- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Re: How to add a rule with multiple actions
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to add a rule with multiple actions
I'm working on a baseline for an inline policy to enable URL Filtering and Application control for a customer that has not used this before, I searched through the questions here but could not find a response that would give me the clue.
I run into some issues, while most things work just fine, adding and filling groups and creating the Layer with all rules, I'm just hitting a few snags, like when I add a drop rule I would also like to show the default Block Page, however I can only add 1 action Item, how can you add more actions?
The layer is added but unless I set it to shared the layer cannot be manually used as an inline layer. After the test I wanted to remove the layer again, it is not in use but delete layer is grayed out, in Manage Policies and Layers.
Regards, Maarten
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You must have App/URL or content awareness enabled on the layer to add other actions. I suspect this is the issue. On the layer be sure the additional blades are checked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
in the create of the rule I had used applications-and-url-filtering "true" when I created the layer, so that part is ok, but what is the syntax for adding multiple actions?
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So this is per the API?
So under the documentation add-access-rule, you need to supply the user-check object with field interaction.
It wasn't clear in the docs(Amiad Stern) what was valid for this field, so I reverse engineered by making a rule in SmartConsole, then using show-access-rule to see how it returned.
An example would be:
#mgmt_cli add-access-rule layer "<layer>" position top action drop user-check.interaction "Blocked Message - Access Control"
This added a rule as drop with standard Blocked Message.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, so the thing I could not find in the documentation was the user-check.interaction "Blocked Message - Access Control" part, that helps to make that last bit clear, thanks a lot.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If anyone is interested I can post this script that will create this shared layer:
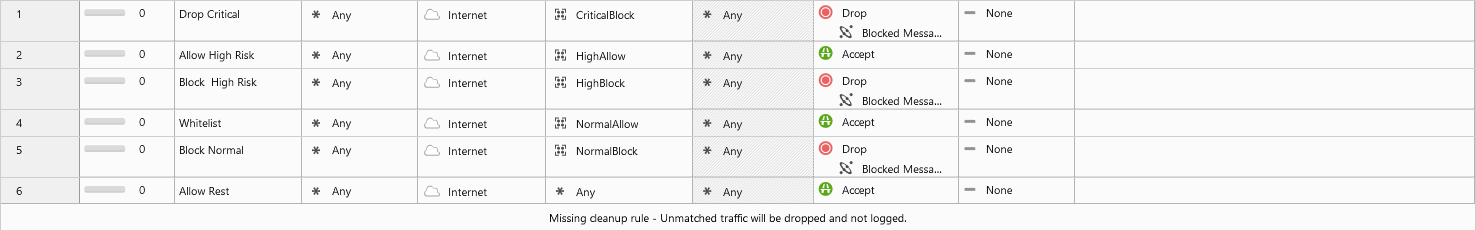
CriticalBlock has the categories Child Abuse, Critical Risk and a newly created category Blacklist in it.
HighBlock only has High risk in it And NormalAllow contains a newly category WhiteList.
Normalblock contains a list of default (best practice) block categories.
All is very simple to adjust, but it is a nice template to start with.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maarten, please do post the script.
Thank you,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
here it is:
mgmt_cli login user admin password <PW> domain <Domain> -m <IP> > id.txt
mgmt_cli add application-site-category name "WhiteList" description "Custom Whitelist category" -s id.txt
mgmt_cli add application-site-category name "BlackList" description "Custom Blacklist category" -s id.txt
mgmt_cli add application-site-group name "CriticalBlock" members.1 "Critical Risk" members.2 "Child Abuse" members.3 "BlackList" -s id.txt
mgmt_cli add application-site-group name "HighAllow" -s id.txt
mgmt_cli add application-site-group name "HighBlock" members.1 "High Risk" -s id.txt
mgmt_cli add application-site-group name "NormalAllow" members.1 "WhiteList" -s id.txt
mgmt_cli add application-site-group name "NormalBlock" members.1 "Anonymizer" members.2 "Botnets" members.9 "Illegal Drugs" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "File Storage and Sharing" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "File Upload" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Gambling" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Games" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Hate / Racism" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Illegal / Questionable" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Illegal Drugs" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Media Sharing" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Media Streams" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Nudity" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "P2P File Sharing" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Pornography" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Sex" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Spam" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Spyware / Malicious Sites" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Suspicious Content" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Tasteless" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Violence" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Weapons" -s id.txt
mgmt_cli set application-site-group name "NormalBlock" members.add "Web Advertisements" -s id.txt
mgmt_cli add service-group name "Blocked-Ports" members.1 "smtp" -s id.txt
mgmt_cli set service-group name "Blocked-Ports" members.add "imap" -s id.txt
mgmt_cli set service-group name "Blocked-Ports" members.add "IMAP-SSL" -s id.txt
mgmt_cli set service-group name "Blocked-Ports" members.add "pop-3" -s id.txt
mgmt_cli set service-group name "Blocked-Ports" members.add "POP3S" -s id.txt
mgmt_cli set service-group name "Blocked-Ports" members.add "SMTPS" -s id.txt
mgmt_cli set service-group name "Blocked-Ports" members.add "ssh" -s id.txt
mgmt_cli add access-layer name "Internet-Filter" firewall "false" applications-and-url-filtering "true" shared "true" add-default-rule "false" -s id.txt
mgmt_cli add access-rule layer "Internet-Filter" position 1 name "Drop Critical" service "CriticalBlock" destination "Internet" action "Drop" user-check.interaction "Blocked Message - Access Control" track "log" -s id.txt
mgmt_cli add access-rule layer "Internet-Filter" position 2 name "Allow High Risk" service "HighAllow" destination "Internet" action "Accept" track "log" -s id.txt
mgmt_cli add access-rule layer "Internet-Filter" position 3 name "Block High Risk" service "HighBlock" destination "Internet" action "Drop" user-check.interaction "Blocked Message - Access Control" track "log" -s id.txt
mgmt_cli add access-rule layer "Internet-Filter" position 4 name "Whitelist" service "NormalAllow" destination "Internet" action "Accept" track "log" -s id.txt
mgmt_cli add access-rule layer "Internet-Filter" position 5 name "Block Normal" service "NormalBlock" destination "Internet" action "Drop" user-check.interaction "Blocked Message - Access Control" track "log" -s id.txt
mgmt_cli add access-rule layer "Internet-Filter" position 6 name "Allow Rest" destination "Internet" service "Blocked-Ports" service-negate "true" action "Accept" track "log" -s id.txt
mgmt_cli publish -s id.txt
mgmt_cli logout -s id.txt
Regards, Maarten
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 1 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


