- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: R81.10 Single Gateway Azure deployment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.10 Single Gateway Azure deployment
Hi,
Testing the CG Network Single Gateway deployment in Azure.
Started following documentation "CloudGuard Network Security for Azure Demo Guide".
Setup:
1. Single Gateway - Standalone
2. Webserver
Configured UDRs to point webserver traffic to Security Gateway Backend IP(for VNET, internet, and subnet)
Configured NAT for webserver like in the documentation....what <<http>> req come on Security Gateway Frontend private IP is translated to Webserver.
Created allow policy from accessing webserver from internet.
Facing the following issue:
--> webserver does not reach the internet
--> I cannot access the webserver from internet
--> I see logs in the SMS both ways(from internet to SG and from webserver to internet) accepted, but neither way the goal communication is not started.
Is there any Single Gateway R81.10 Azure Deployment guide that I can follow to understand what I am missing here?
Any ideea about what is missing in the above setup?
Thanks,
A
https://www.linkedin.com/in/andrei-bosinceanu-34582358/
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Come back with the full Azure Deployment Guide for Single Gateway + Security Management Server.
Doc in Word, not yet been able to make it nice but is Step By Step deployment guide for anyone.
Hope you enjoy it and if requested, I will repost it in several weeks a bit more mice.
https://www.linkedin.com/in/andrei-bosinceanu-34582358/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The precise steps (with screenshots) you've taken would be helpful.
In terms of troubleshooting: have you done any packet captures on the gateway to see if the traffic is even traversing it? (e.g. with tcpdump or fw monitor)
That will help determine where the issue might be.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Azure Deployment performed steps
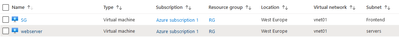
- Deployed Security Gateway – single gateway à Standalone – R81.10, BYOL.
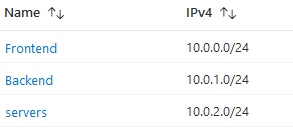
- This very deployment has created The VNET (vnet01 - 10.0.0.0/16) the resource Group in WestEurope (RG) and the SG required subnets (Frontend & Backend)
- This very deployment has created The VNET (vnet01 - 10.0.0.0/16) the resource Group in WestEurope (RG) and the SG required subnets (Frontend & Backend)
- Subnet “servers” has been created in order to host the linux webserver required for testing.
- Created required UDR&routes(myVNETroutes) in order to guide webserver traffic to gateway & linked the UDR to the “servers” subnet
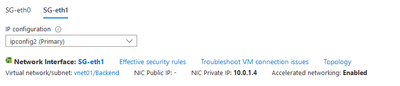
- Disabled Anti-Spoofing on both NICs of the SG
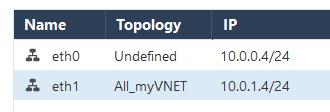
- Edited ETH1(internal) in order to be aware of my VNET
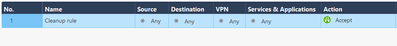
- I edited the cleanup rule and set it to allow any any allow&log, pushed the policy – this is just a POC environment for Azure deployment of CHKP CG Network
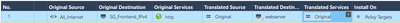
- Inserted new NAT config in order to translate any http requests incoming to eth0 to my webserver
- Published & Pushed policy.
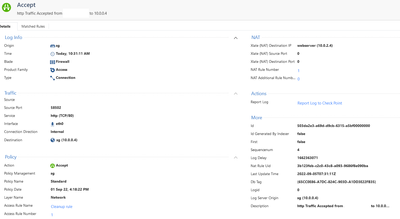
- From browser, if accessing my public IP with http :// in front, I receive timeout but in the logs I see the following
removed my public IP for privacy.
The ICMP request from webserver to 8.8.8.8 reaches the GS. Also the http request from my laptop reaches the SG.
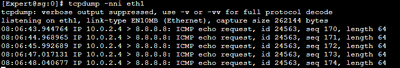
- Command: Tcpdump -nni eth0 port 80
- Result : 07:59:53.834148 IP myPublicIP.59992 > 10.0.2.4.80: Flags [S], seq 1959054956, win 64240, options [mss 64694,nop,wscale 8,nop,nop,sackOK], length 0
- Command: tcpdump -nni eth1
- Result: 08:03:50.896602 IP 10.0.2.4 > 8.8.8.8: ICMP echo request, id 24563, seq 1, length 64
- Cpinfo -y all
- This is Check Point CPinfo Build 914000215 for GAIA
- FW1 build number:
- This is Check Point Security Management Server R81.10 - Build 220
- This is Check Point's software version R81.10 - Build 883
- kernel: R81.10 - Build 793
- BUNDLE_DANA_AUTOUPDATE Take: 116
- BUNDLE_CPSDC_AUTOUPDATE Take: 21
- BUNDLE_PUBLIC_CLOUD_CA_BUNDLE_AUTOUPDATE Take: 18
- BUNDLE_NGM_DOCTOR_AUTOUPDATE Take: 15
- BUNDLE_GENERAL_AUTOUPDATE Take: 12
- BUNDLE_CORE_FILE_UPLOADER_AUTOUPDATE Take: 17
- BUNDLE_INFRA_AUTOUPDATE Take: 55
- BUNDLE_DEP_INSTALLER_AUTOUPDATE Take: 23
- BUNDLE_CME_AUTOUPDATE Take: 205
- BUNDLE_DC_CONTENT_AUTOUPDATE Take: 15
- BUNDLE_GOT_MGMT_AUTOUPDATE Take: 101
- BUNDLE_DC_INFRA_AUTOUPDATE Take: 30
- BUNDLE_WEBCONSOLE_AUTOUPDATE Take: 43
- BUNDLE_HCP_AUTOUPDATE Take: 57
- BUNDLE_GOT_TPCONF_MGMT_AUTOUPDATE Take: 36
- BUNDLE_GOT_TPCONF_AUTOUPDATE Take: 107
- Cpinfo -y all
- Result: 08:03:50.896602 IP 10.0.2.4 > 8.8.8.8: ICMP echo request, id 24563, seq 1, length 64
https://www.linkedin.com/in/andrei-bosinceanu-34582358/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it maybe an issue with the routing, since the Check Point is deployed with 2 NIC by default, the route tables in the Operating System needs to be aware how to use the ETH0 for External and ETH1 for Internal, this is because the interfaces are now like trunks or needs to know other Subnets/vNET by the next hop (the router inside the Subnet), this hop is always the first host of each subnet, so when you edit the UDR, are editing this router, but not the Machine and if we remember the Networking 101 where all the collision domains that are different require a router.
Looking at your screenshots, I can say the OS need this route.
set static-route 10.0.0.0/8 nexthop gateway address 10.0.1.1 on
PD: are you not seeing SYN errors or Stateful Inspection drops?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with @ChristianCastil. It is probably a routing issue. Does the CP GW know about the "servers' network? 10.0.2.0/24? Maybe you just need to add this network into the GW routing table?
https://yourgwip -> Network Management -> IPv4 Static Routes
or
SSH -> "show route"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I found the issue - deployment guide related - at step 5. Edited ETH1(internal) in order to be aware of my VNET
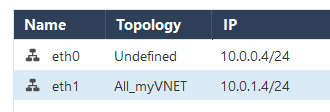
FIX: Edited eth0 and set it to "Internet(External)".
NAT to webserver is working now.
New situation I am facing now: internet access for VMs is not working.
1. UDR (route table) points all subnet traffic to internal nic ETH1 of the gateway.
2. All traffic is allowed on gateway
3. Seen that there is a difference in standard deployment from Marketplace, between "Single Gateway" and "Single Gateway - Standalone" and that is for the Standalone deployment there are Route tables both for Frontend and Backend subnets. The Internet access for VMs is still not working by default on none of them.
Troubleshooting is not an option as I want to reach straight deployment documentation so that our partners to have the confidence in deploying without any surprises.
Please, help me find the missing steps and then to have here a deployment doc head to toe.
Best wishes,
Andrei
LATER UPDATE
Internet access from subnets VMs solved as soon as I created the subnet object and set it as Hide behind gateway.
If some one of you is aware of an existing working full documentation here for this deployment, please share it here. Otherwise, I will post a full documentation in the next 2 days.
Best wishes,
Andrei
https://www.linkedin.com/in/andrei-bosinceanu-34582358/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Come back with the full Azure Deployment Guide for Single Gateway + Security Management Server.
Doc in Word, not yet been able to make it nice but is Step By Step deployment guide for anyone.
Hope you enjoy it and if requested, I will repost it in several weeks a bit more mice.
https://www.linkedin.com/in/andrei-bosinceanu-34582358/