- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Re: Sam Rule and "sam: Failed to enforce inhibit r...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Sam Rule and "sam: Failed to enforce inhibit rules"
Hi,
I want to block an ip via sam as documentation:
https://sc1.checkpoint.com/documents/R77/CP_R77_Gaia_AdminWebAdminGuide/html_frameset.htm?topic=documents/R77/CP_R77_Gaia_AdminWebAdminGuide/80898
when I try to run this command in management, I have this error:
fw sam -t 600 -i src 11.11.11.11 sam: Could not resolve firewalled object name in 'Inhibit src ip 11.11.11.11 on All'. The entire SAM request was not enforced. sam: Failed to enforce inhibit rules
any advice about this issue would be appreciated
Labels
- Labels:
-
General
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
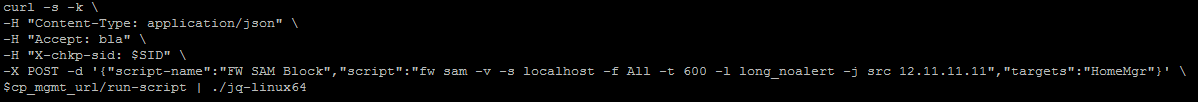
Here is a working example of using fw sam inside a run-script command written in bash using curl. Note the variables and the fw sam syntax may be different for your environment.The run-script api call has an argument for "targets". The target is the Check Point device the script/command will be executed on. In this example the fw sam command is executed on my Management server ("HomeMgr"), and the management server is telling all my gateways ("-f All") to enforce this sam rule. If you wish to use a different method you can simply translate the same parameters in the "POST -d" line below to another scripting language like mgmt_cli/python etc.
Run Script Call
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By default fw sam will push the rule to all defined gateways if executed from the management.
The fact you're getting that error suggests no gateways are defined at all (which means fw sam won't work).
Curious, what happens when you try it with an actual firewall object name (e.g. -f gw-name).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What are the requirement for fw sam to work? I am trying to check it from SmartMonitor or from the cli and get the following error:
[Expert@dc1fm4:0]# fw sam -t 60 -j src x.x.x.x
sam: fw1 (0/2) failed 'Inhibit Drop src ip x.x.x.x on All' processing
sam: fw2 (1/2) failed 'Inhibit Drop src ip x.x.x.x on All' processing
I wonder what the requirements are and why it is failing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try invoking it with debugging and post the output:
fw -d sam -t 60 -j src x.x.x.x
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
[Expert@fw1:0]# fw -d sam -M -ijn all
[7197 4124510016]@fw1[16 Feb 17:20:31] run_full_fw: running original fw:
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_create: version 5301.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_add_name_to_group: finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_set_local_names: () names. finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_create: finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_read (/opt/CPshrd-R80.40/conf/sic_policy.conf): finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_set_external_host_groups: 49 names. finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_add_name_to_group: finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_set_local_names: (local_sic_name) names. finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_add_name_to_group: finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_set_local_names: (127.0.0.1) names. finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_add_name_to_group: finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_policy_set_local_names: ("CN=fw1,O=fm1.n9wfk4") names. finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_apply_default_dn: ca_dn = [O=fm1.n9wfk4].
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_apply_default_dn: calling PM_policy_DN_conversion ..
[7197 3983104576]@fw1[16 Feb 17:20:31] PM_apply_default_dn: finished successfully.
[7197 3983104576]@fw1[16 Feb 17:20:31] fwPubKeyfromPKCS8: decoding RSA key
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 12
[7197 3983104576]@fw1[16 Feb 17:20:31] is_initialized: new process or forked
[7197 3983104576]@fw1[16 Feb 17:20:31] hash_drbg_add_sample: Adding 55 bytes worth 27500 milibits. Total: 27500. Required: 0
[7197 3983104576]@fw1[16 Feb 17:20:31] hash_drbg_add_sample: Adding 110 bytes worth 440000 milibits. Total: 467500. Required: 0
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'CKPSSL_MIN_TLS_VERSION'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Get_TLS_Version_From_Registry: SOFTWARE\CheckPoint\FW1\CKPSSL_MIN_TLS_VERSION wasn't found in the registry
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'ENABLE_3DES'.
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] Error opening file /opt/CPshrd-R80.40/database//authkeys.C:: No such file or directory
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 12
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 12
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 32
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 12
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 12
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 32
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 32
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 11
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 31
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 11
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 11
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 31
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSLctx_New: prefs = 31
[7197 3983104576]@fw1[16 Feb 17:20:31] ckpSSL_Set_TLS_Version: setting minimum TLS version: 0x301
[7197 3983104576]@fw1[16 Feb 17:20:31] cpcrypto_get_registry_value: could not query value of key 'Get_Disable_RC4'.
[7197 3983104576]@fw1[16 Feb 17:20:31] sic_sslca_Free: defs = 0x852a820, references = 0
[7197 3983104576]@fw1[16 Feb 17:20:31] fwobj_obj_initmode: mode=2
[7197 3983104576]@fw1[16 Feb 17:20:31] fwobj_obj_initmode: MGR RO mode
[7197 3983104576]@fw1[16 Feb 17:20:31] fwobj_destroy_reference_hash: reference_resolving_hash_users<0
[7197 3983104576]@fw1[16 Feb 17:20:31] fetch_objects: Start
[7197 3983104576]@fw1[16 Feb 17:20:31] fwobj_destroy_reference_hash: reference_resolving_hash_users<0
[7197 3983104576]@fw1[16 Feb 17:20:31] sam_client_main called
[7197 3983104576]@fw1[16 Feb 17:20:31] fwdopsec_load called
[7197 3983104576]@fw1[16 Feb 17:20:31] fwdopsec_load: fwdopsec library is loaded
[7197 3983104576]@fw1[16 Feb 17:20:31] resolver_gethostbyname: Performing gethostbyname for localhost
[7197 3983104576]@fw1[16 Feb 17:20:31] Env Configuration:
(
:type (opsec_info)
)
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...opsec_sic_name...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...opsec_sslca_file...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...opsec_shared_local_path...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...opsec_sic_policy_file...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...opsec_mt...
[7197 3983104576]@fw1[16 Feb 17:20:31] opsec_init: multithread safety is not initialized
[7197 3983104576]@fw1[16 Feb 17:20:31] fwasync_get_maxbuf: maxbuf=4194304
[7197 3983104576]@fw1[16 Feb 17:20:31] opsec_init_entity_sic: called for the client side
[7197 3983104576]@fw1[16 Feb 17:20:31] Configuring entity sam_server
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...sam_server...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...sam_server...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...sam_server...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...sam_server...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...sam_server...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...sam_server...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...sam_server...
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...sam_server...
[7197 3983104576]@fw1[16 Feb 17:20:31] opsec_init_entity_sic: Authentication not initialized...
[7197 3983104576]@fw1[16 Feb 17:20:31] opsec_init_entity_sic: in a CP product - no rules added to SIC
[7197 3983104576]@fw1[16 Feb 17:20:31] opsec_get_comm: creating comm for ent=855a220 peer=855b390 passive=0 key=2 info=0
[7197 3983104576]@fw1[16 Feb 17:20:31] c=0x855a220 s=0x855b390 comm_type=4
[7197 3983104576]@fw1[16 Feb 17:20:31] Could not find info for ...opsec_client...
[7197 3983104576]@fw1[16 Feb 17:20:31] opsec_get_comm: Creating session hash (size=256)
[7197 3983104576]@fw1[16 Feb 17:20:31] opsec_get_comm: ADDING comm=0x855c518 to ent=0x855a220 with key=2
[7197 3983104576]@fw1[16 Feb 17:20:31] fw_do_get_all_ipaddrs: called. naddrs=32769
[7197 3983104576]@fw1[16 Feb 17:20:31] resolver_getaddrinfo_list: name=fw1, pref=0
[7197 3983104576]@fw1[16 Feb 17:20:31] resolver_getaddrinfo_list: found peer 0 x.x.x.y
[7197 3983104576]@fw1[16 Feb 17:20:31] fw_do_get_all_ipaddrs: fw_ipaddr_both returned x.x.x.y ::
[7197 3983104576]@fw1[16 Feb 17:20:31] fw_do_get_all_ipaddrs: found 0 addresses
[7197 3983104576]@fw1[16 Feb 17:20:31] sic_init_myaddr_ex: could not get my own IPv6 addresses.
[7197 3983104576]@fw1[16 Feb 17:20:31] resolver_gethostbyname: Performing gethostbyname for fw1
[7197 3983104576]@fw1[16 Feb 17:20:31] peers addresses are
[7197 3983104576]@fw1[16 Feb 17:20:31] x.x.x.y
[7197 3983104576]@fw1[16 Feb 17:20:31] x.x.x.z
[7197 3983104576]@fw1[16 Feb 17:20:31] x.x.x.w
[7197 3983104576]@fw1[16 Feb 17:20:31] x.x.x.x
[7197 3983104576]@fw1[16 Feb 17:20:31] sic_client_do_connect: no server sic name supplied, server sic name is unknown.
[7197 3983104576]@fw1[16 Feb 17:20:31] cpsicdemux_get_mode: the mode is 1
[7197 3983104576]@fw1[16 Feb 17:20:31] cpsicdemux_check_mode: server_mode=1 | requested_mode=1
[7197 3983104576]@fw1[16 Feb 17:20:31] sam_client_session_creator: created anchor record, session: 85625b0
[7197 3983104576]@fw1[16 Feb 17:20:31] opsec_send_datagram_e: SESSION ID:3 is sending DG_ID=3 DG_TYPE=0x1(DGTYPE_CREATE_SESSION)
[7197 3983104576]@fw1[16 Feb 17:20:31] pushing dgtype=1 len=0 to list=0x855c534
[7197 3983104576]@fw1[16 Feb 17:20:31] dg_stack_push: dg_counter=1
[7197 3983104576]@fw1[16 Feb 17:20:31] opsec_send_datagram_e: SESSION ID:3 is sending DG_ID=3 DG_TYPE=0x602(???)
[7197 3983104576]@fw1[16 Feb 17:20:31] pushing dgtype=602 len=0 to list=0x855c534
[7197 3983104576]@fw1[16 Feb 17:20:31] dg_stack_push: dg_counter=2
[7197 3983104576]@fw1[16 Feb 17:20:31] opsec_send_datagram_e: SESSION ID:3 is sending DG_ID=3 DG_TYPE=0x608(???)
[7197 3983104576]@fw1[16 Feb 17:20:31] pushing dgtype=608 len=42 to list=0x855c534
[7197 3983104576]@fw1[16 Feb 17:20:31] dg_stack_push: dg_counter=3
[7197 3983104576]@fw1[16 Feb 17:20:31] sam_retrieve_info: Sent dg: idnum: 1, type: 800, src: 0, submask: ffffffff, sport: 0, dst: 0, submask: ffffffff, dport: 0, ip_p: 0, actions: 305, serv_ip: ed3f86c5
[7197 3983104576]@fw1[16 Feb 17:20:31] fwasync_conn_params: <7f000001,49787> -> <7f000001,18183>
[7197 3983104576]@fw1[16 Feb 17:20:31] fwasync_connbuf_realloc: reallocating 0 from 0 to 1028
[7197 3983104576]@fw1[16 Feb 17:20:31] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:31] fwasync_connbuf_realloc: reallocating 0 from 0 to 1028
[7197 3983104576]@fw1[16 Feb 17:20:31] sic_client_set_version: 15: protocol version is 59000000
[7197 3983104576]@fw1[16 Feb 17:20:31] cpsicdemux_check_mode: server_mode=1 | requested_mode=1
[7197 3983104576]@fw1[16 Feb 17:20:31] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:31] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:31] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] call_handlers_list: no conversion done, set CN=fw1,O=fm1.n9wfk4 as sic name
[7197 3983104576]@fw1[16 Feb 17:20:32] PM_session_init: given session O(CN=fw1,O=fm1.n9wfk4;CN=fw1,O=fm1.n9wfk4;18183;sam).
[7197 3983104576]@fw1[16 Feb 17:20:32] PM_policy_query: input session O(CN=fw1,O=fm1.n9wfk4;CN=fw1,O=fm1.n9wfk4;18183;sam).
[7197 3983104576]@fw1[16 Feb 17:20:32] PM_policy_query: rule found (ANY;ME;ANY;ANY;cp_local(1/1)).
[7197 3983104576]@fw1[16 Feb 17:20:32] PM_policy_query: finished successfully. 1st method = cp_local
[7197 3983104576]@fw1[16 Feb 17:20:32] PM_policy_choose: finished successfully. choose: cp_local.
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] sic_client_handler: 15: auth result = 1
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_auth_client_connected:conn=0x855cc98 opaque=0x855ca28 err=0 comm=0x855c518
[7197 3983104576]@fw1[16 Feb 17:20:32] Attaching conn 855cc98 to comm 855c518
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] comm succeeded. fwconn=855c518
[7197 3983104576]@fw1[16 Feb 17:20:32] pulling dgtype=1 len=0 to list=0x855c534
[7197 3983104576]@fw1[16 Feb 17:20:32] dg_stack_pull: dg_counter=2
[7197 3983104576]@fw1[16 Feb 17:20:32] pulling dgtype=602 len=0 to list=0x855c534
[7197 3983104576]@fw1[16 Feb 17:20:32] dg_stack_pull: dg_counter=1
[7197 3983104576]@fw1[16 Feb 17:20:32] pulling dgtype=608 len=42 to list=0x855c534
[7197 3983104576]@fw1[16 Feb 17:20:32] dg_stack_pull: dg_counter=0
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_comm_send_datagram: COMM 855c518 switched to non-congested state
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_comm_notify: COM 0x855c518 got signal 131073
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_comm_notify: COM 0x855c518 got signal 131074
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_comm_notify: COM 0x855c518 got signal 131074
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] demultiplex type=5 session-id=3
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] demultiplex type=707 session-id=3
[7197 3983104576]@fw1[16 Feb 17:20:32] sam_client_demultiplex_datagram: INFO RETRIEVED
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] demultiplex type=707 session-id=3
[7197 3983104576]@fw1[16 Feb 17:20:32] sam_client_demultiplex_datagram: INFO RETRIEVED
sam: fw1 (0/2) failed 'Monitor Inhibit Drop Notify all on All' processing
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] demultiplex type=707 session-id=3
[7197 3983104576]@fw1[16 Feb 17:20:32] sam_client_demultiplex_datagram: INFO RETRIEVED
sam: hqfw2b (1/2) failed 'Monitor Inhibit Drop Notify all on All' processing
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] demultiplex type=707 session-id=3
[7197 3983104576]@fw1[16 Feb 17:20:32] sam_client_demultiplex_datagram: INFO RETRIEVED
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_end_session_e: scheduling the end of session 3
[7197 3983104576]@fw1[16 Feb 17:20:32] Destroying session (85625b0) id 3 (ent=855a220) reason=END_BY_APPLICATION
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_send_datagram_e: SESSION ID:3 is sending DG_ID=3 DG_TYPE=0x3(DGTYPE_NOTIFY_END_SESSION)
[7197 3983104576]@fw1[16 Feb 17:20:32] sam_client_pre_user_session_deletor: started
[7197 3983104576]@fw1[16 Feb 17:20:32] sam_client_pre_user_session_deletor: No queries were left unresolved
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_requset: destroyed Table: Table(8562658)
[7197 3983104576]@fw1[16 Feb 17:20:32] SESSION ID:3 already resumed read
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_comm_is_needed:comm 0x855c518 0/0 sessions need the comm.
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_comm_notify: COM 0x855c518 got signal 131074
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] demultiplex type=a session-id=0
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_comm_is_needed:comm 0x855c518 0/0 sessions need the comm.
[7197 3983104576]@fw1[16 Feb 17:20:32] destroying comm 0x855c518
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_conn_get: get max buffer size (4194304) .
[7197 3983104576]@fw1[16 Feb 17:20:32] Destroying comm 0x855c518 with 0 active sessions
[7197 3983104576]@fw1[16 Feb 17:20:32] pulling dgtype=ffffffff len=-1 to list=0x855c534
[7197 3983104576]@fw1[16 Feb 17:20:32] dg_stack_pull: dg_counter=0
[7197 3983104576]@fw1[16 Feb 17:20:32] REMOVING comm=0x855c518 from ent=0x855a220 with key=2
[7197 3983104576]@fw1[16 Feb 17:20:32] sic_client_end_handler: for conn id = 15
[7197 3983104576]@fw1[16 Feb 17:20:32] fwasync_do_end_conn: 15: calling 0xf37b4b20 to free opaque 0x855ca38
[7197 3983104576]@fw1[16 Feb 17:20:32] T_event_mainloop_e: T_event_mainloop_iter returns 0
[7197 3983104576]@fw1[16 Feb 17:20:32] The server doesn't run
[7197 3983104576]@fw1[16 Feb 17:20:32] Destroying entity 1 with 0 active comms
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_destroy_entity_sic: deleting sic rules for entity 0x855a220
[7197 3983104576]@fw1[16 Feb 17:20:32] The server doesn't run
[7197 3983104576]@fw1[16 Feb 17:20:32] Destroying entity 2 with 0 active comms
[7197 3983104576]@fw1[16 Feb 17:20:32] opsec_destroy_entity_sic: deleting sic rules for entity 0x855b390
[7197 3983104576]@fw1[16 Feb 17:20:32] destroy_rand_mutex: destroy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I wonder if it has anything to do with data / mgmt plane separation.
The gateway mgmt ip is in the mgmt plane and the sam process runs in the data plane, no? I wonder if it is a problem?
netstat -nap | grep 18183
tcp 0 0 0.0.0.0:18183 0.0.0.0:* LISTEN 11317/fwd
tcp 0 0 127.0.0.1:18183 127.0.0.1:41357 ESTABLISHED 11317/fwd
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is a working example of using fw sam inside a run-script command written in bash using curl. Note the variables and the fw sam syntax may be different for your environment.The run-script api call has an argument for "targets". The target is the Check Point device the script/command will be executed on. In this example the fw sam command is executed on my Management server ("HomeMgr"), and the management server is telling all my gateways ("-f All") to enforce this sam rule. If you wish to use a different method you can simply translate the same parameters in the "POST -d" line below to another scripting language like mgmt_cli/python etc.
Run Script Call

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


