If you have Activation Mode set to "Detect Only" (formerly known as Troubleshooting Mode) and not "According to policy" on the gateway/cluster object, it doesn't matter whether your log4j protections are set to Prevent even with a user override, it will still act like Detect.
You could simply create a new TP profile, manually set everything except the log4j signatures to Detect or Inactive, put this new profile in a rule at the top of your TP policy, and disable all other rules in your TP policy. However this will not allow you to continue tuning on your existing TP profiles in anticipation of moving to full Prevent mode.
If you want to keep your existing profiles and continue tuning them in anticipation of going full Prevent eventually yet still have log4j in Prevent mode, there is not an easy way to do this but here is a workaround:
0) Take a backup of your SMS just in case.
1) Look at your Threat Prevention policy rules and determine all TP profiles in use by your gateway(s). If for some reason your gateway's IPS functionality is still implemented in the legacy "IPS" layer, there can be only one TP profile assigned to the gateway for IPS functionality. Let's assume for this example that two profiles are being used: Optimized and Strict.
2) In both the Optimized and Strict profile properties, check the IPS...Updates...Newly Updated Protections screen, and make sure that the Set Activation as Staging Mode checkbox is set for now. This will ensure that any newly downloaded protections go into Staging/Detect mode while in this special period of only log4j being Prevent. Obviously this box should be unchecked once you move from "Detect Only" to "According to Policy", make sure you don't forget about it! Note that if the log4j protections get updated by Check Point they will automatically move back into Detect if this is set, so you'll need to weigh the risk of some other newly-downloaded Protection getting put in Prevent mode automatically vs. the log4j Protections going back into Detect if they get updated.
3) Go to the IPS Protections screen. Sort the Optimized column until Prevent actions (blue shield) are at the top of the list.
4) Make a note of any protections that currently have an administrator override set by clicking User Modified under the Filter tab on the right. Take a screenshot of any overrides already in place. Clear the User Modified checkbox.
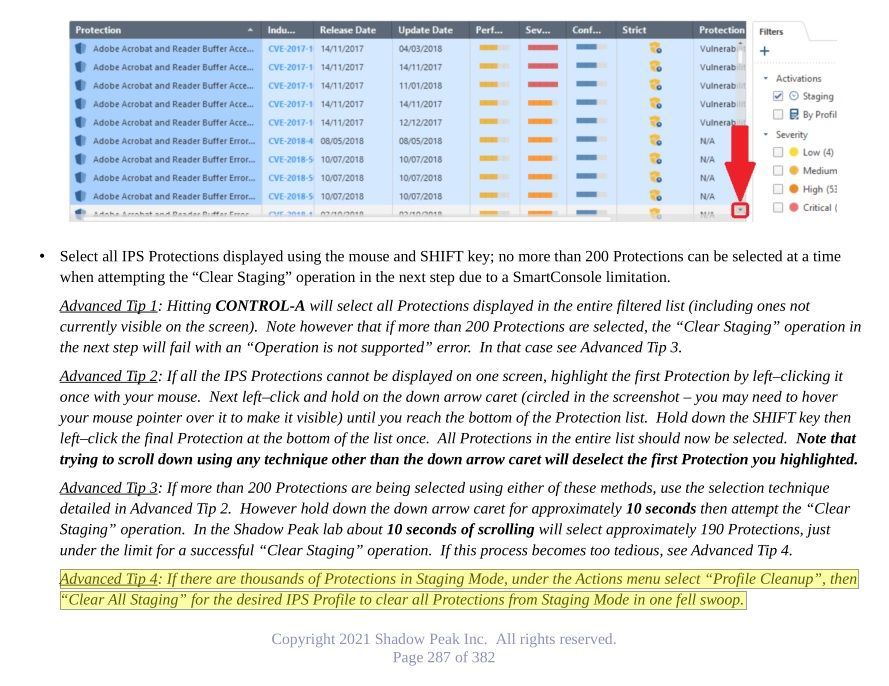
5) Now the painful part, bulk-select up to 200 Protections currently set for Prevent, then click Actions...Selected Protections...Detect Selected. You should get a popup warning about being applied to all visible profiles (which should be both Optimized and Strict in our example which is fine), and click OK. The bulk select is a bit clumsy here, see the screenshot from my IPS/AV/ABOT Immersion class below for tips.
6) The overridden protections will jump down to the bottom of the sorted list and not be visible on the screen any more, select the next 200 or so protections set for Prevent and repeat until there are no more protections under Optimized/Strict showing Prevent (blue shield). Make sure you don't accidentally set any protections under Optimized/Strict currently set as Inactive to Detect with your override actions.
7) Now locate the two log4j protections and override them to Prevent. Once again, double-check via sorts on the Optimized and Strict columns that only the log4j protections are showing a blue shield.
8 ) Change Activation Mode on the gateway to "According to policy", then publish and install the TP policy. Using a blade:ips filter in the logs, immediately make sure that no IPS signatures other than log4j are being tripped in Prevent mode.
Now let's assume that some time has passed and you have achieved reasonable certainty in the rest of your IPS configuration with exceptions and such, and you are ready for full Prevent mode on the gateway:
1) Go to the IPS Protections screen, and under Actions select Cleanup options...Profile cleanup. Click "Remove all user modified". Under Select Profiles pick Optimized and Strict (or whatever profiles you are using), then click OK.
2) Manually re-implement any User Overrides noted in step #4 above.
3) Uncheck the Set Activation as Staging Mode checkbox in all utilized TP profiles.
4) Publish and reinstall the TP policy.
Here is the screenshot showing bulk-selection tips for IPS Protections from my IPS/AV/ABOT Immersion course, it was talking about bulk clearing of the Staging flag but the techniques apply here as well:
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course



