- CheckMates
- :
- Products
- :
- Quantum
- :
- Threat Prevention
- :
- Concerning on blades policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Concerning on blades policy
Hi Team,
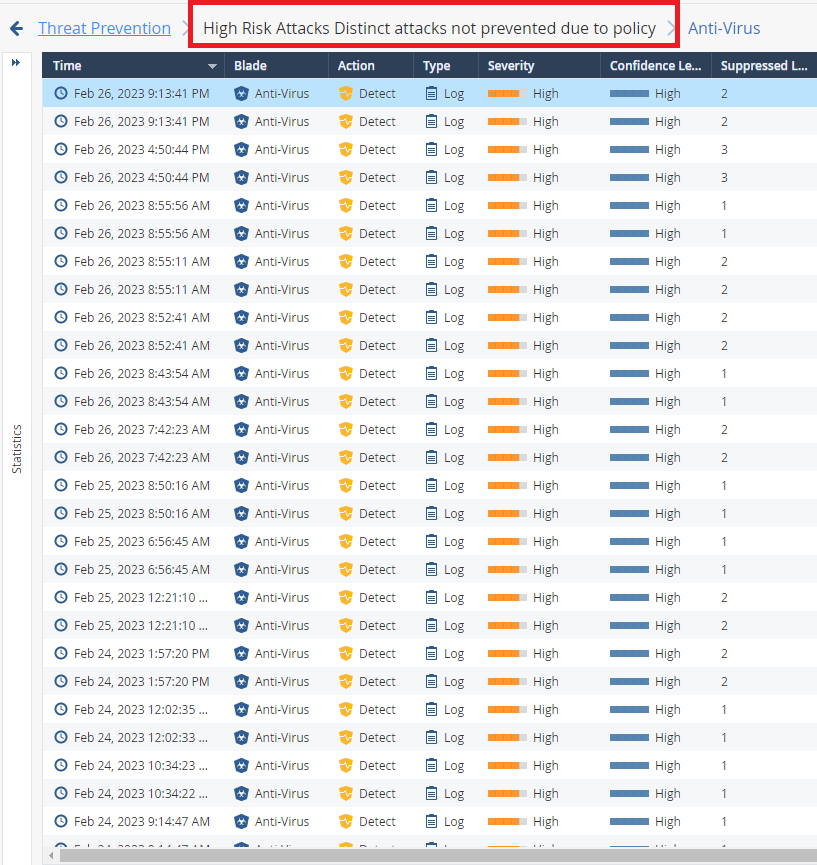
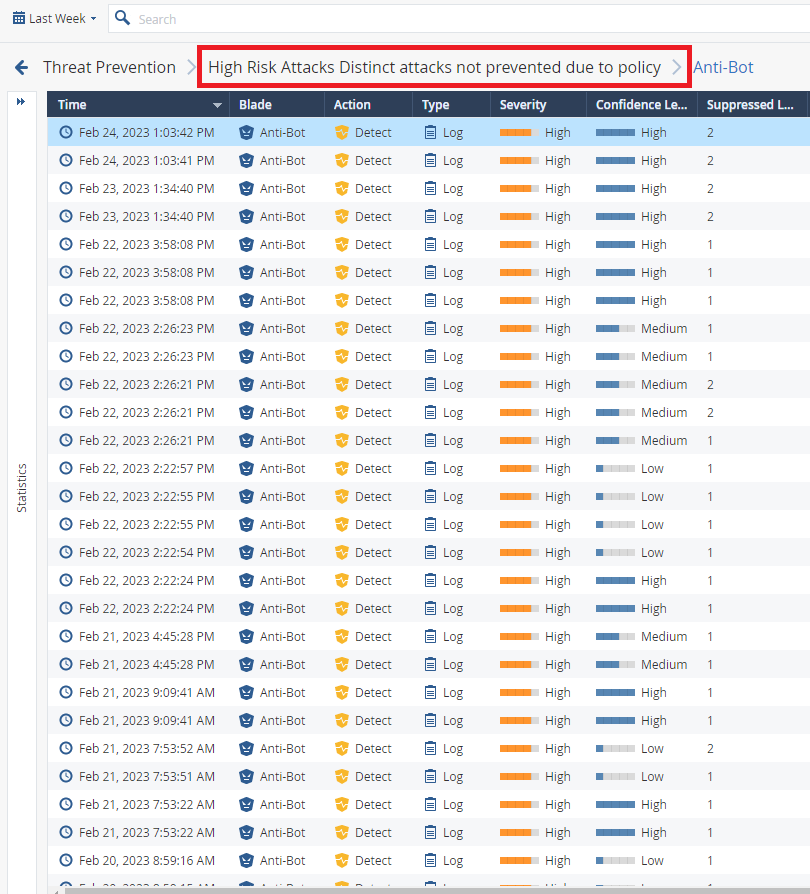
Could you explain log as below pictures?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We previously discussed similar here:
What is different on the expanded / detailed log cards?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Chris_Atkinson ,
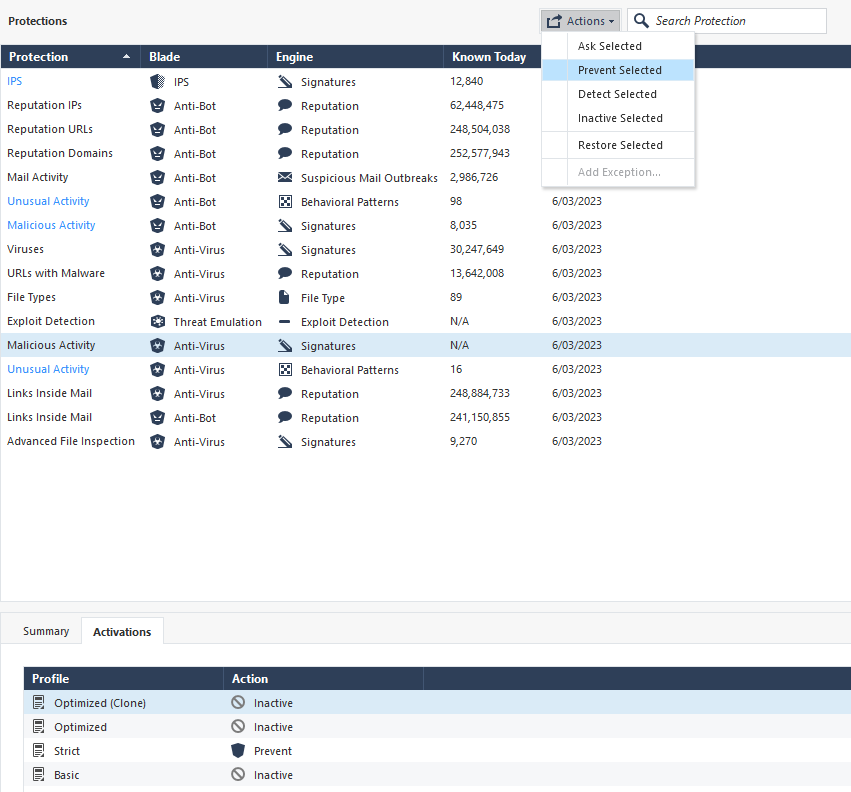
I saw the logs are detected on anti-virus and anti-bot with the detect mode on High Risk Attacks Distinct attacks not prevented due to policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
These logs show you protections triggered by the traffic while being in Detect mode. Change them to Protect if this is what you want.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the detect mode mean Security Gateway allowed the connection into the environment. right ? And if we change from the detect to prevent mode what is will impact ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, Detect means the traffic was allowed.
If you switch to Prevent, the traffic would be blocked.
The impact will depend on whether the traffic is actually malicious or legitimate (i.e. the detection is a false positive).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @PhoneBoy ,
Could you please provide me guide where I can change that policy from Detect to Prevent action? And one more what is the recommendation and user experience (Detect or Prevent action)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
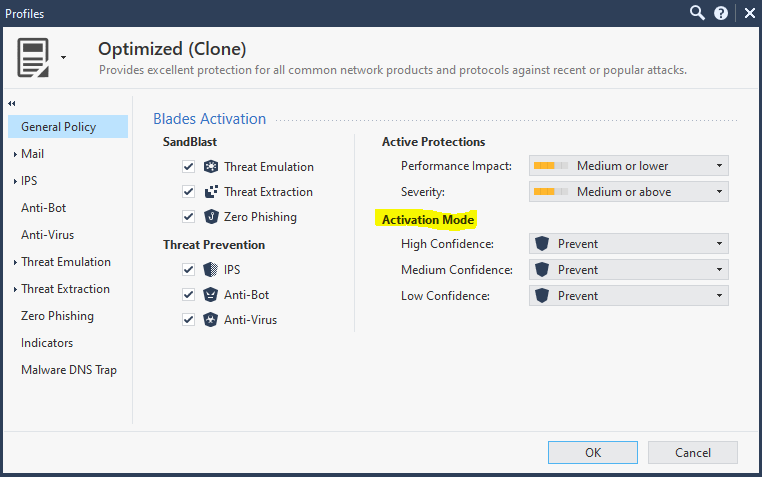
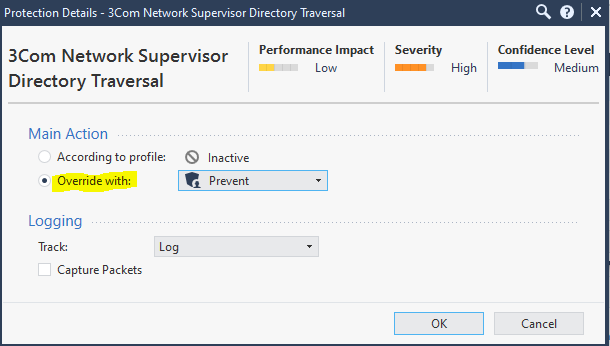
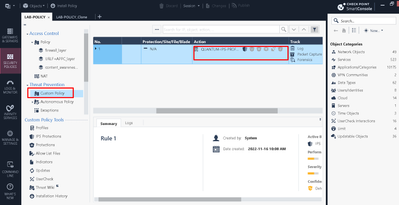
Per the previous thread there are a couple of methods.
Security Policies > Threat Prevention > Custom Policy
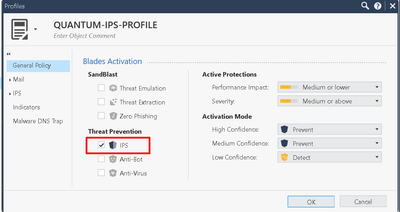
1. Profile - Activation mode:
2. Specific protections (IPS):
Custom Policy tools - IPS protections
Custom Policy tools - Protections (AV/AB)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In addition to the great stuff Chris gave you, be aware that having AV/ABOT enforcement set to "Background" can cause a Detect to occur even if all relevant settings were configured to Prevent. Here is the relevant text from my IPS/AV/ABOT Immersion course explaining why:
Note that if “Background” is set for Anti-Virus and/or Anti-Bot, it can result in situations where the reported action in the log is “Detect”, even though the relevant protection is set to “Prevent” in the applicable TP profile. This can occur when some unknown content is encountered by AV/ABOT, but because “Background” is set, the content is let through the firewall while the unknown data is sent off to the ThreatCloud for evaluation. If the ThreatCloud returns a “malicious” verdict, a log is created with an action of Detect (which is what really happened, but after-the-fact). Subsequent encounters with this content now known to be malicious will of course be dropped with a Prevent action and associated log. Further information: sk74120: Why Anti-Bot and Anti-Virus connections may be allowed even in Prevent mode.
CET (Europe) Timezone Course Scheduled for July 1-2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Some vendors use term "monitor", which is literally fancy term for "detect", nothing else, and as @PhoneBoy said it would be allowed and prevent would block the traffic.
Put it this way...I say same thing to any customer. If you are not sure or clear on what profile to use, just stick with optimized and modify it, so it only uses IPS, if you dont plan to use AV or AB blades.
It would simply save the profile as Optimized (clone) and then you right click on the threat prevention policy and select that profile (you can see example in my lab, I just gave it another name)
Andy