- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: VSX: Moving VLAN to another VS within the same...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VSX: Moving VLAN to another VS within the same VSX-Cluster
Hi community,
in my daily business I am faced with a problem for years now and would like to hear if you guys have a better solution to overcome my problem.
I am running serveral VSX environments with a bunch of virtual systems.
Regularly I have the need to move a VLAN from one virtual system to another virtual system within the same VSX-Cluster.
The VLAN is not connected to a virtual switch as it would too expensive to connect all VLANs to a seperate virtual switch.
All VLANs are behind the same bond interface except the external interface.
Example setup:
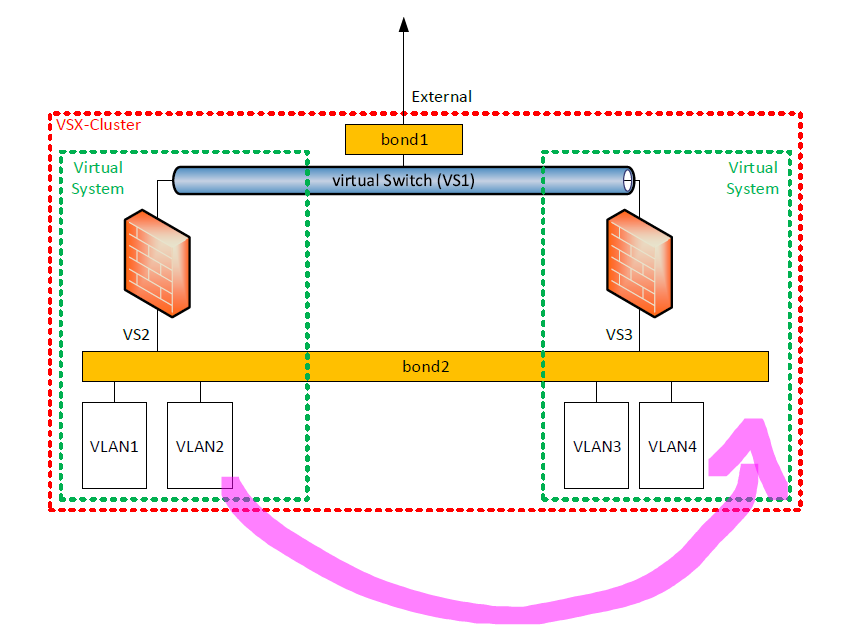
When moving a VLAN from one virtual system to another within the same VSX-Cluster I am facing the following problems:
You are not allowed to add the same VLAN to multiple virtual systems using the same bond interface.
I consequence I know two possibilities to overcome this problem, but both don't make me happy:
1. Deleting the VLAN on VS2, installing policy on VS2, adding VLAN on VS3, installing policy on VS3.
As VS2 and VS3 are running in the same SmartCenter/Domain this means downtime of minimum 10 minutes.
2. Adding a new physical link to the same Switch, configuring the new VLAN to VS3 with duplicate IP address using the new physical link and moving the VLAN on switch side from the old physical link to the new one.
In this scenario the downtime is acceptable, but you always need two links the the same switch and you a loosing flexibility as you need support of the switch guys.
Moreover in some environements I do not have free interfaces on firewall side so I don't have the possibility to add a second link to the same switch.
Any ideas how to overcome this problem?
The coolest thing would be a nice and smooth solution provided by Check Point.
I started asking Check Point years ago, but didn't get a solution, yet.
Looking forward to read your ideas.
Cheers
Sven
Labels
- Labels:
-
VSX
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Sven_Glock I think you have answered your own question here. Option one is the way to go. It causes downtime on the particular VLAN, which is, however, expected event for moving a physical interface from one GW to another.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Having a short downtime is an accaptable thing, but 10 mins+ is out of accaptable range.
As accelerated policy installation is still far away for my environment do you have any ideas how to accelerate option one?
I am struggeling with the policy installation on vs3.
Policy installation is necassary when adding a new interface with a new ip network, because of spoofing objects, etc.
But how about this scenario:
- I add the new network with a dummy VLAN to VS3. --> Apply --> Install policy.
- Now spoofing, routing etc. is fine.
- Next I delete VLAN on VS2 --> Apply --> Install policy
- Then just changing the dummy VLAN to the final VLAN ID and Apply. Will the new network be up and running without policy installation?
Its just guessing, but is there a need to install policy when just changing a VLAN?
If not this would reduce downtime by 30%. It's still a lot but less worse.
More ideas welcome 8)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is the VLAN you are moving the highest or lowest VLAN ID on the interface for the VS which is currently handling it?
Will it be the highest or lowest VLAN ID on the interface on the new VS you're moving it to?
If the answer to both questions is no, you may be able to get away with removing it from the old VS, provisioning (but not pushing policy), adding it to the new VS, provisioning, pushing policy to the new VS, then pushing policy to the old VS. The outage would last from when you provision the old VS to when you finish pushing policy to the new VS.
If the answer to either question is yes, this may not be safe. By default, ClusterXL monitors the highest and lowest VLAN IDs on each interface. If it's the highest or lowest on the old VS, provisioning the removal there could cause spontaneous failover. If it's the highest or lowest on the new VS, you should be fine, but may see failovers when policy is first installed. Depending on how you do sync, the failovers could trigger active contention which could result in neither firewall taking over the cluster (direct-wired sync is particularly bad for this).
I would test this a lot. Like a LOT a lot. ClusterXL should only care about VIP uniqueness within a VS, but I may be misremembering.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am always monitoring all vlans - even it it costs some ressources - never trust a switch guy 😊
I will test it in my lab after some vacation and will keep you updated about the outcome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay, then your only option is to provision the removal, push the removal, provision the new interface, push the new interface. There’s not a faster way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We experienced instability/flapping when only removing and provisioning on the source vs, so be careful with that approach.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your advice! 👍
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not facing this problem, but I think that you can create dedicated TMP VLAN for migration and always ask switching guys to map migrated vlan to this TMP vlan.
After that migration should be faster:
- Create TMP vlan (with all configuration) on target VS
- Removing migrated vlan from previous VS
- Change TMP vlan to migrated on target VS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"You are not allowed to add the same VLAN to multiple virtual systems using the same bond interface."
Hi, i know about this limitation, but it seems that is not mentioned on VSX Admin Guide. Am i correct?
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you want to have the same VLAN on the same BOND to multiple VS. you will use a virtual switch within VSX. And connect both the VS to the virtual switch.
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much Magnus; last question, the only alternative is to create the same vlan to different physical interface/bond, it is right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Virtual switch or virtual router or diff physical interfaces / bond.
Virtual switch would be the most common way to solve it, if it’s to the same L2 environment and actually the same VLAN.
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do not understand why you need an alternative to a virtual switch. This is a widely used and stable solution for your requirement.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 26 | |
| 20 | |
| 16 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


