- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Who rated this post
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Think of iIoO as different stages of processing on the firewall, but bear in mind that these four inspection/capture points are only relevant to traffic that is not accelerated at all and is going through the Firewall Path (F2F); this is what the command fw ctl chain is showing. Unaccelerated packets that are permitted through the firewall will cross all four capture points. Traffic that is partially or fully accelerated (via the PXL or SXL paths, respectively) takes a "shorter" path across the firewall as shown in the diagram below excerpted from my book:
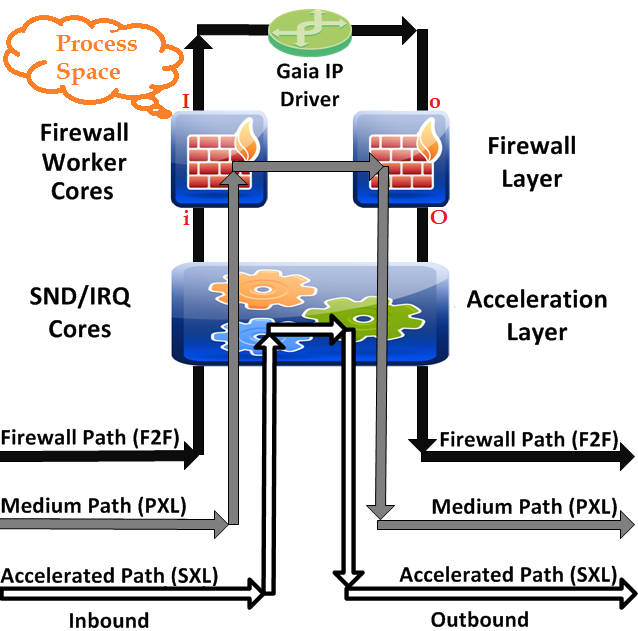
Not every Firewall Path operation below has its own dedicated chain module, and many of these operations occur inside the same chain module. The vast majority of firewall security operations (and possible drops) happen on the inbound/client side of the firewall kernel between "i" and "I" such as:
- Inbound Anti-spoofing
- Geo Policy
- HTTPS/VPN decryption
- Connections state table lookups
- Access Control policy layer evaluation
- Destination IP NAT
- Threat Prevention policy layer evaluation
Between "I" and "o" the Gaia IP driver performs routing.
Between "o" and "O" on the outbound/server side of the firewall kernel, the following types of operations occur:
- Outbound Anti-spoofing
- HTTPS/VPN encryption
- Source IP NAT
Obviously things get a lot more complicated if the traffic is accelerated; you can get a basic sense of how much traffic is accelerated on your firewall by running fwaccel stats -s.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Who rated this post
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


