- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Introduction to Lakera:
Securing the AI Frontier!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Who rated this post
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Custom Application/Site Findings
For years, I've been wanting to test Check Point's Custom Application/Site objects' matching logic. Finally got a chance to.
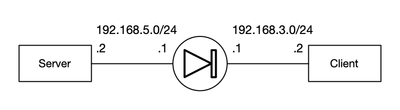
/etc/hosts on the client has these two lines added:
192.168.5.2 gooddomain.local subdomain.gooddomain.local
192.168.5.2 baddomain.local gooddomain.local.baddomain.local subdomain.gooddomain.local.baddomain.local
I built a self-signed certificate on the server and set up httpd(8) to serve a simple page via both HTTP and HTTPS using that self-signed cert. I build a small KSH script on the client with my test cases:
#!/bin/ksh
set -A domainsList "http://gooddomain.local/" \
"https://gooddomain.local/" \
"http://gOoDdOmAiN.lOcAl/" \
"https://gOoDdOmAiN.lOcAl/" \
"http://gooddomain.local:80/" \
"https://gooddomain.local:443/" \
"http://gOoDdOmAiN.lOcAl:80/" \
"https://gOoDdOmAiN.lOcAl:443/" \
"http://subdomain.gooddomain.local/" \
"https://subdomain.gooddomain.local/" \
"http://baddomain.local/" \
"https://baddomain.local/" \
"http://gooddomain.local.baddomain.local/" \
"https://gooddomain.local.baddomain.local/" \
"http://subdomain.gooddomain.local.baddomain.local/" \
"https://subdomain.gooddomain.local.baddomain.local/" \
"http://baddomain.local/gooddomain.local/" \
"http://gooddomain.local:password@baddomain.local/" \
"http://user:gooddomain.local@baddomain.local/" \
"http://baddomain.local/gooddomain.local" \
"http://baddomain.local/gooddomain.local/" \
for domain in ${domainsList[*]}; do
printf "%60s: " $domain
curl -k "$domain" >/dev/null 2>/dev/null
exitCode=$?
if [ $exitCode -eq 0 ]; then
echo "Success"
else
echo " Fail ${exitCode}"
fi
done
And finally, I set up the policy on the firewall (standalone, R81.10 jumbo 94) in the middle. Here it is in abbreviated form:
"rulebase" : [ {
"rule-number" : 1,
"source" : [ "Any" ],
"destination" : [ "Any" ],
"service" : [ "GoodDomain" ],
"action" : "Accept",
}, {
"rule-number" : 2,
"source" : [ "Any" ],
"destination" : [ "Internet" ],
"service" : [ "Any" ],
"action" : "Accept",
}, {
"rule-number" : 3,
"source" : [ "ClientNet", "ServerNet" ],
"destination" : [ "Outside Private (to reach my NTP server)" ],
"service" : [ "Any" ],
"action" : "Accept",
}, {
"rule-number" : 4,
"source" : [ "Any" ],
"destination" : [ "Any" ],
"service" : [ "SSH" ],
"action" : "Accept",
}, {
"rule-number" : 5,
"source" : [ "Any" ],
"destination" : [ "Any" ],
"service" : [ "Any" ],
"action" : "Drop",
} ]
"GoodDomain" is the Application/Site object I built for testing. HTTPS Inspection is not set up.
With the first rule's Application/Site object set to match "gooddomain.local" not as a regular expression:
obsd-client# ./domainTest.sh
http://gooddomain.local/: Success
https://gooddomain.local/: Success
http://gOoDdOmAiN.lOcAl/: Success
https://gOoDdOmAiN.lOcAl/: Success
http://gooddomain.local:80/: Success
https://gooddomain.local:443/: Success
http://gOoDdOmAiN.lOcAl:80/: Success
https://gOoDdOmAiN.lOcAl:443/: Success
http://subdomain.gooddomain.local/: Fail 56
https://subdomain.gooddomain.local/: Fail 35
http://baddomain.local/: Fail 56
https://baddomain.local/: Fail 35
http://gooddomain.local.baddomain.local/: Success
https://gooddomain.local.baddomain.local/: Success
http://subdomain.gooddomain.local.baddomain.local/: Fail 56
https://subdomain.gooddomain.local.baddomain.local/: Fail 35
http://baddomain.local/gooddomain.local/: Fail 56
http://gooddomain.local:password@baddomain.local/: Fail 56
http://user:gooddomain.local@baddomain.local/: Fail 56
http://baddomain.local/gooddomain.local: Fail 56
http://baddomain.local/gooddomain.local/: Fail 56
Not great. It allows some potential phishing domains.
With the Application/Site object set to match "gooddomain.local/":
obsd-client# ./domainTest.sh
http://gooddomain.local/: Success
https://gooddomain.local/: Fail 35
http://gOoDdOmAiN.lOcAl/: Success
https://gOoDdOmAiN.lOcAl/: Fail 35
http://gooddomain.local:80/: Success
https://gooddomain.local:443/: Fail 35
http://gOoDdOmAiN.lOcAl:80/: Success
https://gOoDdOmAiN.lOcAl:443/: Fail 35
http://subdomain.gooddomain.local/: Fail 56
https://subdomain.gooddomain.local/: Fail 35
http://baddomain.local/: Fail 56
https://baddomain.local/: Fail 35
http://gooddomain.local.baddomain.local/: Fail 56
https://gooddomain.local.baddomain.local/: Fail 35
http://subdomain.gooddomain.local.baddomain.local/: Fail 56
https://subdomain.gooddomain.local.baddomain.local/: Fail 35
http://baddomain.local/gooddomain.local/: Fail 56
http://gooddomain.local:password@baddomain.local/: Fail 56
http://user:gooddomain.local@baddomain.local/: Fail 56
http://baddomain.local/gooddomain.local: Fail 56
http://baddomain.local/gooddomain.local/: Fail 56
Worse, as it doesn't allow HTTPS.
Would anybody like to see other URLs tested? I plan to explore other matching expressions, and I plan to try to enable HTTPS Inspection.
Edit: I realized I should include the exit codes in case some failures are for things other than connectivity being prevented. And of course, I discovered that subdomain.gooddomain.local.baddomain.local was failing to resolve, so I added that to /etc/hosts on the client. Modifications made to the hosts file, the script, and the results above.
Edit 2: Added some phishy paths to the script and the results.
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter