- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: install a Certificate for IPSec VPN
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
install a Certificate for IPSec VPN
Hi All,
is it possible to install a public certificate for IPSec VPN without creating TrustCA or CSR?
Supposed that I already have a public certificate vpn.domain.com, I just want install it...
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah. Unfortunately, you can't use a wildcard certificate in this fashion.
Here's the SK article on creating the 3rd party CA and any intermediate CAs, then generating the CSR with that CA:
https://support.checkpoint.com/results/sk/sk149253
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, use Add to import it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
finally, you have to generate CSR if you import it...
i now have a certificate, i just want o replace the default certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I'm worndering the same as @Alex_Wu, in my case I'm replacing old Cluster to new gateway models, so, I need to import the IPSec VPN Certificate which resides in the SMS, but there is no such option to Import the certificate to the new Cluster. If you click "Add" it takes you to generate the CSR, but I already have the signed certificate, you need to import it.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I'm worndering the same as @Alex_Wu, in my case I'm replacing old Cluster to new gateway models, so, I need to import the IPSec VPN Certificate which resides in the SMS, but there is no such option to Import the certificate to the new Cluster. If you click "Add" it takes you to generate the CSR, but I already have the signed certificate, I just need to import it, ¿is there a way do do this?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are about to replace the cluster members in an existing cluster, you will only remove the old device from the cluster and initiate SIC with the new member, the policy for the cluster stays the same and the same certificate will be installed on the new device. If you create a new cluster with the new devices you must have the certificate to import it to the new cluster.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a new CLuster because new models (6600) vs old models (4800) are different in hardware and software, also
Indeed I have the certificate which I can export form the SMS, but there is no such option to Import the certificate to the new Cluster. If you click "Add" it takes you to generate the CSR, but I already have the signed certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If both the old and new gateways are managed by the same management, there is no need to do this as new certificates will be generated and automatically trusted.
Any third party will validate the certificate is valid through the certificate authority.
So I’m not sure why this is necessary.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello and thank you for your support.
Yes, both are managed by the same management, but the certificate is from an external CA (Digicert). Let me show you some images for better explanation:
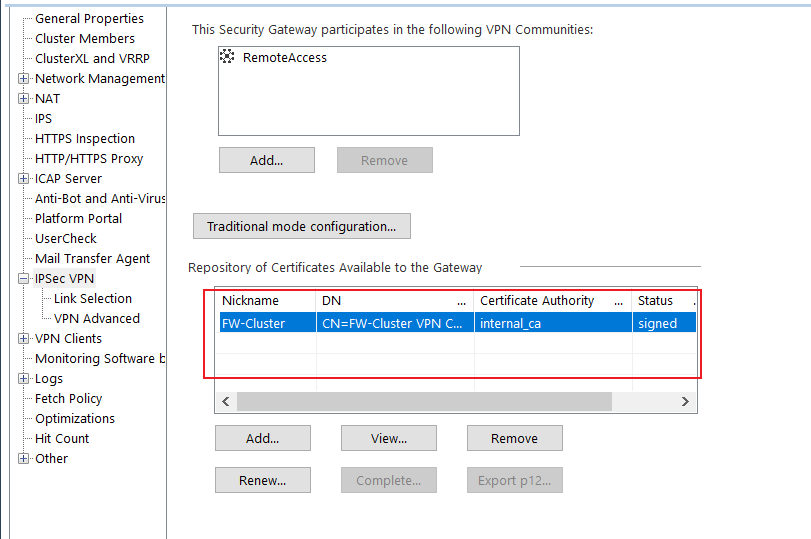
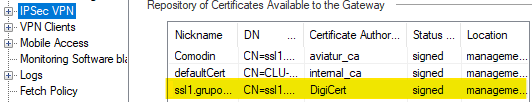
This is the current CLuster which I need to replace, it has the certificate signed by Digicert CA.
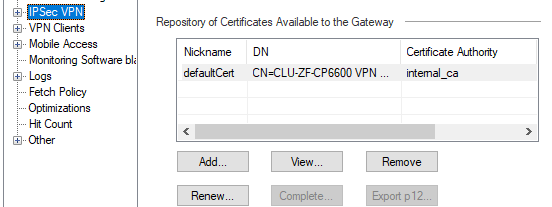
Now, this is the new Cluster which I'm preparing for migration, so, I need to ensure it has the same certificate as current Cluster. I know I can export the certificate from the SMS with export_p12 command, but there is not option to import such certificate in the Cluster properties:
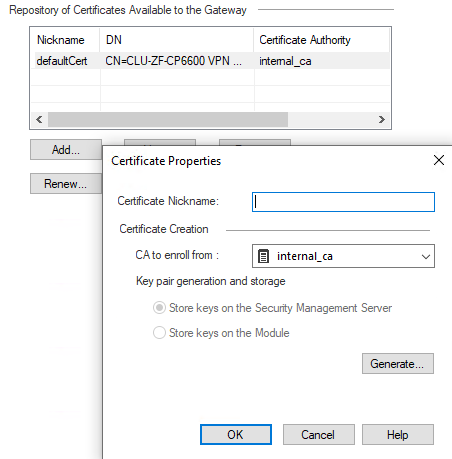
If I click "Add" this takes me to generate the CSR, but this process was made in the past whe creating the certificate for the current cluster.
So, my question is whether there is a method to import the certificate directly, or need to make the signing process again.
Thank you in advance for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the screenshots, this helps a lot.
In this case, you must generate a new certificate via a Certificate Signing Request as we do not support importing private keys for VPN usage.
I suspect we don't allow this to maintain the security of the private key.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello guys,
I understand this is quite an old topic. However, since 2022 I’ve been wondering if there’s any way to import an already existing SSL certificate for an IPsec VPN on R81.20 - just like it’s possible to do for the Platform Administration Web Portal, UserCheck and Mobile Access portal ?
Is there any supported method or workaround to achieve this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, just follow the same information as listed above. You will have needed to generate the CSR from SmartConsole here, tho, as PhoneBoy noted above. Certificates for the other portals are a separate matter, because they use a different internal infrastructure on the gateways (multiportal), whereas IPsec VPN certificates are the VPN and IKE daemons.
As far as importing arbitrary pre-made certificates, then no, you cannot do that. The certificate information (CN, etc.) needs to match the gateway's own information in order to be used correctly. This what the CSR generation process does for you. Plus, this ensures the private key is stored securely on the management server (and pushed to the gateways).
When you have the completed certificate, you can finish the enrollment with the "Complete" button, which will become available for that certificate.
When the certificate is imported, you can select the certificate within the IPsec VPN configuration for the specific remote VPN gateway peer. Edit the interoperable device peer, select IPsec VPN on the left, and you can choose the match criteria for it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Duane_Toler,
thank you for your prompt response.
I understand that no changes have been made by Check Point regarding this.
Unfortunately, the current/supported procedure doesn’t apply to my scenario: I’m using a wildcard SSL certificate issued by a public CA. It would have been ideal to use it not only for other portals, but also for client VPNs.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah. Unfortunately, you can't use a wildcard certificate in this fashion.
Here's the SK article on creating the 3rd party CA and any intermediate CAs, then generating the CSR with that CA:
https://support.checkpoint.com/results/sk/sk149253
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 12 | |
| 8 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter