- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- fw monitor -f vs -F understanding & questions
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
fw monitor -f vs -F understanding & questions
Dear all,
In order to troubleshoot an issue I need to capture traffic in the following way:
- Traffic between hosts A and B & A and C for ICMP only
- Traffic between hosts A and B & A and C for all protocols
The reason I want to capture this traffic is because I am troubleshooting a strange issue related to ICMP, but I would like to have a capture of all the protocols as well in case nothing interesting shows up in the ICMP capture and it might be related to something else.
So far I was planning to use -F to achieve this with two captures as follows:
- One ICMP capture for both couple of hosts using 4 instances of -F parameter: fw monitor -F "a.a.a.a,0,b.b.b.b,0,1" -F "b.b.b.b,0,a.a.a.a,0,1" -F "a.a.a.a,0,c.c.c.c,0,1" -F "c.c.c.c,0,a.a.a.a,0,1" -o /<file to .cap>
- One All protocols capture for both couple of hosts using another 4 instances of -F: fw monitor -F "a.a.a.a,0,b.b.b.b,0,0" -F "b.b.b.b,0,a.a.a.a,0,0" -F "a.a.a.a,0,c.c.c.c,0,0" -F "c.c.c.c,0,a.a.a.a,0,0" -o /<file to .cap>
However, I was wondering if I could manage to achieve that within only one capture instead of two, since only one fw monitor can run and I would like to ideally reduce the number of captures needed as much as possible based on my environment constrains. For that, I was looking if I could use -f with an INSPECT file instead.
Is it possible to both capture ICMP only and all protocols traffic using one -f inspect file? I believe not but I if somebody could help validate that. In addition, from what I understand using -e or -f it does not apply to accelerated traffic, in that case would it be more recommended for me to just use -F since I can't disable acceleration in my case for the capture?
I also seem to have another strange problem when testing my filters using -f with a file, when I put my filters in the file and load it with -f it does not seem to work (it captures all traffic), but if I use the same filter in a -e expression, it works as expected.
For exemple, if I put the below in a file and load it via fw monitor -f <path to file>
#include "fwmonitor.def"
ip_p=1, ((src=a.a.a.a , dst=b.b.b.b) or (src=b.b.b.b , dst=a.a.a.a) or (src=a.a.a.a , dst=c.c.c.c) or (src=c.c.c.c , dst=a.a.a.a)), accept;
(I tried with accept at the beginning or end of the line, same results).
It does not seem to work and all captures is shown. But if I do fw monitor -e "accept ip_p=1, ((src=a.a.a.a , dst=b.b.b.b) or (src=b.b.b.b , dst=a.a.a.a) or (src=a.a.a.a , dst=c.c.c.c) or (src=c.c.c.c , dst=a.a.a.a));"
Lastly, when using -F, the last parameter (protocol number) when set to 0, captures all traffic. But when using ip_p=0 it does not seem to do so, I guess to achieve the same and capture all protocols when using -e or -f you just don't specify a protocol.
Apologies if some of the questions seem basic but I have not played with fw monitor a lot so I am trying to get a better understanding of it and apply to my situation to be more efficient.
Thank you for reading me.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't quite understand your problem correctly. If you want to display all protocols (including ICMP), they are included if you set the protocol to "0" with the -F flag option (-F a.a.a.a,0,b.b.b.b,0,0 ...).
Then you can filter all packets with Wireshark or if you have the output as a text file with "grep".
The difference between -F and -e:
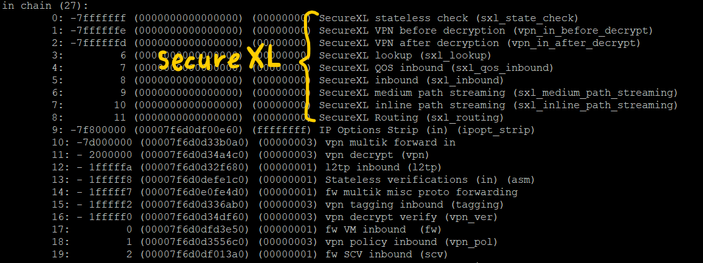
-F -> works in the chain at SecureXL and firewall kernel level
-e -> works in the chain at firewall kernel level only
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
4 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't quite understand your problem correctly. If you want to display all protocols (including ICMP), they are included if you set the protocol to "0" with the -F flag option (-F a.a.a.a,0,b.b.b.b,0,0 ...).
Then you can filter all packets with Wireshark or if you have the output as a text file with "grep".
The difference between -F and -e:
-F -> works in the chain at SecureXL and firewall kernel level
-e -> works in the chain at firewall kernel level only
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for sharing.
Kyaw Myo Oo
CCIE #58769 | PCNSE | CCSE | CISSP | PMP
CCIE #58769 | PCNSE | CCSE | CISSP | PMP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can't do what you want in one capture with fw monitor -F. However if you are only capturing ICMP traffic, you can use fw monitor -e since all non-TCP and non-UDP traffic is always handled F2F/slowpath.
fw monitor -e captures traffic in the F2F/slowpath on the Firewall Worker Instances, and therefore supports a rich matching syntax that can do "and", "or", "not", etc. But only unaccelerated F2F/slowpath traffic can be captured. The -f option is just feeding matching expressions into an fw monitor -e capture from a file instead of directly on the command line.
fw monitor -F captures traffic in the SecureXL driver (sim) on the SND/Dispatcher cores; it is in reality a kernel debug run in the sim driver and as such the matching syntax is extremely limited, but the acceleration status of traffic will not impact obtaining a complete capture. For fw monitor -F:
- You can specify up to five matching -F conditions in a single capture
- If there is more than one -F condition they are treated as an OR, not an AND (no this cannot be changed)
- For each -F expression, you are only permitted to specify a raw IP address, port number, or protocol number. Wildcards, ranges, CIDR notation or any kind of matching attempt beyond what is stated in the first sentence is not allowed. In some unlucky cases if you construct illegal matching syntax you will get blasted with a completely unfiltered capture.
All this is covered in my Max Capture: Know your Packets self-guided video series available for purchase. But for free you can access my 2021 CPX speech, which covers the various available capturing tools and hits the highlights of the Max Capture class here: Max Capture: Why cppcap is Now My Go-To Packet Capturing Tool
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you both for the additional information, very helpful!
In that case, I am indeed better off using -F with all protocols to capture everything (including ICMP + other accelerated traffic). ICMP related traffic can be filtered in the capture file later on (in Wireshark for example). So that everything can be done in one capture as mentioned earlier:
"a.a.a.a,0,b.b.b.b,0,0" -F "b.b.b.b,0,a.a.a.a,0,0" -F "a.a.a.a,0,c.c.c.c,0,0" -F "c.c.c.c,0,a.a.a.a,0,0" -o /<file to .cap>
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter