- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Who rated this post
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.10 Site to Site VPN Config between two Gateways hosted in Azure - full documentation
I have documented here the Site to Site VPN config between two Check Point R81.10 Gateways hosted in Azure Cloud, managed also by Azure Hosted IaaS Security Management Server. Attached also the Word document.
Firewall deployment & VNET level configs, used for this VPN S2S setup are documented here:
Configuring Site To Site VPN between 2 Check Point Gateways hosted in Azure
Version 1.0
6 October 2022
Configuration description:
Firewall Management Servers
- A single Management server is managing both Gateways
Gateways
- westSG protecting VNET1 10.0.0.0/16
- northSG protecting VNET2 10.2.0.0/16
Services & VMs that need to communicate via VPN
- west-webserver hosted in VNET1 à subnet 10.0.2.0/24
- north-webserver hosted in VNET2 à subnet 10.2.2.0/24
Existing environment setup
- On both VNET1 and VNET2, the subnets where the webservers are hosted are configured as “Hide behind the Gateway”.
- This setting is the basic config for the Azure hosted assets to have Internet Access via the Check Point Security gateway à config on network object
- Automatic NAT Rules are enabled
- This setting is the basic config for the Azure hosted assets to have Internet Access via the Check Point Security gateway à config on network object
Existing configuration is documented here:
Site to Site VPN Configuration Steps
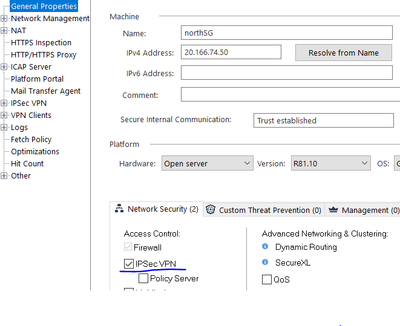
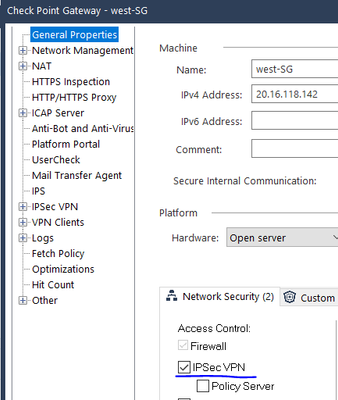
- Enable IPsec VPN software blade on both Gateways --> General Properies --> Network Security TAB --> Check The IPSec VPN tick box --> Click OK to save the configuration.
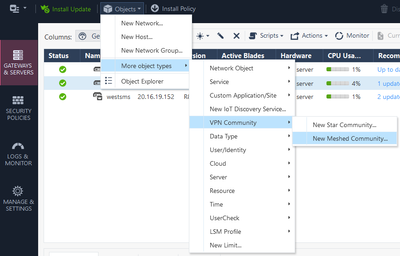
- Create a VPN Community object --> Objects --> More Objects --> VPN Community --> New Meshed Community
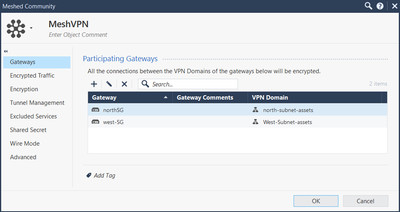
- Give a name to the VPN Community and add the two gateways and Click OK.
- The other default settings can remain default for this Check Point to Check Point VPN Configuration.
- Give a name to the VPN Community and add the two gateways and Click OK.
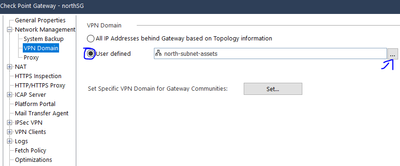
- Configure the VPN Domain for both Security Gateways --> Edit Gateway properies --> Network Management --> VPN Domain --> Select User Defined option --> tick the 3 dots in the right --> Select the subnet you want to use for the VPN. If the object for the subnet is not created, create it.
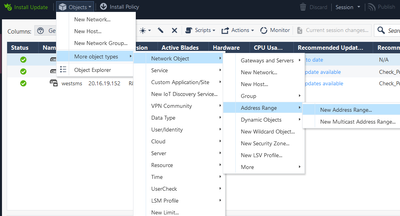
- If you do not want to use an entire subnet as VPN Domain, you can create and use Address Range objects.
- If you do not want to use an entire subnet as VPN Domain, you can create and use Address Range objects.
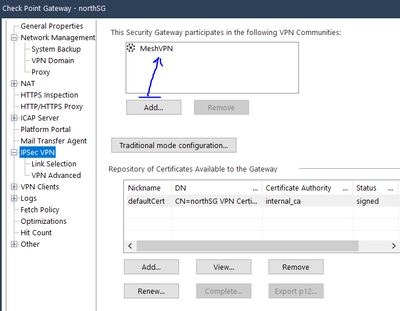
- Set the Scope of the VPN --> Gateway Properties --> IPSec VPN TAB & add the VPN Community you created earlyer
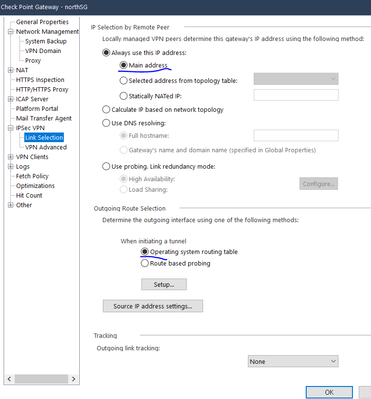
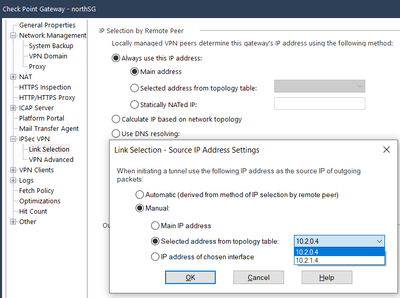
- Link selection --> Gateway Properies --> IPSec VPN TAB --> Link Selection under-TAB --> assure that Main Address is selected and Operating System Routing Table also.
- Link selection --> Gateway Properies --> IPSec VPN TAB --> Link Selection under-TAB --> Go to Source IP address settings --> Select Manual --> Selected addresses from topology table --> select the private IP of the eth0(external) of the Gateway
- Validate that Step 1 was configured on both gateways
- Validate that Steps 3, 4, 5 & 6 where configured on both gateways
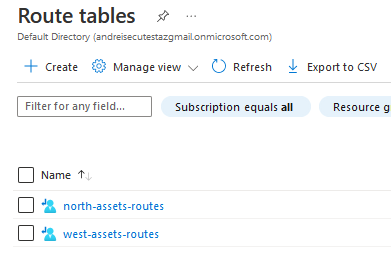
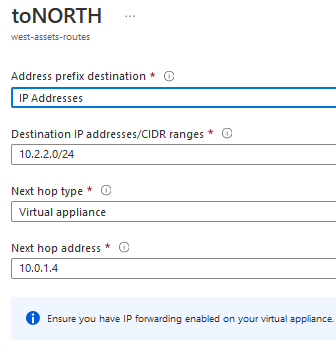
- Azure level routes --> In Azure Portal --> Go to Route Tables
- Edit the Route Tables for the subnets used in VPN Domain for both Gateways, in this case there are only two route tables as we have only a single test subnet in each Azure VNET
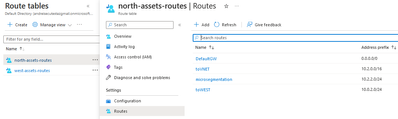
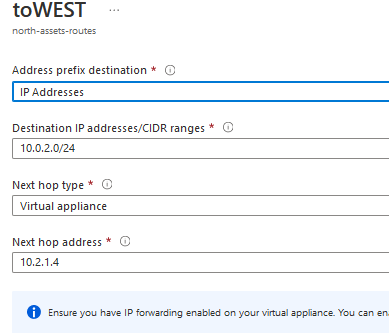
- On the Route Table properies, go to Routes TAB and add a new Route to reddirect traffic torward the other VNET’s subnet via the gateway’s eth1 private IP
- For the north-asset-routes, all traffic to west-webserver subnet assets will be reddirected via the north-SG eth1 interface IP
- For the west-asset-routes, all traffic to north-webserver subnet assets will be reddirected via the west-SG eth1 interface IP
- For the north-asset-routes, all traffic to west-webserver subnet assets will be reddirected via the north-SG eth1 interface IP
- Create Access Control Rules
- In SmartConsole --> Security Policy --> Access Control --> Policy --> I have created a single policy to allow traffic both ways(north-->west & west-->north) marking the previously created VPN Community with any service and marked as Allowed
- This policy was installed on both Security Gateways
- I used subnet objects both for Source & Destination as this is a test/Demo environment only.
- In real life, we will use host objects, host groups, Dynamic Objects and so on…
- Create Access Control Rules
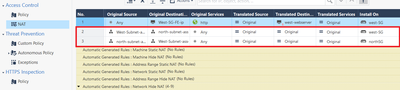
- In SmartConsole --> Security Policy --> Access Control --> NAT --> I have created two manual NAT rules
- This policies are needed because both assets subnet(north & west) have NAT configured --> Hide behind the gateway. Practically, this rules are an exception for the following Automatic NAT Rules(created automatically when configured NAT on subnet objects)
- We do not want that traffic from west-subnet-assets to reach the north-subnet-assets with northSG gateway eth0 private IP, but with it’s own subnet allocated IP --> as we need to filter traffic as much as possible.
- Do not forget to Publish & Install the policies on both gateways to implement changes & configs.
- Testing can be done by ping from a server hosted in west-subnet-assets to a server hosted in the north-subnet-assets and than from north to west.
- This policies are needed because both assets subnet(north & west) have NAT configured --> Hide behind the gateway. Practically, this rules are an exception for the following Automatic NAT Rules(created automatically when configured NAT on subnet objects)
- In SmartConsole --> Security Policy --> Access Control --> NAT --> I have created two manual NAT rules
- This policy was installed on both Security Gateways
- In SmartConsole --> Security Policy --> Access Control --> Policy --> I have created a single policy to allow traffic both ways(north-->west & west-->north) marking the previously created VPN Community with any service and marked as Allowed
Andrei Bosinceanu
https://www.linkedin.com/in/andrei-bosinceanu-34582358/
https://www.linkedin.com/in/andrei-bosinceanu-34582358/
Cloud Network Security
Cloud Network Security
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter