- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- "fw ctl zdebug" Helpful Command Combinations
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"fw ctl zdebug" Helpful Command Combinations
"fw ctl zdebug" is a powertool that is not exhausted from being used with "fw ctl zdebug drop". There is not much to be found in Check Point KB or in the documentation. "fw ctl zdebug" is an R&D tool for testing software in development. Therefore, the insert should be used with care. It starts a debugging in the background until it is aborted with CTRL+C. On productive systems it can have a high performance impact. Furthermore, the debug buffer is not the largest.
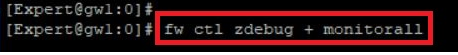
What happens when you execute! It is a macro that executes the following commands:
fw ctl debug -buf 1024
fw ctl debug [The option behind "fw ctl zdebug"]
fw ctl kdebug -f
[Wait until CTRL+C is pressed]
fw ctl debug 0
Node:
A current list with kernel debug flags can be found here.
Here are some good examples for debugging:
fw ctl zdebug + packet
fw ctl zdebug + packet | grep -B 1 TCP |grep -B 1 "(SYN)" <<< change SYN-ACK,ACK,FIN,... and/or UDP,TCP...
fw ctl zdebug + all |grep -A 1 "Monitor" | grep "1.1.1.1" <<< change IP address
fw ctl zdebug + all |grep -A 2 "Monitor"
fw ctl zdebug + sync
fw ctl zdebug + conn |grep "After VM:" |grep "(SYN)"
fw ctl zdebug + xlate
fw ctl zdebug + monitorall <<< use with host IP "| grep 1.1.1.1" or network range "| grep 1.1."
fw ctl zdebug + monitor <<< use with host IP "| grep 1.1.1.1" or network range "| grep 1.1."
fw ctl zdebug + filter conn | grep -A 8 "rule 1" <<< change rule number - show connetions to rule xyz
fw ctl zdebug + filter monitor | grep -A 8 "rule 2" <<< change rule number - show connetions to rule xyz
Attention, if you turn on debugging, this will affect the performance of the firewall.
Regards,
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko,
That's super interesting!
Are there any other "fw ctl zdebug" commands?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello mates,
That's very useful post, but I don't understand what the reason is why there's no official documentation in SK
Thanks Heiko for your post
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw ctl zdebug options are documented in the topic-specific ATRGs in SecureKnowledge.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Principle all debug modules are possible for debugging with „fw ctl zdebug“.
„fw ctl debug -h“ shows all current kernel debugging options for modules and instances.
You can use various combinations.
Unfortunately, the commands are only mentioned in few SK's. Try it out here. I have described the most important ones above.
I would be pleased about new interesting combinations.
Regards,
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's a great tool. I didn't know you could do so much with it. I have only worked with "fw ctl zdebug drop" and did not recognize the potentiality.
Thanks for the info.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw ctl zdebug drop = debug of IPv4 connections
fw6 ctl zdebug drop = debug of IPv6 connections.
all flags and options listed here should be also valid for IPv6 (fw6).
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice post. Thanks Heiko.
In the original post there is this line:
fw ctl debug [The option behind "fw ctl zdebug"]
Is that not more like a fw ctl debug -m fw [options/flags] ?
I think I remember the zdebug focuses on the fw kernel module but I think I also remember that some other kernel module debug flags may also be set.
I know that the (DON'T DO THIS IN PRODUCTION) option of 'fw ctl zdebug all' adds debug flags to three or four other kernel modules but not all.
The fw module gets all debug flags set in that case.
fw ctl zdebug -m CPAS all would be required if, for example, the CPAS module was interesting for a full debug. The command above would not then be of use.
What is the monitorall option doing?
Regards,
Don
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think it's just turning up the debug level a bit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is very useful! Thanks for sharing... .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very nice Heiko.
I think that the most useful part of using the command is that when you stop the debug you are running it really stops all debugging, so you cannot forget to turn it off again.
I think that the most useful part of using the command is that when you stop the debug you are running it really stops all debugging, so you cannot forget to turn it off again.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw ctl zdebug + monitorall -> shows many fw chain modules
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
so helpful,thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am currently running R80.30 with JHFA take 237. I used to be able to run fw ctl zdebug + drop | grep 10.x.x.x , but that hasn't worked in a while. When I try to grep for a ip address it is as if the debug never loads and hangs there. This is true on all of my gateways. Has something changed in regards to this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use "-F" option instead of "grep".
fw ctl zdebug -F '10.x.x.x,0,0,0,0' -F '0,0,10.x.x.x,0,0' + drop
"fw ctl zdebug" Helpful Command Combinations
"fw ctl zdebug" is a powertool that is not exhausted from being used with "fw ctl zdebug drop". There is not much to be found in Check Point KB or in the documentation. "fw ctl zdebug" is an R&D tool for testing software in development. Therefore, the insert should be used with care. It starts a debugging in the background until it is aborted with CTRL+C. On productive systems it can have a high performance impact. Furthermore, the debug buffer is not the largest.

What happens when you execute! It is a macro that executes the following commands:
fw ctl debug -buf 1024
fw ctl debug [The option behind "fw ctl zdebug"]
fw ctl kdebug -f
[Wait until CTRL+C is pressed]
fw ctl debug 0
Node:
A current list with kernel debug flags can be found here.
Here are some good examples for debugging:
fw ctl zdebug + packet
fw ctl zdebug + packet | grep -B 1 TCP |grep -B 1 "(SYN)" <<< change SYN-ACK,ACK,FIN,... and/or UDP,TCP...
fw ctl zdebug + all |grep -A 1 "Monitor" | grep "1.1.1.1" <<< change IP address
fw ctl zdebug + all |grep -A 2 "Monitor"
fw ctl zdebug + sync
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 15 | |
| 8 | |
| 5 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


