- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- New FW rule to existing in-line layer
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
New FW rule to existing in-line layer
Anyone that tried to create new fw rule within an existing in-line layer with curl or python requests?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It doesn't create a copy, it creates a new rule in the layer "Network" which references the same inline layer. It sounds like you want your request body to be more like this:
d = {"layer" : "0cbdba80-308a-4007-9701-c380c545deb9", "position" : 1, "name" : "inline rule1", "source" : "new_host2", "destination" : "new_host4", "action" : "Accept", "service" : "any", "track" : "log", "comments" : "ROBS_TEST" }
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
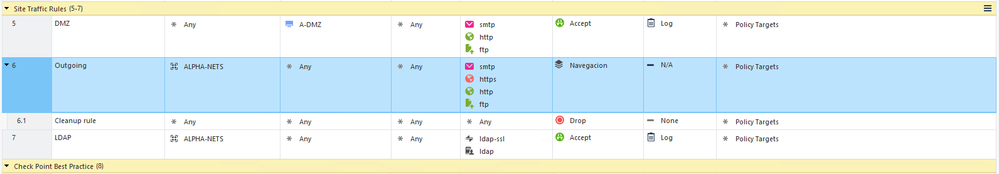
You can definitely do it.
Keep in mind that that an inline layer can potentially be re-used in other policy packages.
So you have to refer to that specific layer when you want to make modifications.
Some related discussion here: https://community.checkpoint.com/t5/API-CLI-Discussion/show-access-rulebase-along-with-inline-layers...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I saw that discussion before but it was related only to show-access-rulebase within an inline-layer and not create a new access rule within an inline-layer.
or am I missing something? 😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In order to manipulate an inline layer via the API, you need to get its name or UID.
Thats where that thread is helpful.
There is a way to get it via SmartConsole as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can see the underlying rules within a inline-layer with this post request
h = {'Content-Type': 'application/json', 'X-chkp-sid': '{}'.format(sid) }
d = {"uid" : "0cbdba80-308a-4007-9701-c380c545deb9"}
r = requests.post(url + 'show-access-rulebase', headers=h, data=json.dumps(d), verify=False)
pprint(r.json())
{'from': 1,
'name': 'TEST_LAYER',
'objects-dictionary': [{'domain': {'domain-type': 'data domain',
'name': 'Check Point Data',
'uid': 'a0bbbc99-adef-4ef8-bb6d-defdefdefdef'},
'name': 'Any',
'type': 'CpmiAnyObject',
'uid': '97aeb369-9aea-11d5-bd16-0090272ccb30'},
{'domain': {'domain-type': 'data domain',
'name': 'Check Point Data',
'uid': 'a0bbbc99-adef-4ef8-bb6d-defdefdefdef'},
'name': 'Drop',
'type': 'RulebaseAction',
'uid': '6c488338-8eec-4103-ad21-cd461ac2c473'},
{'domain': {'domain-type': 'data domain',
'name': 'Check Point Data',
'uid': 'a0bbbc99-adef-4ef8-bb6d-defdefdefdef'},
'name': 'None',
'type': 'Track',
'uid': '29e53e3d-23bf-48fe-b6b1-d59bd88036f9'},
{'domain': {'domain-type': 'data domain',
'name': 'Check Point Data',
'uid': 'a0bbbc99-adef-4ef8-bb6d-defdefdefdef'},
'name': 'Policy Targets',
'type': 'Global',
'uid': '6c488338-8eec-4103-ad21-cd461ac2c476'}],
'rulebase': [{'action': '6c488338-8eec-4103-ad21-cd461ac2c473',
'action-settings': {},
'comments': '',
'content': ['97aeb369-9aea-11d5-bd16-0090272ccb30'],
'content-direction': 'any',
'content-negate': False,
'custom-fields': {'field-1': '', 'field-2': '', 'field-3': ''},
'destination': ['97aeb369-9aea-11d5-bd16-0090272ccb30'],
'destination-negate': False,
'domain': {'domain-type': 'domain',
'name': 'SMC User',
'uid': '41e821a0-3720-11e3-aa6e-0800200c9fde'},
'enabled': True,
'install-on': ['6c488338-8eec-4103-ad21-cd461ac2c476'],
'meta-info': {'creation-time': {'iso-8601': '2021-03-15T15:05+0100',
'posix': 1615817149454},
'creator': 'xagirobadm',
'last-modifier': 'xagirobadm',
'last-modify-time': {'iso-8601': '2021-03-15T15:05+0100',
'posix': 1615817149454},
'lock': 'unlocked',
'validation-state': 'ok'},
'name': 'Cleanup rule',
'rule-number': 1,
'service': ['97aeb369-9aea-11d5-bd16-0090272ccb30'],
'service-negate': False,
'source': ['97aeb369-9aea-11d5-bd16-0090272ccb30'],
'source-negate': False,
'time': ['97aeb369-9aea-11d5-bd16-0090272ccb30'],
'track': {'accounting': False,
'alert': 'none',
'enable-firewall-session': False,
'per-connection': False,
'per-session': False,
'type': '29e53e3d-23bf-48fe-b6b1-d59bd88036f9'},
'type': 'access-rule',
'uid': '3925bd94-5764-49c6-89a5-2ea3f218f87d',
'vpn': ['97aeb369-9aea-11d5-bd16-0090272ccb30']}],
'to': 1,
'total': 1,
'uid': '0cbdba80-308a-4007-9701-c380c545deb9'}
'name': 'TEST_LAYER',
'objects-dictionary': [{'domain': {'domain-type': 'data domain',
'name': 'Check Point Data',
'uid': 'a0bbbc99-adef-4ef8-bb6d-defdefdefdef'},
'name': 'Any',
'type': 'CpmiAnyObject',
'uid': '97aeb369-9aea-11d5-bd16-0090272ccb30'},
{'domain': {'domain-type': 'data domain',
'name': 'Check Point Data',
'uid': 'a0bbbc99-adef-4ef8-bb6d-defdefdefdef'},
'name': 'Drop',
'type': 'RulebaseAction',
'uid': '6c488338-8eec-4103-ad21-cd461ac2c473'},
{'domain': {'domain-type': 'data domain',
'name': 'Check Point Data',
'uid': 'a0bbbc99-adef-4ef8-bb6d-defdefdefdef'},
'name': 'None',
'type': 'Track',
'uid': '29e53e3d-23bf-48fe-b6b1-d59bd88036f9'},
{'domain': {'domain-type': 'data domain',
'name': 'Check Point Data',
'uid': 'a0bbbc99-adef-4ef8-bb6d-defdefdefdef'},
'name': 'Policy Targets',
'type': 'Global',
'uid': '6c488338-8eec-4103-ad21-cd461ac2c476'}],
'rulebase': [{'action': '6c488338-8eec-4103-ad21-cd461ac2c473',
'action-settings': {},
'comments': '',
'content': ['97aeb369-9aea-11d5-bd16-0090272ccb30'],
'content-direction': 'any',
'content-negate': False,
'custom-fields': {'field-1': '', 'field-2': '', 'field-3': ''},
'destination': ['97aeb369-9aea-11d5-bd16-0090272ccb30'],
'destination-negate': False,
'domain': {'domain-type': 'domain',
'name': 'SMC User',
'uid': '41e821a0-3720-11e3-aa6e-0800200c9fde'},
'enabled': True,
'install-on': ['6c488338-8eec-4103-ad21-cd461ac2c476'],
'meta-info': {'creation-time': {'iso-8601': '2021-03-15T15:05+0100',
'posix': 1615817149454},
'creator': 'xagirobadm',
'last-modifier': 'xagirobadm',
'last-modify-time': {'iso-8601': '2021-03-15T15:05+0100',
'posix': 1615817149454},
'lock': 'unlocked',
'validation-state': 'ok'},
'name': 'Cleanup rule',
'rule-number': 1,
'service': ['97aeb369-9aea-11d5-bd16-0090272ccb30'],
'service-negate': False,
'source': ['97aeb369-9aea-11d5-bd16-0090272ccb30'],
'source-negate': False,
'time': ['97aeb369-9aea-11d5-bd16-0090272ccb30'],
'track': {'accounting': False,
'alert': 'none',
'enable-firewall-session': False,
'per-connection': False,
'per-session': False,
'type': '29e53e3d-23bf-48fe-b6b1-d59bd88036f9'},
'type': 'access-rule',
'uid': '3925bd94-5764-49c6-89a5-2ea3f218f87d',
'vpn': ['97aeb369-9aea-11d5-bd16-0090272ccb30']}],
'to': 1,
'total': 1,
'uid': '0cbdba80-308a-4007-9701-c380c545deb9'}
But still no luck adding new rule within this inline-layer (TEST-LAYER)
@PhoneBoy : do you have an exemple with curl or python request?
@PhoneBoy : do you have an exemple with curl or python request?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What precise API call did you make to try and do it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
h = {'Content-Type': 'application/json', 'X-chkp-sid': '{}'.format(sid) }
d = {"layer" : "Network", "inline-layer" : "0cbdba80-308a-4007-9701-c380c545deb9", "position" : 1, "name" : "inline rule1", "source" : "new_host2", "destination" : "new_host4", "action" : "Apply Layer", "service" : "any", "track" : "log", "comments" : "ROBS_TEST" }
r = requests.post(url + 'add-access-rule', headers=h, data=json.dumps(d), verify=False)
pprint(r.json())
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The body you provided is saying to add a new rule to the layer named "Network" which then passes matching traffic to the layer "0cbdba80-308a-4007-9701-c380c545deb9".
What does this call return to your program?
What do you want to happen instead?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It seems that it creates a "copy" of inline-layern TEST_LAYER, like a shared one..??
What I want is to add an underlying access rule to existing inline layer, in this case TEST_LAYER.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @Rob_A ,
If you want just add a rule in your inline layer.
Check the name of the inline layer. Using the module "show-access-layers"
Address: http://127.0.0.1:50277/web_api/v1.3/show-access-layers
Encoding: ISO-8859-1
Http-Method: POST
Content-Type: application/json
Headers: {Accept=[*/*], accept-encoding=[gzip, deflate, br], Cache-Control=[no-cache], connection=[keep-alive], Content-Length=[70], content-type=[application/json], Host=[127.0.0.1:50277], Postman-Token=[d83e3ed2-0c54-44e6-91d8-f63be888ff7e], User-Agent=[PostmanRuntime/7.26.8], X-chkp-sid=[255dcfc11685f477c0198bbe2184d278], X-Forwarded-For=[172.16.6.209], X-Forwarded-Host=[10.1.1.100], X-Forwarded-Host-Port=[443], X-Forwarded-Server=[10.1.1.100]}
Payload: {
"limit" : 50,
"offset" : 0,
"details-level" : "standard"
}
Response-Code: 200
Content-Type: application/json
Headers: {Content-Type=[application/json], Date=[Wed, 31 Mar 2021 15:48:33 GMT]}
Payload: {
"access-layers" : [ {
{
"uid" : "329a689f-77c3-4be1-9c25-c52cfecbcd2d",
"name" : "Navegacion",
"type" : "access-layer",
"domain" : {
"uid" : "ca6c345d-69a8-4854-b2a9-e78d7698e229",
"name" : "domaintest",
"domain-type" : "domain"
}
}, {
"uid" : "1ed41347-fdbe-4139-a20b-42da72d91ef0",
"name" : "Network",
"type" : "access-layer",
"domain" : {
"uid" : "ca6c345d-69a8-4854-b2a9-e78d7698e229",
"name" : "domaintest",
"domain-type" : "domain"
}
} ],
"from" : 1,
"to" : 2,
"total" : 2
}
After that, create a rule like always with module add-access-rule
Address: http://127.0.0.1:50277/web_api/v1.3/add-access-rule
Encoding: ISO-8859-1
Http-Method: POST
Content-Type: application/json
Headers: {Accept=[*/*], accept-encoding=[gzip, deflate, br], Cache-Control=[no-cache], connection=[keep-alive], Content-Length=[114], content-type=[application/json], Host=[127.0.0.1:50277], Postman-Token=[0c782250-39e1-428b-9539-8522973a4eb6], User-Agent=[PostmanRuntime/7.26.8], X-chkp-sid=[0460973acad474eb653b28a5f7ec00fc], X-Forwarded-For=[172.16.6.209], X-Forwarded-Host=[10.1.1.100], X-Forwarded-Host-Port=[443], X-Forwarded-Server=[10.1.1.100]}
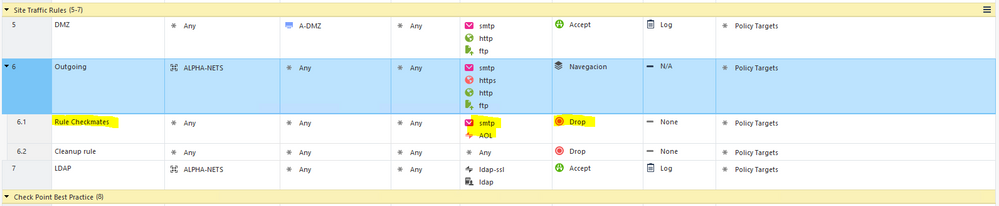
Payload: {
"layer" : "Navegacion",
"position" : 1,
"name" : "Rule Checkmates",
"service" : [ "SMTP", "AOL" ]
}
Response-Code: 200
Content-Type: application/json
Headers: {Content-Type=[application/json], Date=[Wed, 31 Mar 2021 15:55:34 GMT]}
Payload: {
"uid" : "488e9ac6-4fcb-4e5e-b8dd-c2e7e2676f5a",
"name" : "Rule Checkmates",
"type" : "access-rule",
"domain" : {
"uid" : "ca6c345d-69a8-4854-b2a9-e78d7698e229",
"name" : "domaintest",
"domain-type" : "domain"
},
"track" : {
"type" : {
"uid" : "29e53e3d-23bf-48fe-b6b1-d59bd88036f9",
"name" : "None",
"type" : "Track",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
}
},
"per-session" : false,
"per-connection" : false,
"accounting" : false,
"enable-firewall-session" : false,
"alert" : "none"
},
"layer" : "329a689f-77c3-4be1-9c25-c52cfecbcd2d",
"source" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
}
} ],
"source-negate" : false,
"destination" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
}
} ],
"destination-negate" : false,
"service" : [ {
"uid" : "97aeb3d9-9aea-11d5-bd16-0090272ccb30",
"name" : "smtp",
"type" : "service-tcp",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"port" : "25"
}, {
"uid" : "97aeb44f-9aea-11d5-bd16-0090272ccb30",
"name" : "AOL",
"type" : "service-tcp",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"port" : "5190"
} ],
"service-negate" : false,
"vpn" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
}
} ],
"action" : {
"uid" : "6c488338-8eec-4103-ad21-cd461ac2c473",
"name" : "Drop",
"type" : "RulebaseAction",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
}
},
"action-settings" : { },
"content" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
}
} ],
"content-negate" : false,
"content-direction" : "any",
"time" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
}
} ],
"custom-fields" : {
"field-1" : "",
"field-2" : "",
"field-3" : ""
},
"meta-info" : {
"lock" : "locked by current session",
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1617206133411,
"iso-8601" : "2021-03-31T17:55+0200"
},
"last-modifier" : "admin",
"creation-time" : {
"posix" : 1617206133411,
"iso-8601" : "2021-03-31T17:55+0200"
},
"creator" : "admin"
},
"comments" : "",
"enabled" : true,
"install-on" : [ {
"uid" : "6c488338-8eec-4103-ad21-cd461ac2c476",
"name" : "Policy Targets",
"type" : "Global",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
}
} ]
}
--------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It doesn't create a copy, it creates a new rule in the layer "Network" which references the same inline layer. It sounds like you want your request body to be more like this:
d = {"layer" : "0cbdba80-308a-4007-9701-c380c545deb9", "position" : 1, "name" : "inline rule1", "source" : "new_host2", "destination" : "new_host4", "action" : "Accept", "service" : "any", "track" : "log", "comments" : "ROBS_TEST" }- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And it works 🙂
Thanks!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter