- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Cyber Attack View formal release for R80.10 & R80....
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cyber Attack View formal release for R80.10 & R80.20
Hey,
Few months ago, we started to work the new dashboard for Threat Prevention Investigation methods.
You can find the first post in here: https://community.checkpoint.com/community/management/visibility-monitoring/blog/2018/04/04/threat-p...
I am happy to announce that we formally released the version for R80.10 & R80.20 under the following SK - sk134634
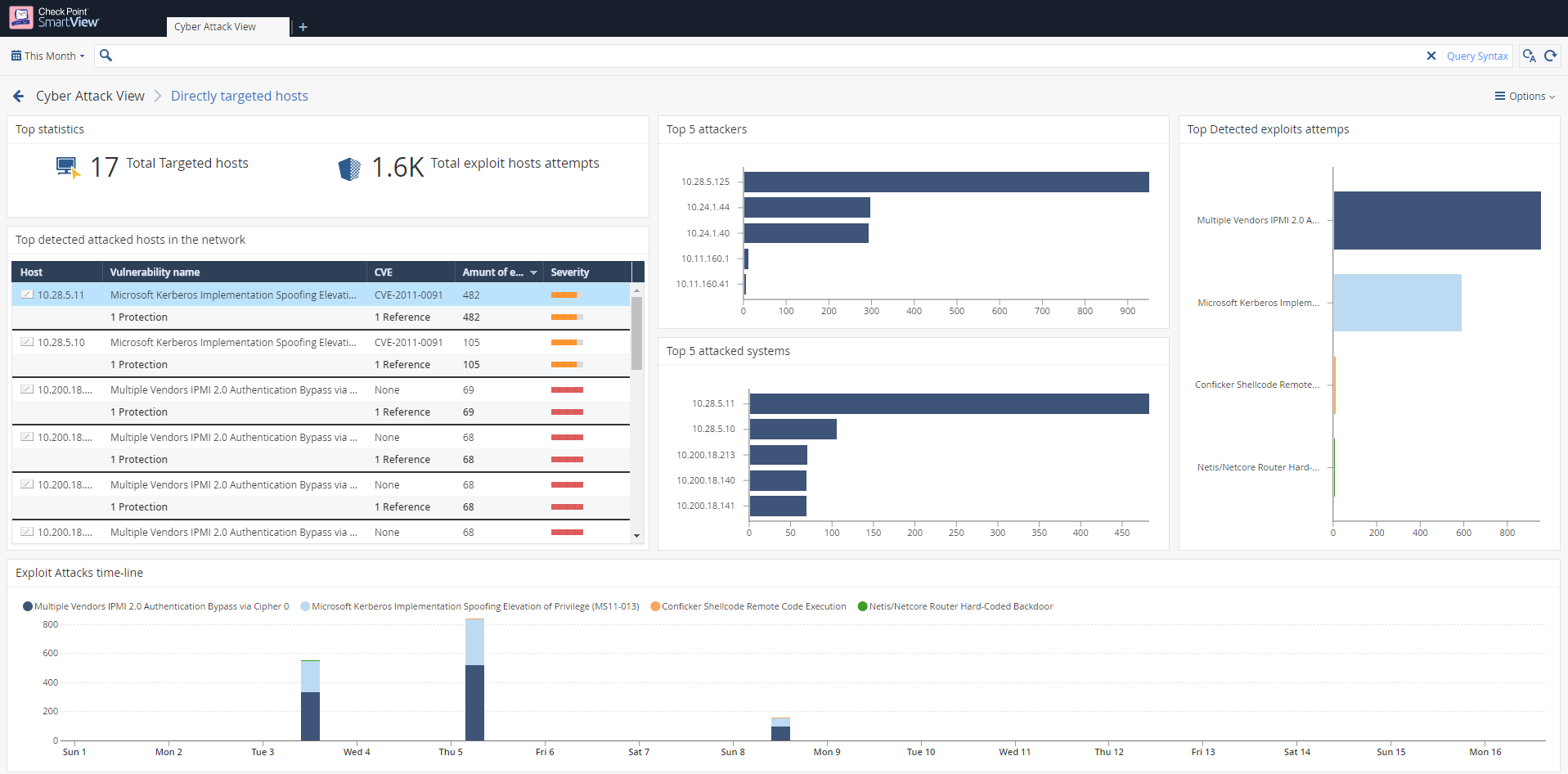
This dashboard is allowing you to locate the cyber threat you need to address to based on attack vector and in a very fast way. our EA customers were able to locate threats on/in their network in a very fast way and without the need to query on their logs as the first action.
we improved the queries also based on the community inputs and we are looking for more improvements and inputs from the community. if you have any inputs related to the dashboard please contact me directly - Orenkor@checkpoint.com
Thanks,
Oren
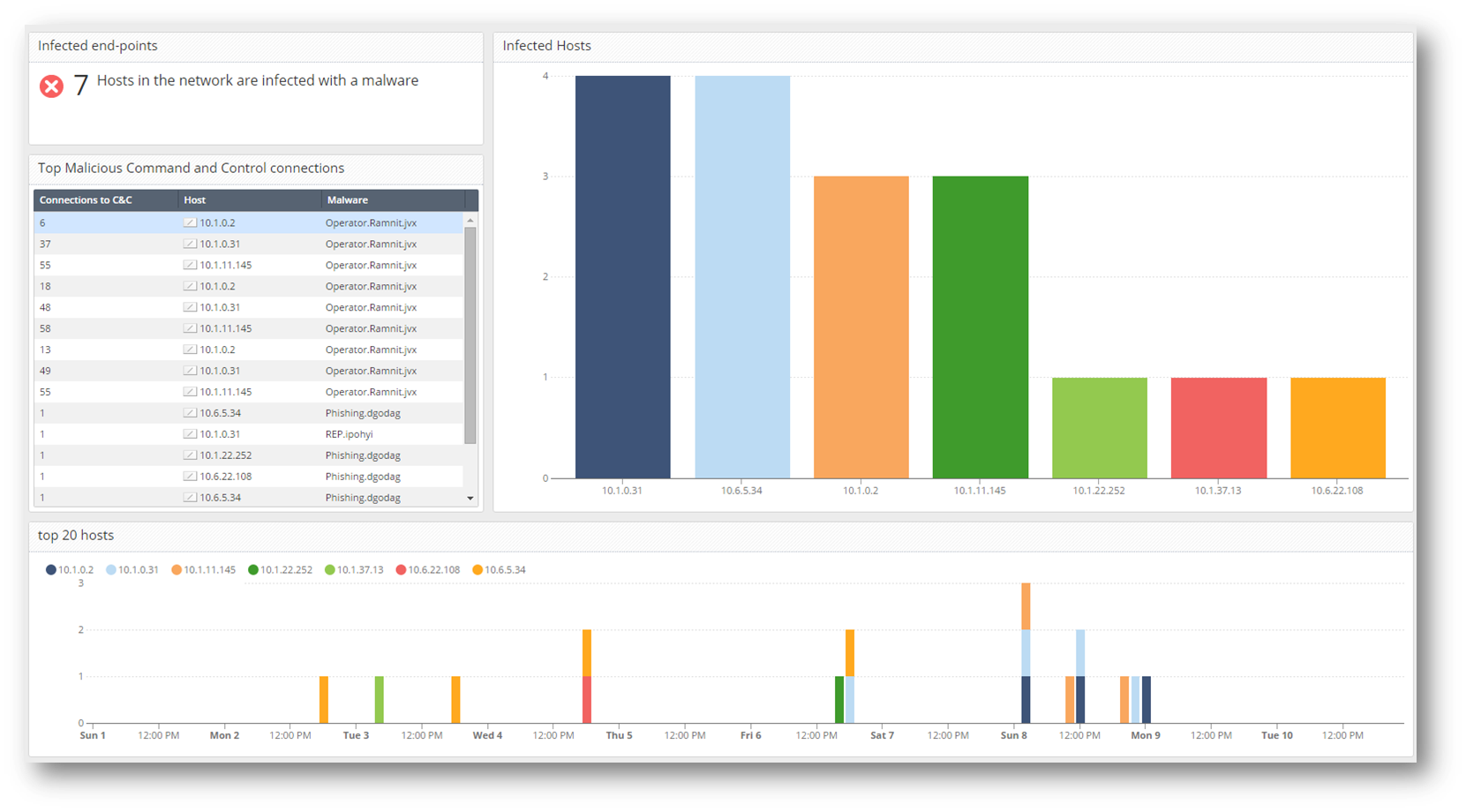
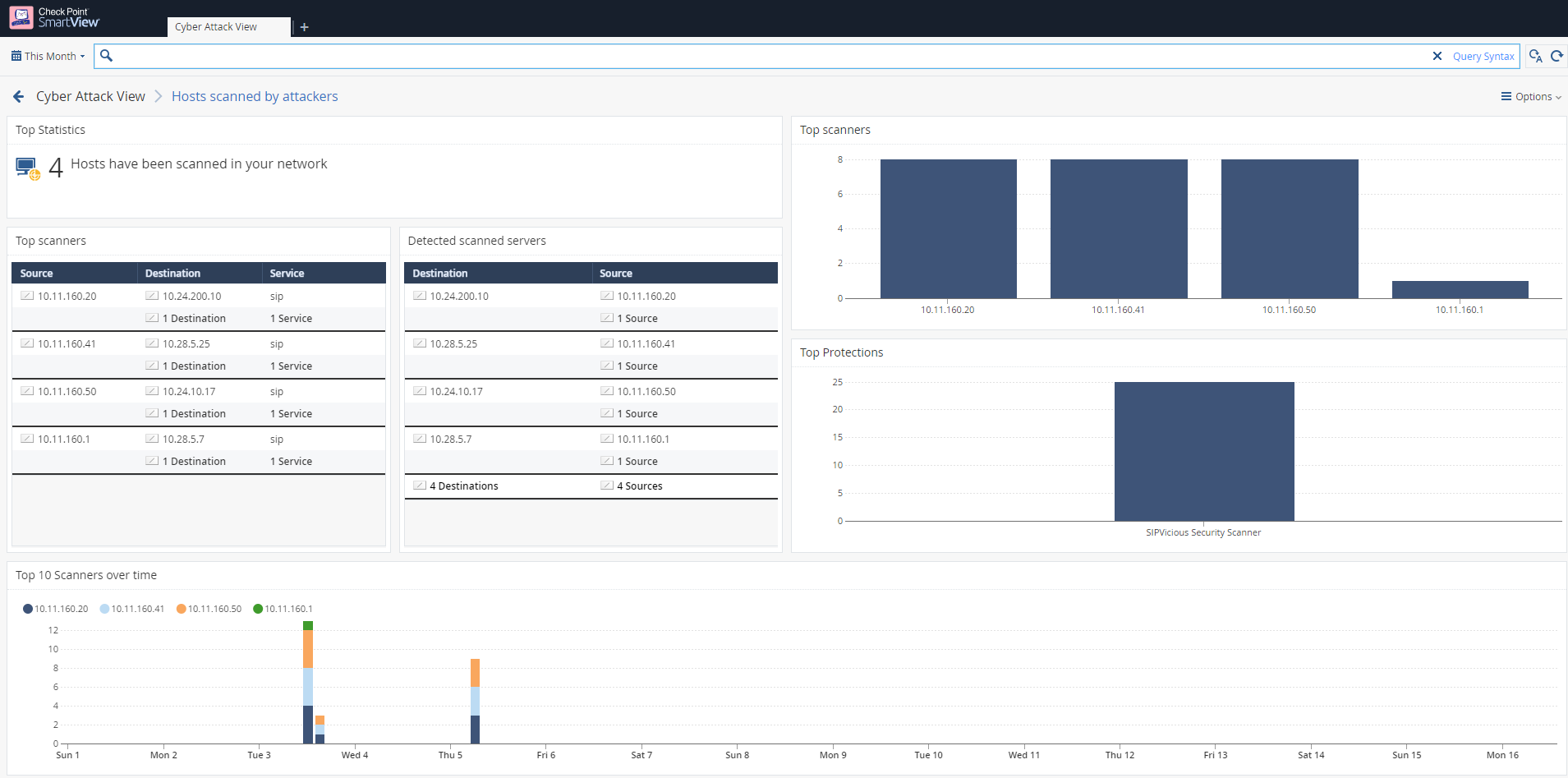
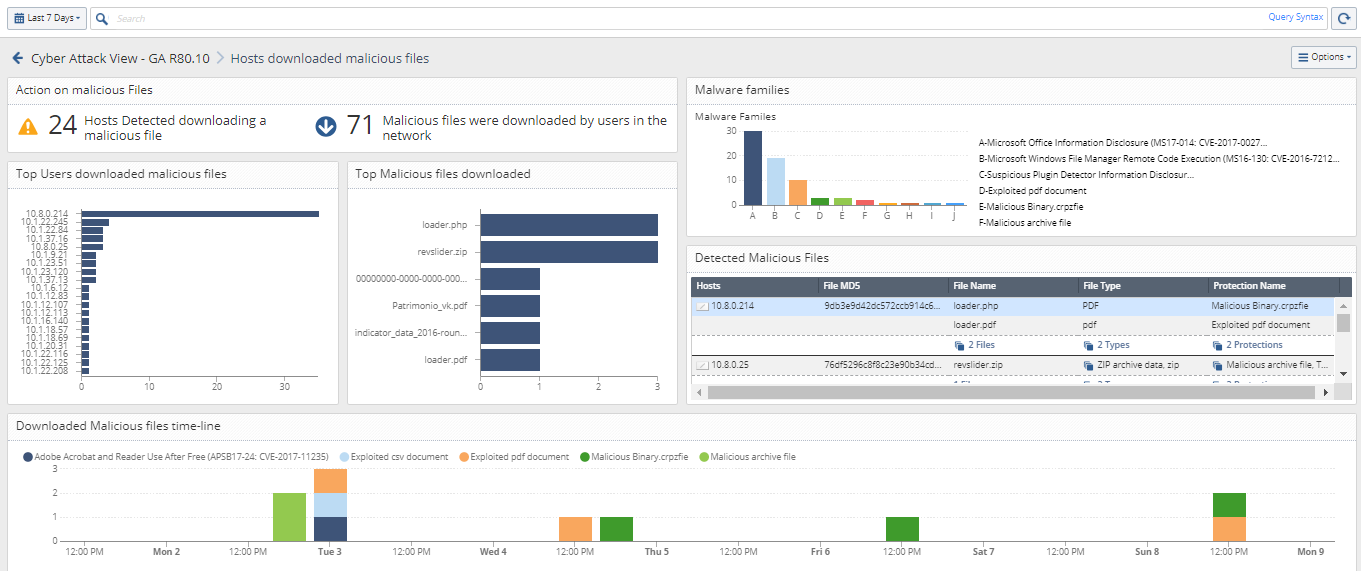
examples for all of the pages in the dashboard.
- Main page
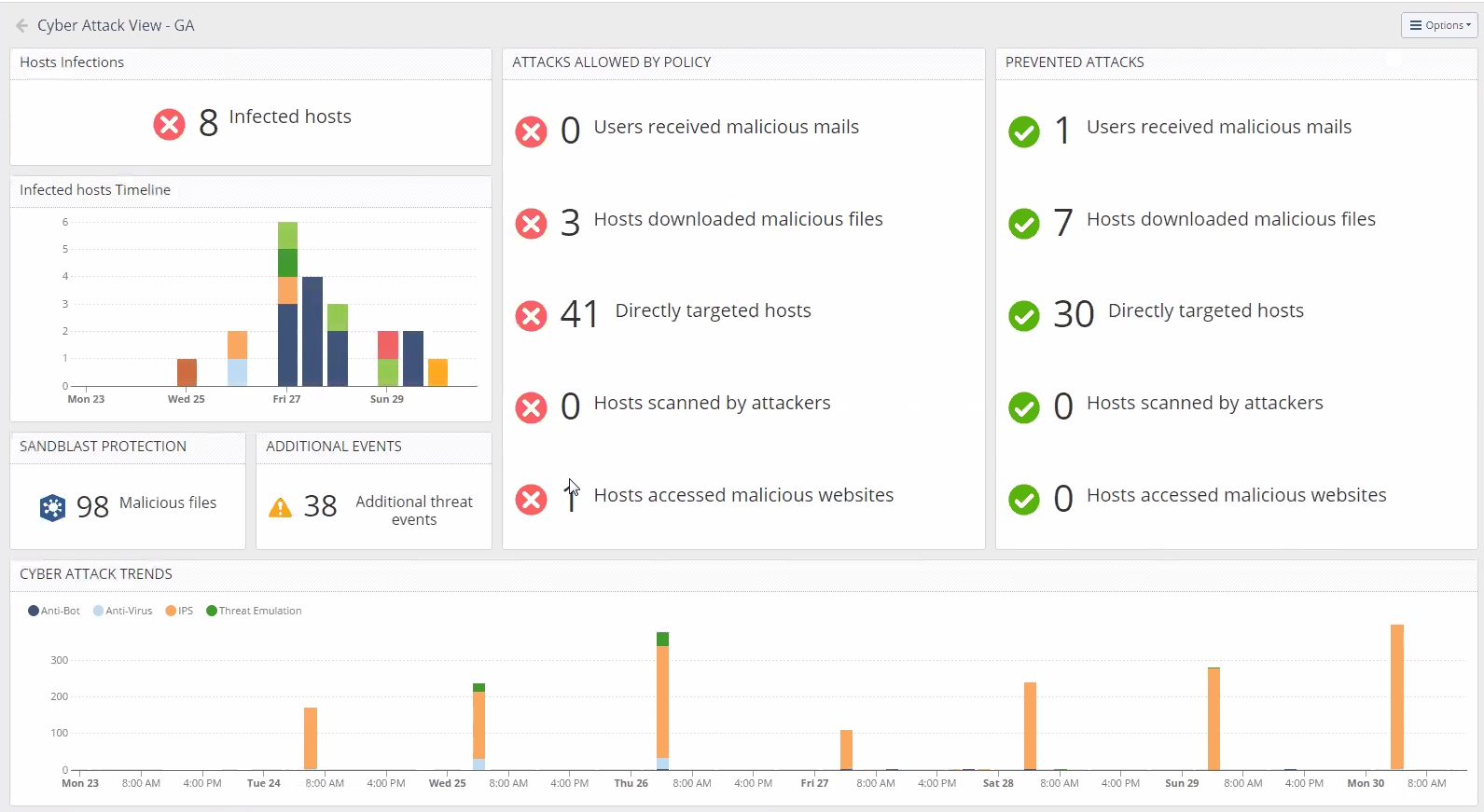
- Infected Hosts
- Reconnaissance action on your network
- Different delivery methods
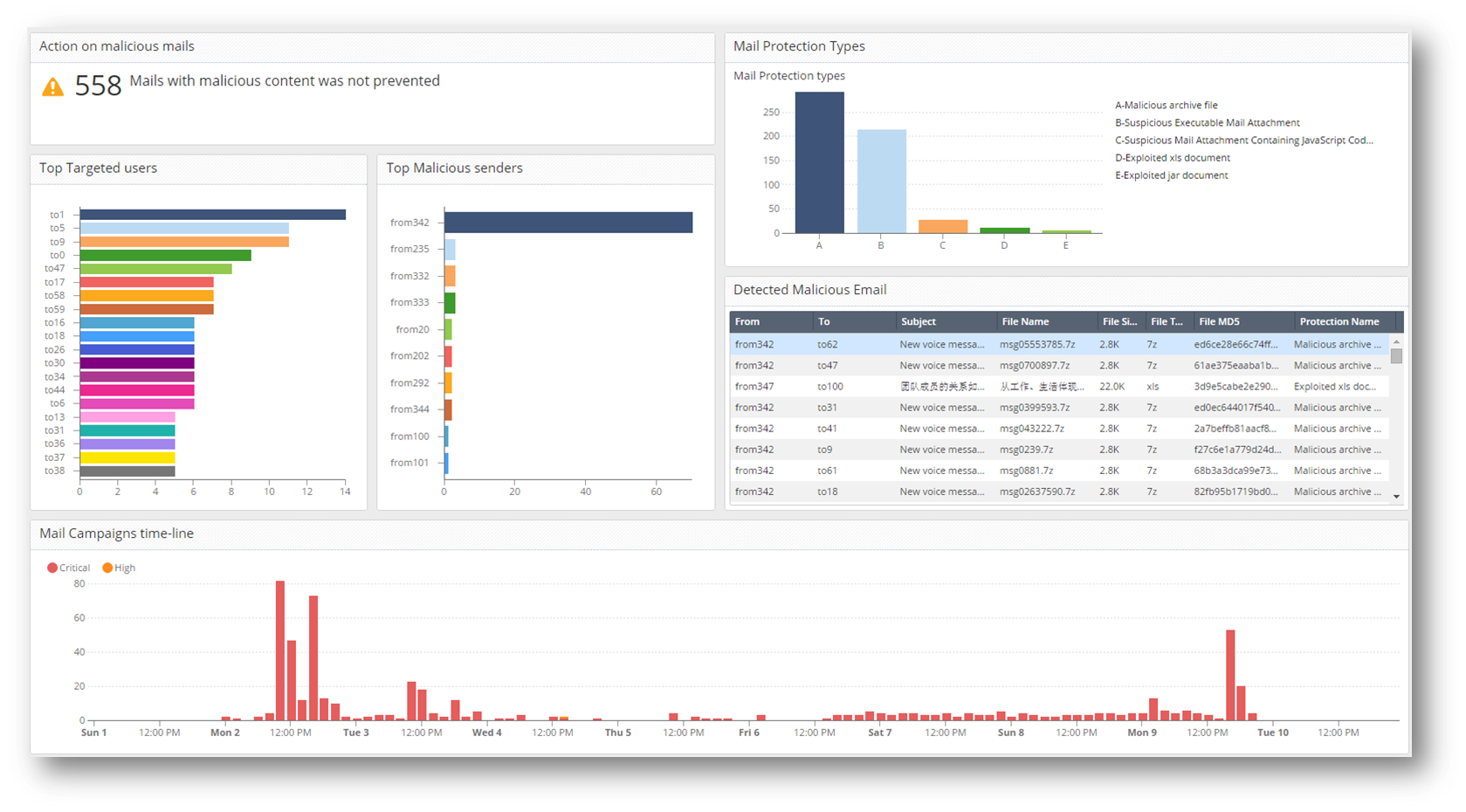
- Host exploit
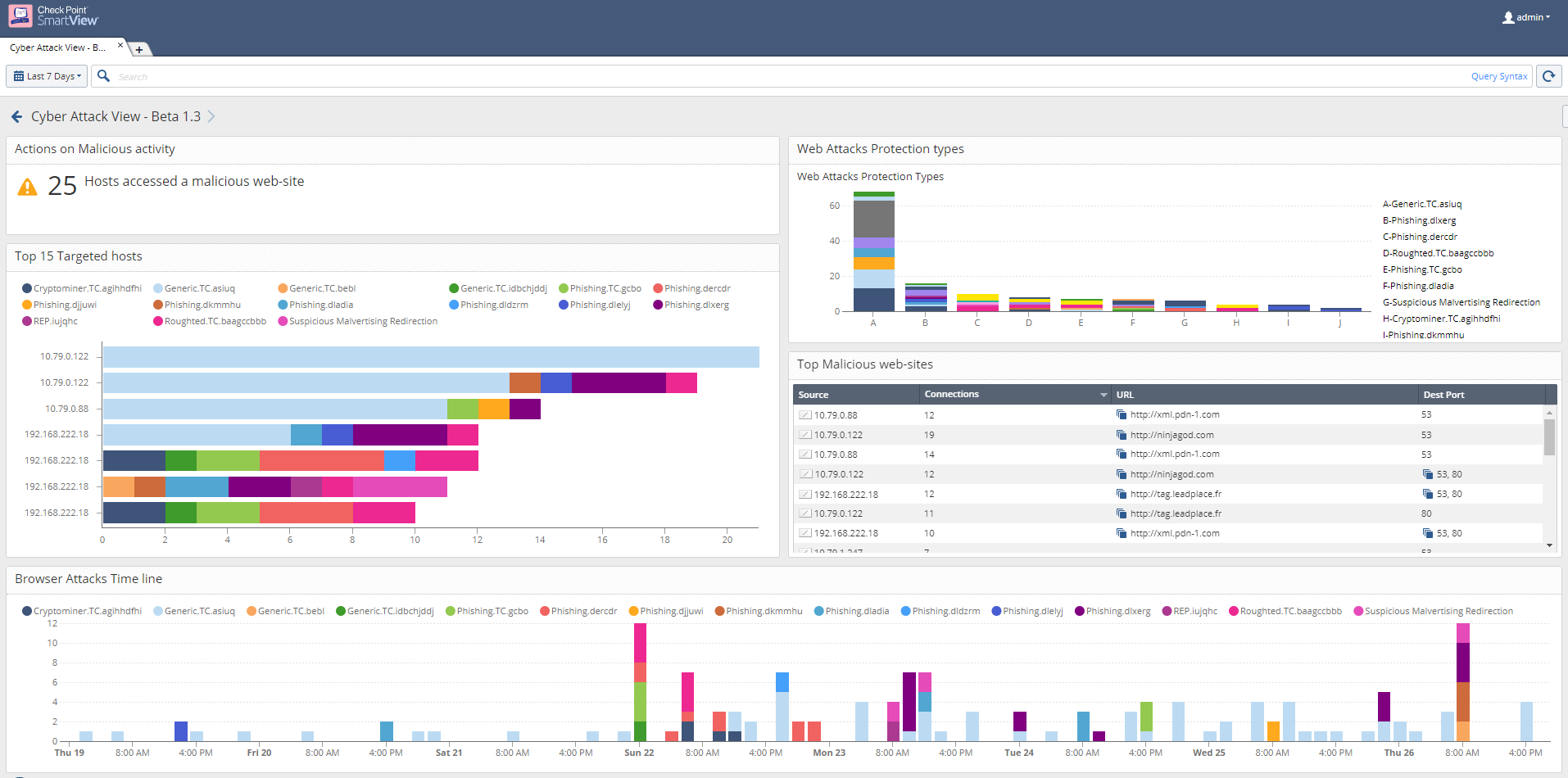
- Malicious Websites
Labels
- Labels:
-
Logging
-
Monitoring
-
SmartEvent
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello. You did great job!
I have one suggestion. It will be really cool if you add one more widget - The Map of Attackers. Something like this^

It will help to create a Geo Pollicy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
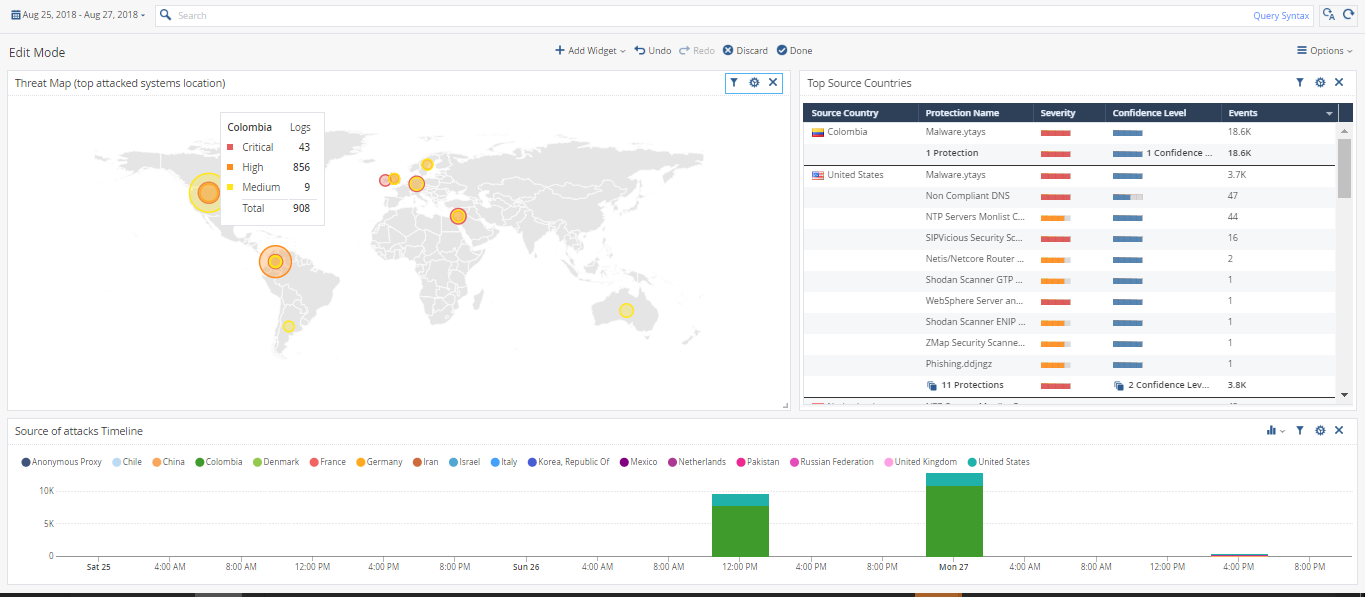
created basic one - something like that?
what should be the order and data that needed to be presented from you POV?
if you have use-cases, it will be the best (something like 'as an admin, i want to find/someone called me with a problem or need and i want to ********** and based on that do *******'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you please send me the template?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, this screenshot looks good. The main goal is to find what countries is attacking you. Maybe from this screen you will see a lot of attacks from Bangladesh or Kongo. After that you can create Geo pollicy and block all malicious traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
is that a view that related to threat prevention only? based on my work in SOC operations, they are working on top sources and destination and asking more questions:
- Top sources for traffic usage
- Top destinations (my organization) connection rate
- Top source Attack countries (where the attacker is located)
- Top attacked countries (where the customer is located)
based on your experience, we should connect it to Threat Prevention events or have a higher look on it? (access, Threat, VPN, etc...)?
Thanks,
Oren
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can't speak for everyone. But I think if we talk about 'cyber threat view', the only information we need is the map between security events and the country of its originate. After that we can start our investigation.
But it's only my opinion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
so something more like that?
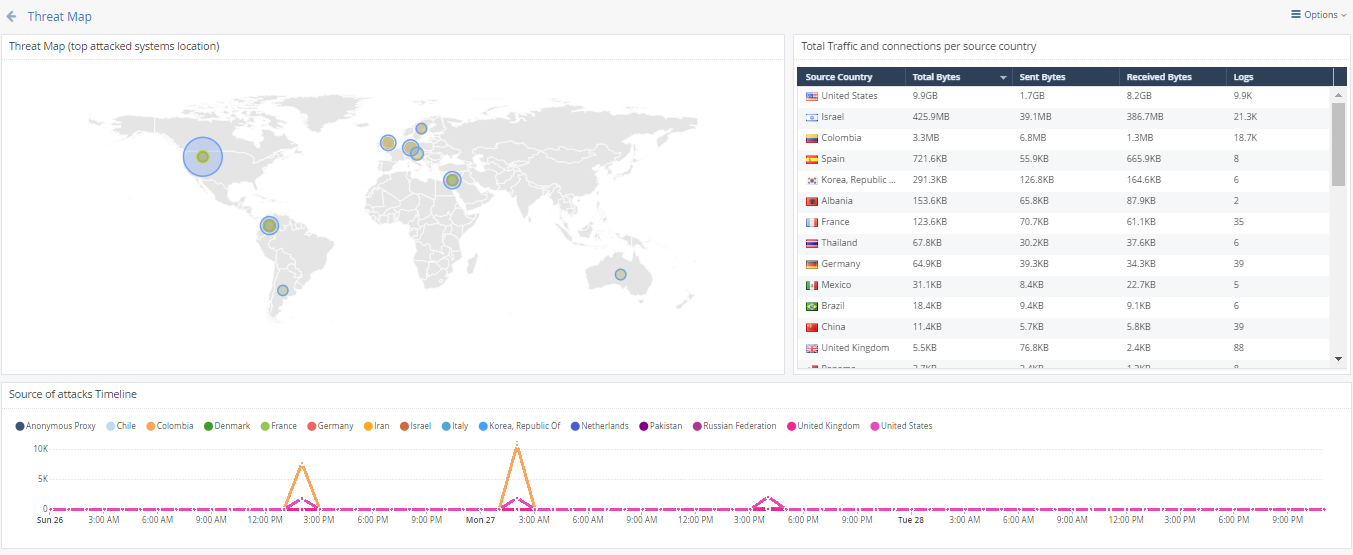
focus on threat but also presents the amount of logs and bandwidth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I like more your first screenshot. It's about security events
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
o.k
i will see how we can integrate the GEO view.
Thanks for the feedback!
Oren
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very useful this new View!
One question about the "Hosts accessed malicious websites" that is stated in the field "Attacks Allowed By Policy".
I see there always our internal DNS servers that tries name resolutions for phishing/infected websites. The protection "DNS Reputation" successfully blocks this -> OK. Why is that in this field "Attacks Allowed By Policy" when the DNS Reputation blocks it?
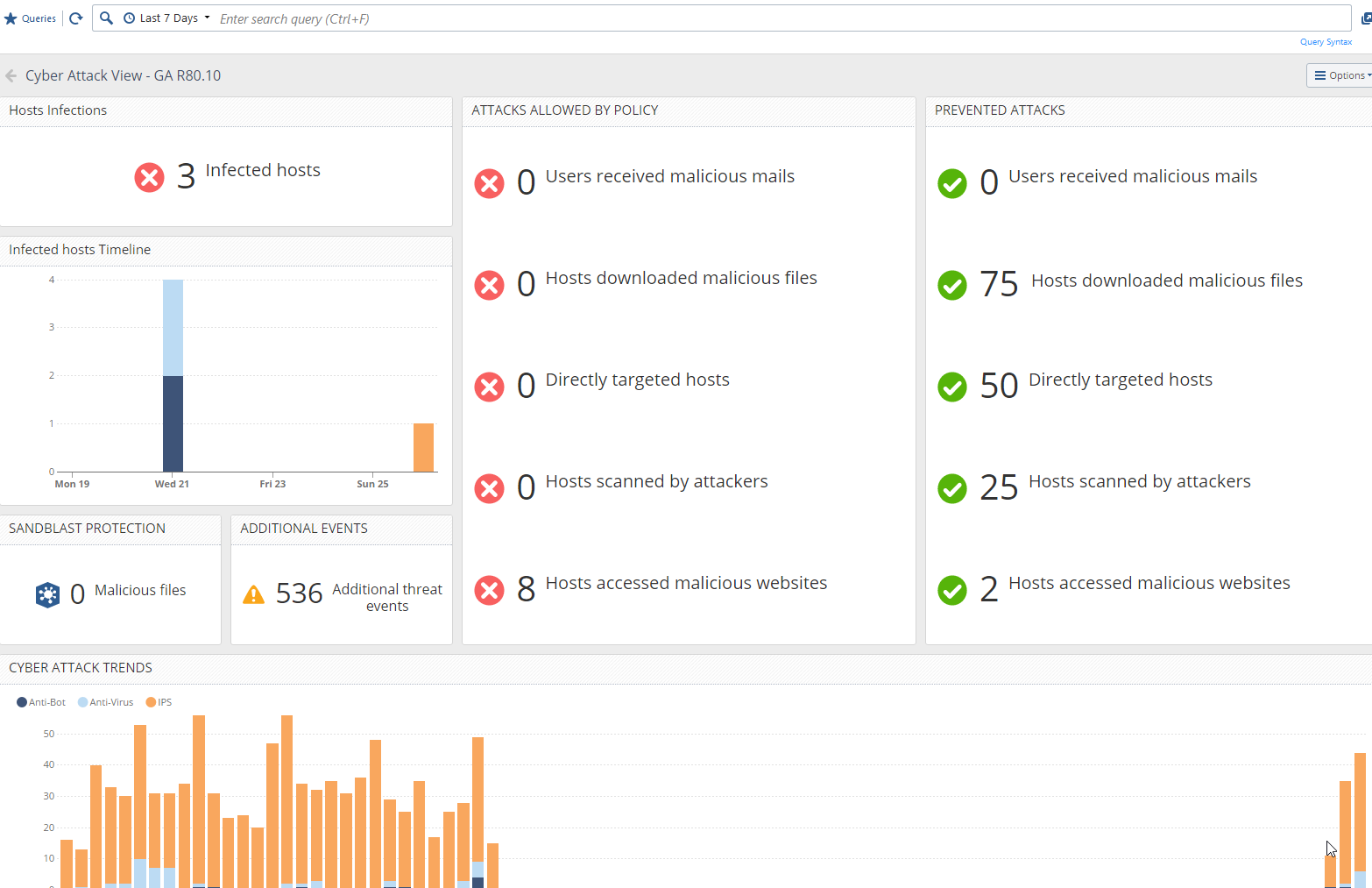
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
great job!
we've been using it for a long time and it's nice to see this becoming official GA!
keep up the good work!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 13 | |
| 13 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


