- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Check Point
for Beginners
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Educational Resources
- :
- Check Point for Beginners
- :
- SMP 1500 appliance VPN setup with an Externally Ma...
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
OPEN OTHER ARTICLES
 How To Deploy 1550 SMB Appliance Using Zero Touch Cloud Service
How To Deploy 1550 SMB Appliance Using Zero Touch Cloud Service
 Jump Start: SMB Appliance Network Security - free online course
Jump Start: SMB Appliance Network Security - free online course
 Check Point 1500 Appliances - Reviewer Guide
Check Point 1500 Appliances - Reviewer Guide
 Check Point Security Management Portal - Reviewer Guide
Check Point Security Management Portal - Reviewer Guide
 Video - Learn Zero Touch Deployment with Quantum Spark In 10 Minutes
Video - Learn Zero Touch Deployment with Quantum Spark In 10 Minutes
 Video - Getting Started with Quantum Spark 1800 Series; Unboxing + 1st Time Wizard
Video - Getting Started with Quantum Spark 1800 Series; Unboxing + 1st Time Wizard
 Video - Firmware Upgrade on Quantum Spark In Less Than 3 Minutes
Video - Firmware Upgrade on Quantum Spark In Less Than 3 Minutes
 Video - Check Point Quantum Spark 1590: Unboxing, Initial Configuration and Watch Tower App
Video - Check Point Quantum Spark 1590: Unboxing, Initial Configuration and Watch Tower App
 Video - Setting up a Check Point 1590 Quantum Spark SMB Firewall
Video - Setting up a Check Point 1590 Quantum Spark SMB Firewall
 Video - How to use Check Point Zero Touch with Quantum Spark SMB appliance
Video - How to use Check Point Zero Touch with Quantum Spark SMB appliance
 Video - Check Point Remote Access VPN Setup and Configuration for Quantum Spark 1590 SMB Firewall
Video - Check Point Remote Access VPN Setup and Configuration for Quantum Spark 1590 SMB Firewall
 Video - Check Point Quantum Spark 1590 Site to Site VPN with Ubiquiti UDM Pro
Video - Check Point Quantum Spark 1590 Site to Site VPN with Ubiquiti UDM Pro
 Video - First look at the Check Point Quantum Spark 1600 Firewall
Video - First look at the Check Point Quantum Spark 1600 Firewall
 Video - Unboxing of Check Point Quantum Spark 1800 Firewall
Video - Unboxing of Check Point Quantum Spark 1800 Firewall
 Video - Block internet access to a client on Quantum Spark 1590 SMB Firewall + URL Filtering
Video - Block internet access to a client on Quantum Spark 1590 SMB Firewall + URL Filtering
 Video - Firmware Upgrade on Check Point Quantum Spark 1590 SMB appliance in less than 3 Minutes
Video - Firmware Upgrade on Check Point Quantum Spark 1590 SMB appliance in less than 3 Minutes
 Video - Configuring high availability on Check Point Quantum Spark Next-Gen Firewalls
Video - Configuring high availability on Check Point Quantum Spark Next-Gen Firewalls
 Check Point Jump Start: Quantum Spark
Check Point Jump Start: Quantum Spark
 SMB Security
SMB Security
PREVIOUS ARTICLE
TO READ THE FULL POST
it's simple and free
NEXT ARTICLE
SMP 1500 appliance VPN setup with an Externally Managed Gateway
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2020-07-09
04:12 AM
Author @Julie_Paul
Introduction
This document is instructions to setup a 1500 Appliance managed by an SMP plan in a Star VPN setup with an externally managed gateway a that is R80.x or higher.
Setup:
- Security Management Server(SMS) at R80.40, latest JHF
- 6500 Appliance managed by SMS, also at R80.40
- Security Management Portal (SMP) configured
- 1500 appliance managed by SMP portal at latest firmware version
- Plan is created and applied to the 1500 Appliance
Assumptions
- NAT is not being utilized or needed in this example, as every network behind each gateway is unique.
- You have access to both the Security Management Portal and the Security Management Server
SMP Portal Steps
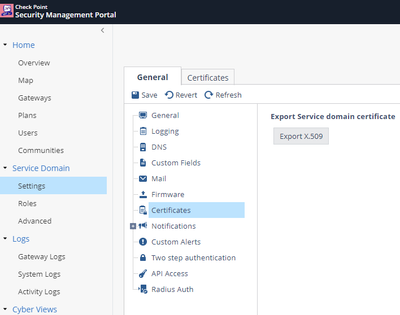
- Export SMP Certificate
- Logon to the SMP portal, go to Service Domain – Settings—in the General section select Certificates
- Click export X.509 and save to your desktop
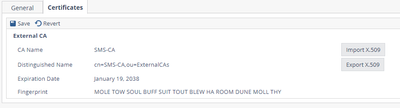
- Import SMS Certificate. (See step 1 in the SMS section on how to get the Certificate)
- Click on the Certificates Tab
- Click Add
- Enter a name, in this example we will call it SMS-CA
- Click Import X.509, select the internal_ca.crt file downloaded from the SMS. Click Save
- Click on the Certificates Tab
- Retrieve DN for the gateway on the SMP portal
- Select Gateways and click on the gateway to be in the VPN, in this example it is lab02-gw
- Click on VPN – Authentication Method
- Highlight the Distinguished Name and click copy, save this to a notepad for use in the SMS portal
- Create a new gateway to represent the externally managed gateway
- Select Gateways under the Home Section – click New
- Leave the Type as the default of Small Office Appliance
- Enter the name of the External gateway, in this example it is Spock
- Uncheck “Managed by SMP”
- Enter in the Static IP of the external interface, Click Finish
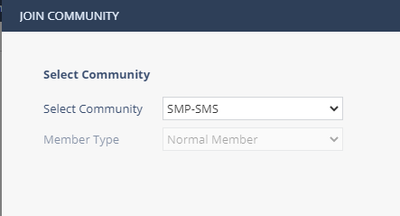
- Create a VPN Community
- Select Communities under the Home Section, Click New
- Enter in a name—we will use SMP-SMS in this example
- Description is optional
- Click Ok
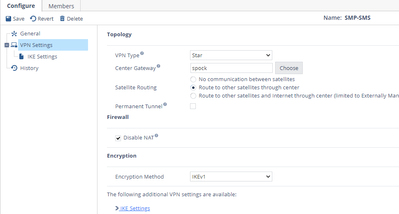
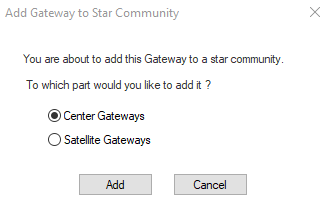
- Click on VPN Settings—Select VPN type to Star
- Set the Center Gateway to the spock object just created in step 4
- Change Satellite Routing to the option that works for you, we will use “Route to other satellites through center”
- Click Save
- Set the VPN Community
- Under the Home go to the Plan Section
- Open the plan in use in this example we are using the Plan-MSP-1500
- Select VPN – Community, use the drop down and select the VPN community you just created in Step 5 SMP-SMS
- Click Finish — then click Save
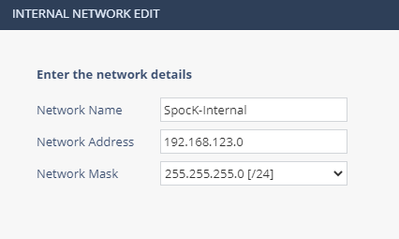
- Setup internal Topology for External Gateway in the SMP
- Under Home – Gateways edit the External Gateway we created in Step 4 Spock
- Click VPN – Internal Network Topology
- Under the Manually configured Networks—click New
- Enter in a name, in our example use Spock-Internal
- Enter in the Internal Network and Network mask
- Click Finish -- then click Save
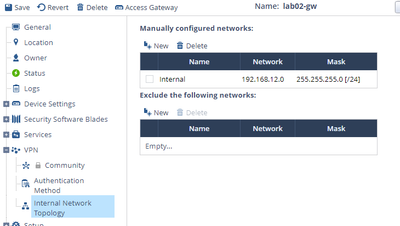
- Setup Internal Topology for the Internal Gateway lab02-gw
- Under Home – Gateways – Edit lab02-gw
- Click on VPN – Internal Network Topology
- Click New under the Manually configured networks
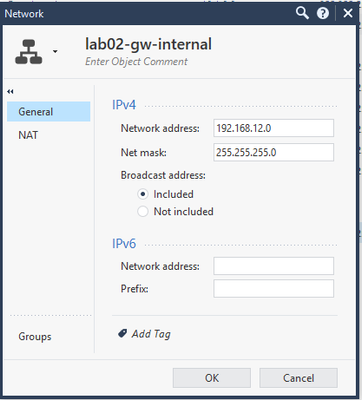
- Add the internal network, in this example it is 192.168.12.0/24, click Finish & Save
SMS Portal Steps
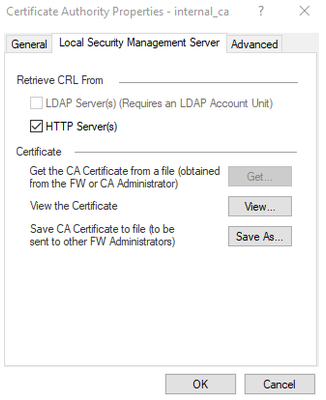
- Export the Certificate for use in the SMP portal
- Open Object Explorer, search for the internal_ca, open the object
- Click Local Security Management Server Tab
- Click Save As, save to your desktop, close the object
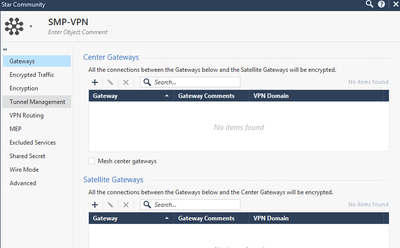
- Create a new VPN Community called SMP-VPN
- Open Object Explorer, Click New VPN Community --> Star Community
- Add the name SMP-VPN in this example
- Click on Advanced, Select “Disable NAT inside the VPN community”
- Click OK to accept the new object
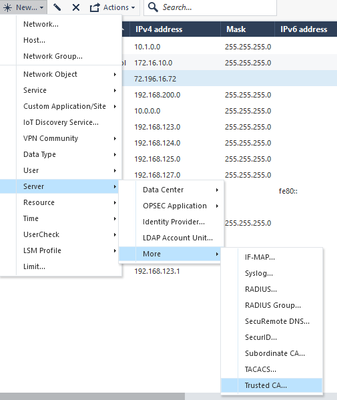
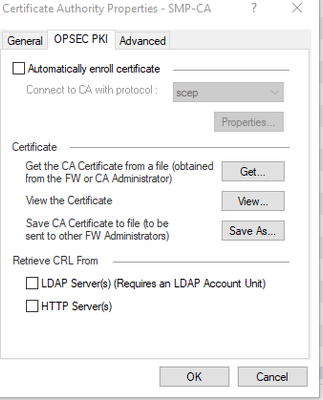
- Create a Trusted CA—called SMP-CA
- Open Object Explorer, Click Add New Server --> More --> Trusted CA…
- Enter the name SMP-CA
- Click on OPSEC PKI, click Get, select the SMP cert you extracted in step 1 under the SMP Section.
- In the Retrieve CRL From section, uncheck HTTP Servers (s)
- Open Object Explorer, Click Add New Server --> More --> Trusted CA…
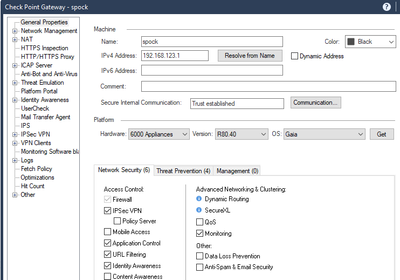
- Enable IPSEC VPN on the Gateway
- In this example we are using the Gateway Spock
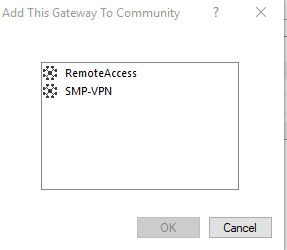
NOTE: In this example, the Main IP for Spock is internal 192.168 x address - Go to the IPSEC vpn option in the Gateway Spock, Click Add select the new VPN community we created in step 2 SMP-VPN, click OK.
- Select Center Gateways, as this will be the center of our Star VPN, click Add
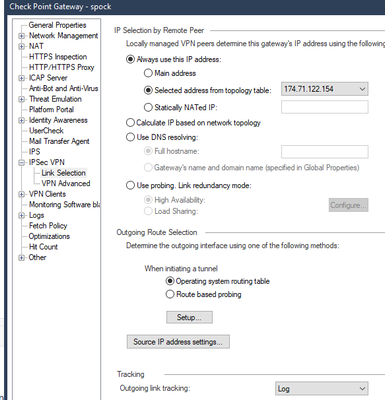
- Click on Link Selection,
- Under the “Always use this IP address” section
NOTE: Default is to use the Main IP address. In this scenario, the main IP is a 192.168 x address. We need to use external IP or VIP if a cluster. This will be the IP address used for VPN communication to the SMP device. - Select the option “Selected Address from topology table”.
- Click the drop down option and select the external IP or VIP if a cluster.
- This will be the IP address that the VPN will use for communication to the SMP device.
- Under the “Always use this IP address” section
- Click OK to save the changes made
- In this example we are using the Gateway Spock
- Create the Network Object(s) to represent the IP addresses behind the remote VPN gateway. In this example we have one network 192.168.12.254/24
- Note, if you have more than one network, create a group for all the networks
- Create an object to represent the other end of the tunnel
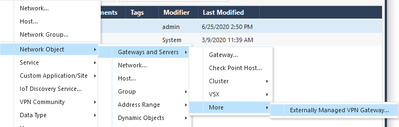
- Click New Network object --> Gateway and Servers --> More --> Externally Managed VPN Gateway
- In this example we will call it lab02-gw
- Enter the name of the object and the external IP address & Select IPsec VPN
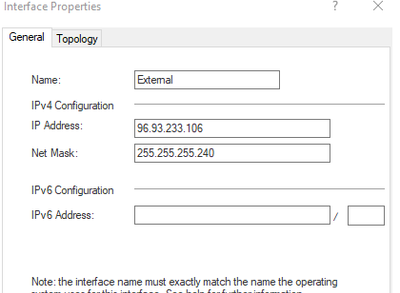
- Click on Topology, Click New, add the Name of External and the Ip information for the external interface Our example will be 96.93.233.106/28
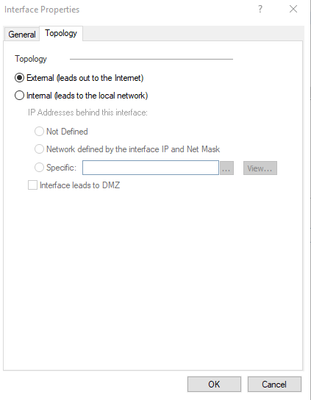
- Click on Topology, select External, click OK
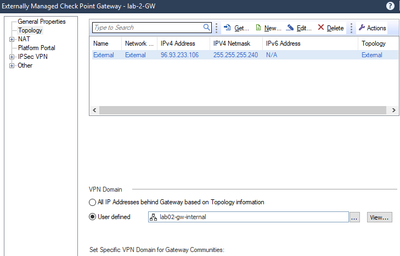
- In the VPN Domain, select “User defined“ select the Network object/group you just created in Step 3 & click OK
- Re-open the Externally Managed Check Point Gateway object you just created.
- Note: you cannot add to the VPN community until after you click OK in step 4
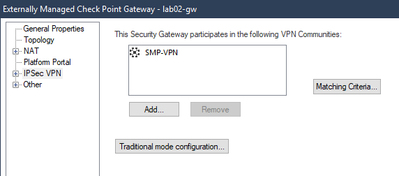
- Click on IPSec VPN, select Add, select the SMP-VPN community and pick Satellite Gateways option
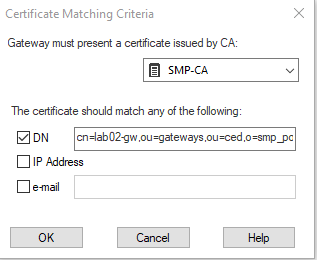
- Click Matching Criteria
- Click the drop down select and select the SMP-CA Trusted CA object we created in step 3.
- Check the DN box and past in the Distinguished Name information that you copied to the notepad in SMP Step 3. Click OK
- Publish & Install Policy
Labels
Author @Julie_Paul
Introduction
This document is instructions to setup a 1500 Appliance managed by an SMP plan in a Star VPN setup with an externally managed gateway a that is R80.x or higher.
Setup:
- Security Management Server(SMS) at R80.40, latest JHF
- 6500 Appliance managed by SMS, also at R80.40
- Security Management Portal (SMP) configured
- 1500 appliance managed by SMP portal at latest firmware version
- Plan is created and applied to the 1500 Appliance
Assumptions
- NAT is not being utilized or needed in this example, as every network behind each gateway is unique.
- You have access to both the Security Management Portal and the Security Management Server
SMP Portal Steps
- Export SMP Certificate
- Logon to the SMP portal, go to Service Domain – Settings—in the General section select Certificates
- Click export X.509 and save to your desktop
- Import SMS Certificate. (
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter