- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: Moving from Detect to Prevent TechTalk: Video,...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
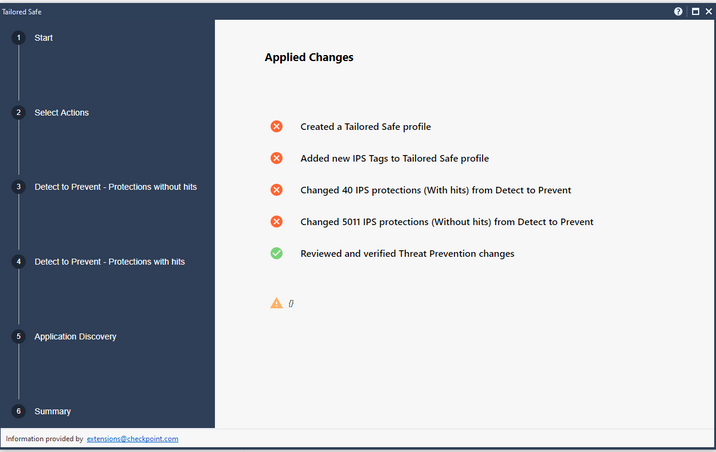
Moving from Detect to Prevent TechTalk: Video, Slides, and Q&A
On 8th January 2020, @Oren_Koren gave us a preview of a SmartConsole Extension that will be launched at CPX 360 2020, making it simple to move from Detect to Prevent with Check Point!
The following is available to CheckMates members who are logged in:
- Slides (will be provided after CPX 360 2020)
- Video
Q&A will be posted as comments.
The SmartConsole Extension mentioned: https://secureupdates.checkpoint.com/appi/tailoredsafe/extension.json
49 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Excellent presentation! This will be very useful for me.
I just ran the extension and receive these errors. I approved every pop-up.
Manager - R80.30
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey
if u can send me a direct email, I will take care of it
orenkor@checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks like a "cosmetic" error more than a real error.
Best to email Oren as he suggested so we can investigate.
Best to email Oren as he suggested so we can investigate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's not creating the new profile either. i'll wait on Oren to get back to me.
thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey
We are reviewing it and A short remote session will assist us to finish up the review and fix what is needed
I have seen your email, will respond soon and if it’s a possibility from your side, can we have a short session?
We are reviewing it and A short remote session will assist us to finish up the review and fix what is needed
I have seen your email, will respond soon and if it’s a possibility from your side, can we have a short session?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, i will send you email w/ my available times. Again, thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
did you solve the issue?
got the same issues (all errors, no tailored safe profile being created).
but it was just a first test in my lab.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey,
we have worked on all of the issues that has been sent by you and the others. a new version was release with bug fixes two days ago (same link so no change is needed). can you check again and tell me if it is still doesnt work for you?
Thanks,
Oren
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Worked like a champ. Thanks guys!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
its all on @asafga head 🙂
Asaf - do you want to update on the fixes has been added to the last TS version based on the community inputs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey all,
I wanted to update on our new improvement to TailoredSafe.
- We have reduced the pop-ups in the flow of the extension.
- Improved error handling – we will be able to handle errors much efficiently.
- Fixed a bug with the non-hit protections – based on inputs from the community, we have located few use-cases that we didn’t have in our lab and fixed them accordingly.
- Multiple code improvements.
I would like to add that CheckMates assists a lot with checking and giving us lots of feedback – please keep the feedback coming!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great presentation. I am looking forward to seeing more about it at CPX2020. I did install the extension on my SmartConsole and went through the wizard and it worked. I was a little surprised to see that I had 0 items that were in detect with no hits. I am running the Optimized profile (which I cloned so I could start customizing it for our environment) and I was expecting to have a lot of No Hits based on the presentation. If there is anything else I can provide on this, let me know.
Charles
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same here with one of my customers on the Recommended_Profile. 0 protections with no hits, 0 protections with hits, 0 Application Discovery.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Andreas,
Can you send me a short email with your details? We will want to review it with you
Thanks,
Oren
Can you send me a short email with your details? We will want to review it with you
Thanks,
Oren
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Charles
Thanks for the feedback
If you can please send me a short email so we can coordinate a short session, that will be great!
Thanks for the feedback
If you can please send me a short email so we can coordinate a short session, that will be great!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cdurham,
I got the same screen. Went for a cup of coffee from my desk and after 10min I saw 4500 changes in the session pane (in top of the Dashboard).
I could see this number increasing for the last 1000. Because there was no button to click ok or anything else, I closed the window and was able to publish and install policy. There was no chance to review the changes.
Wolfgang
I got the same screen. Went for a cup of coffee from my desk and after 10min I saw 4500 changes in the session pane (in top of the Dashboard).
I could see this number increasing for the last 1000. Because there was no button to click ok or anything else, I closed the window and was able to publish and install policy. There was no chance to review the changes.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Wolfgang,
By review the changes you mean that you want to verify what are the changes before the push policy, correct?
If we were able to show you the changes in any place and way in the console, what would be the best scenario/solution for you?
By review the changes you mean that you want to verify what are the changes before the push policy, correct?
If we were able to show you the changes in any place and way in the console, what would be the best scenario/solution for you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey chduram,
Can you please check if a new profile was created?(so I will differentiate between the presenting side and the configuration side)
Thanks
Oren
Can you please check if a new profile was created?(so I will differentiate between the presenting side and the configuration side)
Thanks
Oren
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are working very fast on reviewing all of your inputs
I will ask you to run the extension and if there is any challenge, send me an email - we want to know
please check if a profile was created in your threat prevention policy - in some cases, as Phoneboy said - it’s a bit of cosmetic thing and time manner (waiting time of few minutes for the changes to be created)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey all
in the past few days we have had multiple sessions with community members that includes debugging and understanding the reasons of fail in the extension
for the ones who didn’t had a session OR doesn’t have a session with R&D in the schedule to review the challenge and solve it (+learn what is the improvement we need to deploy) - please drop me an email and we will schedule a session to solve it WITH you.
as I said to all of the customers we have had a session with - the power of the community with reviewing our innovative products and the great inputs are priceless
let’s keep working together to make the best products based on your real needs!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally had the time to go through the video, nice tool!
From an optimization perspective this tool can be very helpful as well, since an action of Detect instead of Prevent or Inactive causes higher overhead on the firewall; this concept was hit hard in the latest version of my book. Particularly bad is an action of Detect but no logging, which is just consuming firewall resources for no valid reason. Good to see there is an automated tool to streamline getting out of Detect mode, my book goes through doing it manually. Will definitely add this tool to the upcoming addendum!
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks!
if you will add it to your book as a way to utilize Threat Prevention, that will be great 🙂
any input on the process is welcomed - we want to make our customers life simple and with no business impact
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where can I download the extension from to have a go in a lab with it?
Cheers
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But is it recommended to activate as much protections as possible? For example I activate all protections for McAffe, but we don't use any McAffe solutions in our organization. Doas it make sense? Or did I just create Performance impact for my gateway?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey,
as a basic rule, from our experience, some one in your organization can /will install something new tomorrow.
the challenge of managing the applications that are in use in your organization (+vulnerable versions) is a hard challenge.
to make it simple, we recommend to enable all the protections (beside exceptions if needed OR if you have performance issues due miss-sizing as an example)
just for example, lets say you do not have SQL today, but tomorrow someone from the DEV team will install a local instance with a known vulnerability:
sql will not be seen in d_port 1433 so you will not have any inspection == no performance usage
in the second the user will install the app and an attack will accure, only then you will have an inspection.
in some unique cases, i have seen customers that enable ONLY the tags for the applications they have, in those cases, they had a dedicated person that this was his job - its all about man-power...... (IMHO)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Oren
Great video, just a followup I think I am missing something.
I was under the impression that if you don't need a protection to not enable it, that if you enable it will launch the content inspection to, steam,parse,cmi protections, looking for traffic that might match this protection.
example: when ssl poodle vulnerability come out, We added protection for it., because the servers were vulnerable, but once the servers are patched , OS was patched, then there was no more need to keep the protection enable any more,
I think maybe my confusion might be related to performance, maybe I have been here to long and the engine has change
but I remember having a customer with worm catcher protection enable, and this was spiking up all the cpu high, because ALL http traffic was being inspected for a worm, when customer patch his window servers, against code red/nimba vulnerabilities, then we disable worm catch and his cpu went down.
thanks,
Manuel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mentions of Code Red/NIMDA put you back in the days of SmartDefense (pre-R70).
It's fair to say things are quite different now than they were back then. 😁
It's fair to say things are quite different now than they were back then. 😁
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewTue 28 Oct 2025 @ 12:30 PM (EDT)
Check Point & AWS Virtual Immersion Day: Web App ProtectionTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewTue 28 Oct 2025 @ 12:30 PM (EDT)
Check Point & AWS Virtual Immersion Day: Web App ProtectionThu 30 Oct 2025 @ 03:00 PM (CET)
Cloud Security Under Siege: Critical Insights from the 2025 Security Landscape - EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter