- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Why does IPS protections set to Prevent show Detec...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Why does IPS protections set to Prevent show Detect in log?
IPS logs show only detect on protections which have action prevent on newly activated IPS blade.
The Access control policy drops this traffic destined to the external IF of the gateway, is this the reason for detect only action? I thought IPS policy was read before the access control policy. Am I missing something here?

1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
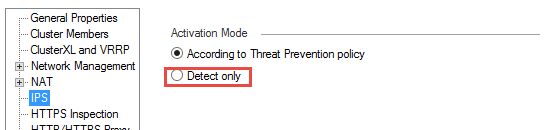
Your gateway is probably in "detect-only" mode:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed it's in 'detect only' mode. I actively decided to put new activations in staging mode so that I can check what updates do before i deploy them. I only help out this customer once a week so I wouldn't be able to deal with false positives on other days. So I thought that 'detect only' mode reflected that new activations go into staging.
But, I thought this would only affect future updates. When I check my IPS protections, there are none in staging mode. This is what puzzled me.

I'll change to 'According to Threat Prevention policy' instead! That shouldn't untick the staging box under updates I suppose.
Thanks to both of you Benjamin and Günther!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By default in most IPS Profiles, newly–downloaded ThreatCloud IPS Protections are set to Detect via “Staging Mode”. IPS Protections in Staging Mode are in a provisional mode and will not start preventing traffic until configured to do so by an administrator.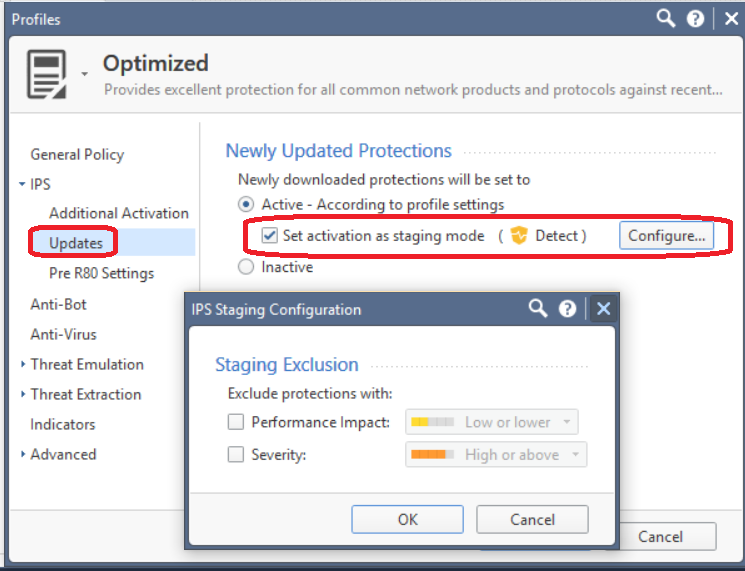
This is from Timothy Hall and found here https://community.checkpoint.com/thread/10122-another-smartconsole-usability-issue
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Having an issue with IPS that is similar, and mode is According to the Profile. The threat should be prevented but is not. The profile is circled in red (prevent) but we get a Detect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is the mode set to Background (Rapid Delivery) on the APCL/URLF Filtering Settings & Threat Prevention Engine Settings screens under Manage & Settings...Blades in the SmartConsole?
Also are you sure in that log card it matched against the ...Optimized-Prevent profile? Can't see that in your screenshot.
Also do you have the IPS bypass feature enabled?
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, background is the Website categorization mode. Not sure what that would have to do with IPS?
Yes, is going against the Optimized Prevent and have a open TAC case as well and they confirmed.
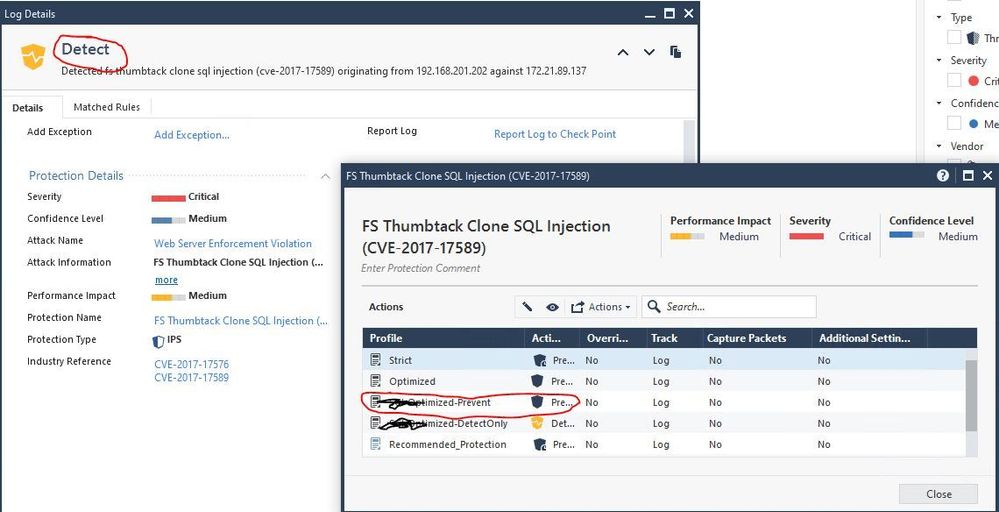
Yes, Bypass IPS inspection when gateway is under heavy load is checked. Below are all the actions taken on the Web Server Enforcement Violation. Some detect and others prevent on the same policy and exact same IPS protection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Those logs can't all be for one IPS protection, as the severity and confidence rankings are different on different lines.
I assume you have checked for any rule-based or global exceptions. Also look in the matching TP profile under IPS...Additional Activation and check what is configured there, although normally this would Inactivate a protection and not set it to Detect.
Beyond that I'll need to see the full log card for a Prevent and another one for Detect on the same IPS signature, and your TP policy containing the rule matching this traffic. You can PM it to me if you wish.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter