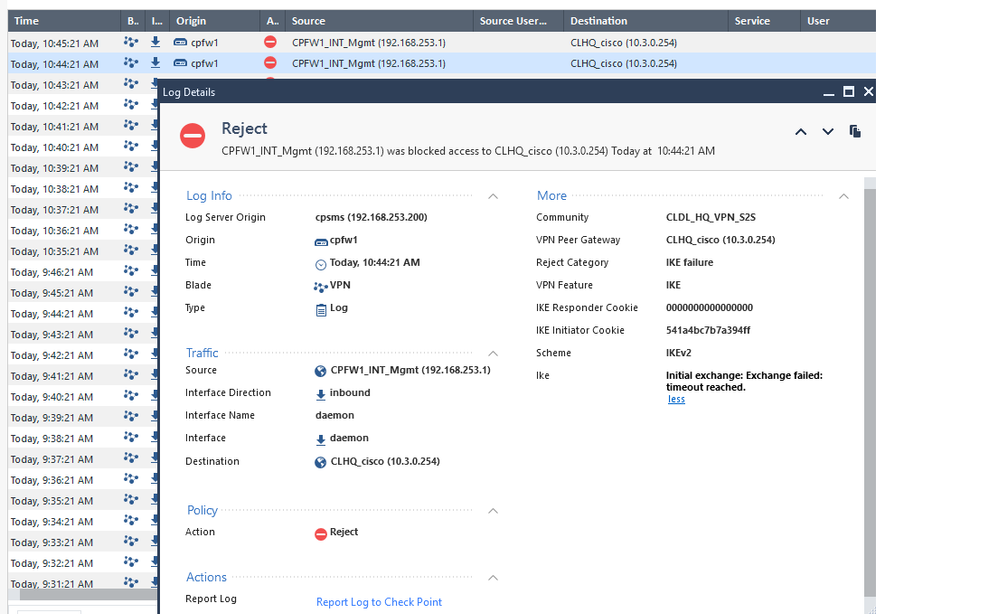
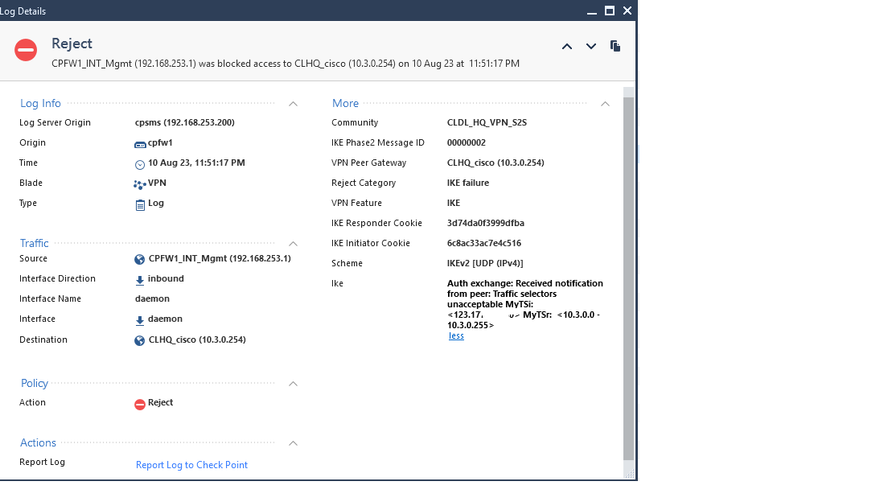
from the checkpoint log, i can get the IKE responder cookie. but today, i tested again. always get this from the log.
Traffic selectors unacceptable MyTSi: <IPv4 Universal Range> MyTSr: <IPv4 Universal Range>
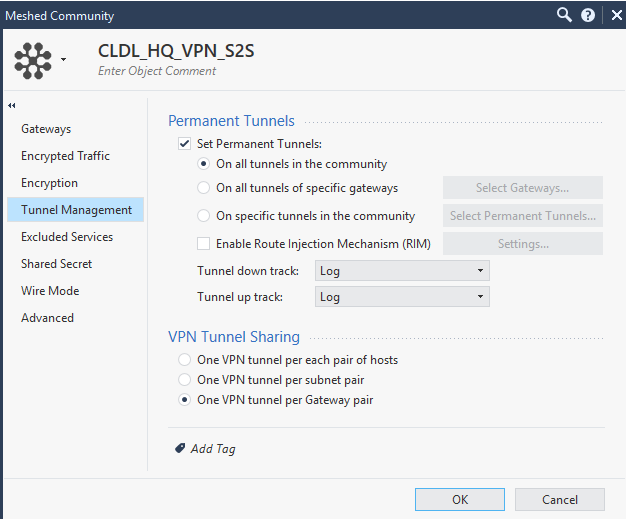
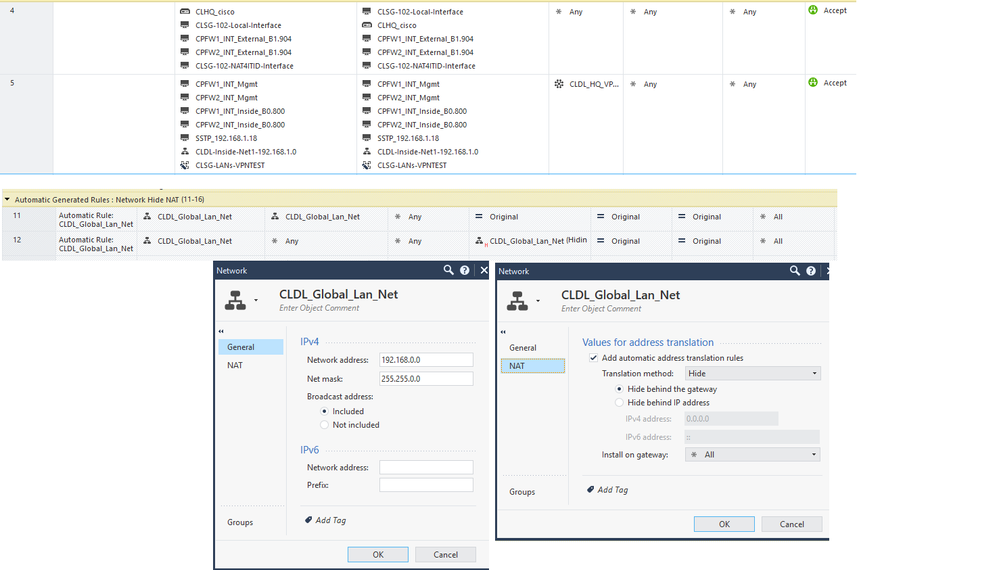
so, i tested "VPN Domain" with/without "disable NAT inside the vpn community", all failure.
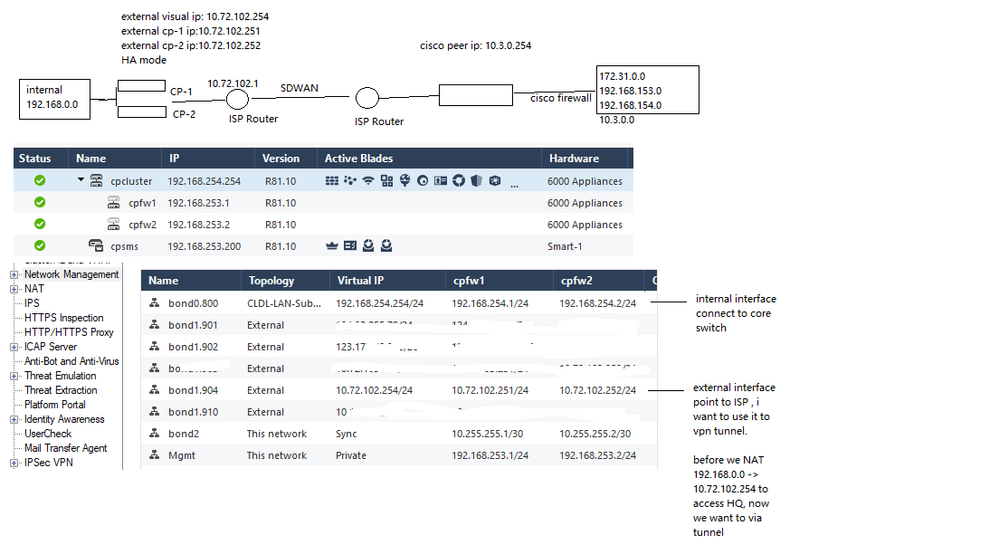
acctually, checkpoint (my side)--- internal subnet 192.168.0.0
cisco ( HQ side ) --- just open 10.3.0.0/24 + 172.31.1.0/24 + 192.168.154.0/23
before create tunnel, my laptop 192.168.1.18 ----NAT---> 10.72.102.254 ( CP external interface to HQ ) ----> HQ network
just for testing.
i set my side VPN Domain :
1) 192.168.1.0/24
2) 192.168.1.0/24 + 10.72.102.0/24
3) 10.72.102.0/24
4) 192.168.0.0/16
i set HQ VPN Domain:
1) 172.31.1.0/24
2) 10.3.0.254/24
3) 172.31.1.0/24 + 10.3.0.254/24
all failure. all logs include "Traffic selectors unacceptable MyTSi: <IPv4 Universal Range> MyTSr: <IPv4 Universal Range>"
------------------
as your mentioned i do the debugging, just "grep -A 40 -B 40 MyTSi" to get about 80 lines log output. do not know whether it is useful.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::doHandleMessage: Got state waiting for arriving message, status initial and event Message Arrived.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::setState: Changing state from: waiting for arriving message to: received message..
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::doHandleMessage: Handling incomming message for exchange 23043, 'Auth for initiator', iSpi: 192780062e6b6406, rSpi: 2d1a75e3b173eea5)
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeEvent::handled: Event Message Arrived Event handled by exchange 23043
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::eventTerminated: entering.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeMsgEvent::~ikeMsgEvent: entering. (exchange 23043)
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] >>>
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] >>> EXCHANGE: 'Auth for initiator' (23043)
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] >>> PROCESS INCOMING MESSAGE
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] >>>
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] cksumMessage: entering
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] cksumMessage: Checksumming 144 bytes with integrity algorithm HMAC-SHA2-256
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Message::Decode: Message passes integrity check
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] decryptMessage: entering
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] decryptMessage: IV:
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] e7 a2 f3 7d f8 64 48 a5 b2 b4 52 11 61 1f c4 f3
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] decryptMessage: Decrypting 96 bytes using SK_er
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikecrypt_decrypt: decrypted. padlen=15, resulting bytes=80
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] decryptMessage: Result has 80 bytes
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Message::decodeAllPayloads: payload 1: VendorID (next=IDr)
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] VendorIDPayload::Decode: Unknown Vendor ID type
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Message::decodeAllPayloads: payload 2: IDr (next=Auth)
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] IDPayload::Decode: ID payload decoded successfully
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Message::decodeAllPayloads: payload 3: Auth (next=Notify)
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Message::decodeAllPayloads: payload 4: Notify (next=None)
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] NotifyPayload::Decode: Notify payload (type 38) has no data
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::updateXML: entering.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::preValidatePayloads: enter. imcomming msg: 0x41b3e6c0
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::processAllNotifications: entering.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::processNotification: Traffic selectors unacceptable
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::doHandleNotification: entering.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::setNotifyData: entering..
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::doProcessNotification: entering. notification type: 38.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeSimpOrder::getPolicyTSi: enter
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeSimpOrder::getPolicyTSr: enter
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeSimpOrder::isSharedSecretAuth: entering (order 18877, ref count 2).
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] dbCommunityHandle::usingPresharedSecret: entering
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::getMethods: entering.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::getMethods: No outbound sa.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::setLog: Setting log message:
Received notification from peer: Traffic selectors unacceptable MyTSi: <IPv4 Universal Range> MyTSr: <IPv4 Universal Range>..
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51] GetEntryIsakmpObjectsHash: received ipaddr: 10.3.0.254 as key, found fwobj: CLHQ_cisco
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51] fwipsechost_from_ipxaddr: calling GetEntryXIsakmpObjectsHash for 10.3.0.254 returned obj: 0x41b286c4
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51] GetEntryCommunityHashX: received ipaddr: 254.0.3.10 as key, found community: CLDL_HQ_VPN_S2S
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51] FindCommonCommunity: Found common community (IPv4 addr=254.0.3.10) (CLDL_HQ_VPN_S2S) for CLHQ_cisco
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51] CFwdCommStreamLocal::Write called
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51] CFwdCommStreamLocal::Write sent 356 bytes
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::processAllNotifications: While process Traffic selectors unacceptable notification changing status to semi-doomed
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::expectedPayloadTypesExist: entering.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::expectedPayloadTypesExist: Received 1 Notification payloads in message.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::expectedPayloadTypesExist: Unexpected SA payloads count in message, 0.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::preValidatePayloads: returning status -3
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::processMessage: verifying payloads. curr status: -3
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::validatePayloads: enter.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::processPayloads: processing the payloads.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::isPayloadExpected: entering. payload: Vendor ID. type 43
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::validateGeneralPayload: validating payload VendorID..
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::isPayloadExpected: entering. payload: ID-r. type 36
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::validateGeneralPayload: validating payload ID-r..
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::isPayloadExpected: entering. payload: Auth. type 39
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::validateGeneralPayload: validating payload AUTH..
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeSimpOrder::isSharedSecretAuth: entering (order 18877, ref count 2).
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] dbCommunityHandle::usingPresharedSecret: entering
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::validateAuthPayload: validate via shared secret.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeSimpOrder::getPresharedSecret: entering (order 18877, ref count 2).
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeSimpOrder::getPresharedSecret: entering (order 18877, ref count 2).
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] AUTHPayload::Verify: signature verifies OK
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::validateAuthPayload: res=0
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::processPayloads: processPayloads returning initial status
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::continueHandleMessage: entering with status = 0
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::postMessageProcessed: enter with status 'initial'
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] initiatorExchange::postMessageProcessed: entering..
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::doComplete: entering..
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::updateSA: Updating esp sa.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] updateEspSA: Invalid chosen proposal ((nil)) or order (0x41bbce28).
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeEvent::handled: Event Diffie-Hellman Event could not be handled by exchange 23043
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::eventTerminated: entering.
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeDHEvent::~ikeDHEvent: entering. (exchange 23043)
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] Exchange::setStatus: Changing status from: initial to: failure (final)..
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::doComplete: entering with status: failure (final) and sa: 0x41b13b48
[vpnd 26945 4071794688]@cpfw1[22 Aug 19:20:51][ikev2] ikeAuthExchange_i::doComplete: notify registered objects - negotiation failed
-----------------
vpn tu 1 & 2
(Q) Quit
*******************************************
1
Peer 10.3.0.254 , CLHQ_cisco SAs:
IKEv2 SA <1597e2aea42be15d,de37e12799b93879>
Hit <Enter> key to continue ...
********** Select Option **********
(1) List all IKE SAs
(2) * List all IPsec SAs
(3) List all IKE SAs for a given peer (GW) or user (Client)
(4) * List all IPsec SAs for a given peer (GW) or user (Client)
(5) Delete all IPsec SAs for a given peer (GW)
(6) Delete all IPsec SAs for a given User (Client)
(7) Delete all IPsec+IKE SAs for a given peer (GW)
(8) Delete all IPsec+IKE SAs for a given User (Client)
(9) Delete all IPsec SAs for ALL peers and users
(0) Delete all IPsec+IKE SAs for ALL peers and users
* To list data for a specific CoreXL instance, append "-i <instance number>" to your selection.
(Q) Quit
*******************************************
2
SAs of all instances:
Peer 10.3.0.254 , CLHQ_cisco SAs:
IKEv2 SA <1597e2aea42be15d,de37e12799b93879>
(No IPSec SAs)
Hit <Enter> key to continue ...