary of all AS paths stored by BGP
peer - Show information for a BGP peer
peers - Show all BGP peers
routemap - Show import and export Route Maps per peer group
stats - Show BGP statistics
summary - Show summary of BGP information
quantum-firewall> show bgp stats
Peer: 169.254.21.1
Received Sent
Opens 1 1
Notifications 0 1
Updates 0 0
Keepalives 6471 5673
Route Refresh 0 0
quantum-firewall>
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @the_rock ,
I have follow up question on this setup. So I was reading Microsoft document and it send Peer should have : "
- You must use a unique /29 (IPv4) or /125 (IPv6) subnet or two /30 (IPv4) or /126 (IPv6) subnets to set up the BGP peering for each peering per ExpressRoute circuit, if you have more than one."
Here Peer is 2 9200 cluster checkpoint on prem and we connecting Express route LAyer2 via Lumen as service provider.
I am running out of IP's for my VIP of the interface since i can only use /30. Am I missing something here or may i know what interface config on CP did you use?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just used any available IP from 169.254.10.x/24 subnet. Or, you can download config file from Azure portal and see whats being used.
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok perfect , thank you.. I will do that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me know if any issues, I can refer to lab config again.
Andy