- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Introduction to Lakera:
Securing the AI Frontier!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: Autonomous Threat Prevention; How to disable T...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Autonomous Threat Prevention; How to disable Threat Emulation and Threat Extraction for NGTP Gateway
Greetings,
Does anyone know how to successfully apply and run Autonomous Threat Prevention on Security Gateways with only an NGTP license?
According to sk163593, you don't need a full NGTX/SBNT license to use Autonomous Threat Prevention:
https://support.checkpoint.com/results/sk/sk163593
And that is indeed the case. Autonomous Threat Prevention works just fine with NGTP, but Smart Console constantly complains about the Security Gateway not having a valid Threat Emulation or Threat Extraction license.
This makes sense as we are running the "Perimeter (recommended)" profile in the Autonomous Threat Prevention Policy, which tries to enable and utilise both Threat Emulation and Threat Extraction.
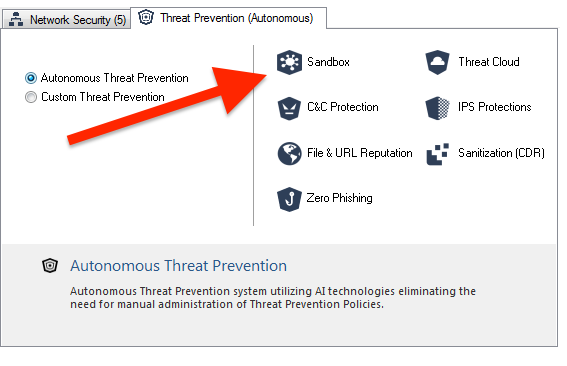
But there seems to be no way for us to disable these blades. You can't choose what blades to run on the Security Gateway object. You choose Autonomous Threat Prevention or Custom Threat Prevention, which lets you manually select blades.
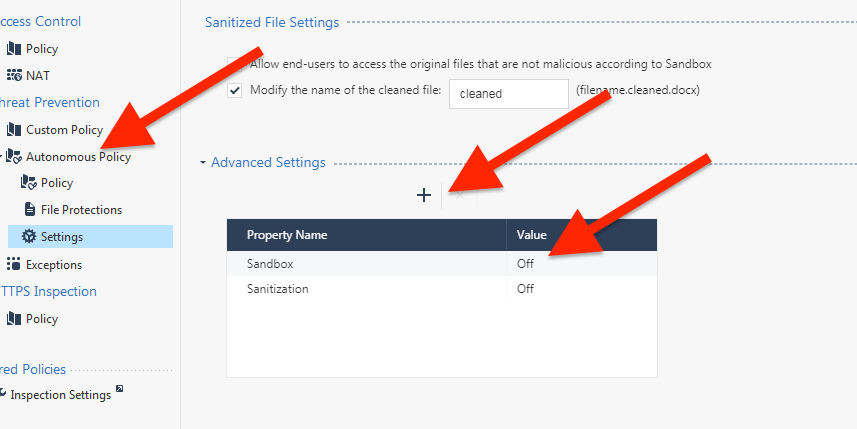
No apparent settings within the Autonomous Threat Prevention Policy let you disable specific blades. The closest thing I've found is to go to Autonomous Policy -> Settings -> Advanced Settings and add Sandbox and Sanitization with "Off" as an override. But this doesn't change anything regarding Smart Console complaining about no valid Threat Emulation or Threat Extraction license on the Security Gateway.
I even tried to create a global exception disabling both blades in the policy. But it's still complaining. I tried to re-create this in my LAB, and it's the same behaviour. I can't locate any meaningful information in the ATRG SK for Autonomous Threat Prevention or anything in the R81.10 or R81.20 Threat Prevention Administration Guides.
How is one expected to deploy and run Autonomous Threat Prevention with only NGTP and no NGTX/SBNT license on the Security Gateway? Do you have to ignore the red warning on the object in Smart Console??
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
Labels
- Labels:
-
Threat Emulation
-
Threat Extraction
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In sk167109: Autonomous Threat Prevention Management integration Release Updates > List of Resolved Issues and New Features per Update we find:
| Update 13 (15 July 2021) | |
| ODU-154 | The License absence warning may be shown to NGTP licensed users. |
Can you verify that you use no older version ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the rapid response. The management and Security Group have direct access to updates.checkpoint.com, so this should update automatically. I did verify it, and it does seem to be the case:
MGMT:
BUNDLE_GOT_TPCONF_MGMT_AUTOUPDATE Take: 36
BUNDLE_DC_INFRA_AUTOUPDATE Take: 30
BUNDLE_GOT_MGMT_AUTOUPDATE Take: 108
GW:
BUNDLE_GOT_TPCONF_AUTOUPDATE Take: 111
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suppose this might be related to the appliances shipped with NGTX/SNBT the first year. When running cplic print the contract coverage is mentioning both Threat Extraction, and Threat Emulation with expiration dates Dec 2022.
# ID Expiration SKU
===+===========+============+====================
1 | T5T5094 | 9Dec2022 | CPSB-TEX-7000-PLUS-1Y
+-----------+------------+--------------------
===+===========+============+====================
5 | T410YT9 | 9Dec2022 | CPSB-TE-7000-PLUS-1Y
+-----------+------------+--------------------
Might it be that Autonomous Threat Prevention starts complaining due to this? If there were no contract for either, to begin with, it wouldn't complain. I suppose I have to contact Account Services to have them remove the expired Threat Emulation and Threat Extraction from the license/contracts?
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am a bit confused here. Do you have a valid contract in the UserCenter?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, @_Val_
There are no valid contracts for Threat Emulation or Threat Extraction. The customer has never intended to go beyond NGTP. But these CPAP-SG7000 appliances included NGTX/SBNT the first year.
We have deployed Autonomous Threat Prevention from the get-go. But ever since the contracts for Threat Emulation and Threat Extraction expired in December 2022, Smart Console has been nagging them about expired licenses for Threat Emulation and Threat Extraction.
What I'm trying to achieve is to keep using Autonomous Threat Prevention but to have this red warning regarding no license for Threat Emulation and Threat Extraction go away. They have no intention of renewing these two blades, so having the warning is rather misleading and annoying.
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, cristal clear now. ATP includes TX/TE as part of the profiles. Technically, you already use just partial functionality of ATP.
Personally, I do not see there too many options. Try checking with TAC what can be done, but I am pretty sure the answer will be "ATP is not supported to run partial config without TX".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_
That would be awkward, considering how the sk163593 - Autonomous Threat Prevention Management states:
Q: Do we need a special license?
A: No. You need the standard NGTP/NGTX licenses.
Ref: https://support.checkpoint.com/results/sk/sk163593
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am looking into the Threat Prevention admin guide, and it clearly states that File protection requires sandboxing. Also, all pre-defined profiles are set with TE/TX active. Finally, the GW side settings clearly have Sandboxing there.
You can use "Custom Threat Prevention" and uncheck TX/TE, but it will not be autonomous anymore. Worth checking with TAC, regardless.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually, I think there is a way.
You can turn off TE and TX in the advanced properties of ATP. Try this and let me know if it helps:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sadly I've already tried this without any luck. I also created a global exception disabling the TE and TX blade. But no dice.
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please open a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So the issue is not resolved in the current take, it seems - worth asking TAC...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@G_W_Albrecht There is nothing to resolve, the license is not there in the first place. SK you mentioned is about false message about a missing license when it is in place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why would sk163593 - Autonomous Threat Prevention Management even mention NGTP if you will be getting warnings nonstop if you don't have NGTX/SBNT?
I think this is specific for this Security Group as a result of expired contracts for TE and TX in place. I'd bet if these contracts didn't show, it would work with NGTP just fine without any warnings. Without TE and TX functionality, of course.
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Answered above. You have a point, there is a way to turn sandboxing and other properties off.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May removing the expired contracts would help ? But i only know sk105757...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, it reads: The License absence warning may be shown to NGTP licensed users.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello everyone,
Is there anything new on this?
I also find the messages very annoying and many customers therefore want to go back to the old scheme and not use Autonoumous.
has anyone found a way to get rid of the messages?
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I’ve forwarded this issue to the relevant owner in R&D.
Let’s see what solution they might suggest.
Thanks,
Tal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Tal_Paz-Fridman ,
thank you.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesWed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter