- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Register HereCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: VPN Site-2-Site on alias interface
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VPN Site-2-Site on alias interface
Hello
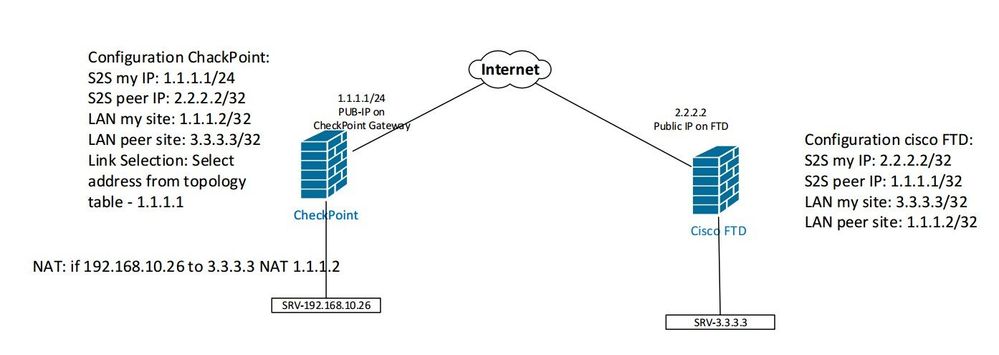
Please help me solve the problem. The situation is as follows. We need to install a VPN between two locations, on our side a checkpoint and on the other side cisco Firepower (FTD), external / public addresses (example)
PUB 1.1.1.1 255.255.255.0 (eth1) from our side
PUB 2.2.2.2 255.255.255.255 from cisco Firepower side
We have an internal server for which we need to provide communication 192.168.10.26 / 24, but as an internal LAN network for VPN we cannot select it, we need to select the address PUB-1.1.1.2 / 32 as the internal network
From the side of cisco Firepower, the LAN network is also from the category of public addresses, conventionally 3.3.3.3/32
Thus, my settings are as follows:
1.I set an alias on eth1 interface, it turns out eth1: 1 - 1.1.1.2 / 24
2. I configure NAT - if 192.168.10.26 goes to 3.3.3.3 then NAT to 1.1.1.2
3. I create a VPN community, in which I set the encryption, PSK key, set the parameter allowing NAT, for our GW 1.1.1.1 I set up the VPN domain in which there are 192.168.10.26 and 1.1.1.2, I set up the VPN domain for the other side which is 3.3.3.3. Install Tunnel Management in Community in One Tunnel Per Gateway Pair
4 making rules
1.1.1.1 to 2.2.2.2 - Allow
2.2.2.2 to 1.1.1.1 - Allow
192.168.10.26 to 3.3.3.3 - allow
3.3.3.3 to 192.168.10.26 - allow
1.1.1.2 to 3.3.3.3 - allow + community VPN
3.3.3.3 to 1.1.1.2 - allow + community VPN
5. Configuring the "user.def" file
subnet_for_range_and_peer = {
<2.2.2.2, 1.1.1.2, 1.1.1.2; 255.255.255.255>
};
I check if the tunnel is established and the first and second phases, from the 3.3.3.3 server to the 192.168.10.26 server, traffic is going, I see it through Wireshark to 192.168.10.26
But traffic does not go from 192.168.10.26 to 3.3.3.3. In the logs, I see that the traffic reached the GW checkpoint, passed NAT, fell under the rule "From 192.168.10.26 to 3.3.3.3 - allow" and then went to the VPN tunnel.
Return message: Reject:
Child SA exchange: Received notification from peer: No proposal chosen MyMethods Phase2: AES-256 + HMAC-SHA2-256, No IPComp, No ESN, Group 14
We checked the encryption settings, they all match, and if the encryption did not match, would the packets come to my server from a remote server.
Could you please tell me where I could have gone wrong.?
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I’m not clear why you’re creating an interface alias here.
If you’re trying to resolve an IP address conflict between the two sites, you will need to use NAT to resolve it.
If you want to originate your VPN from a specific IP, use the Link Selection setting.
See also: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, I created an alias so that the tunnel was built on this LAN network (which has a public address 1.1.1.2), I need to do something so that traffic from my internal server (192.168.10.26) is transformed into the address 1.1.1.2 and falls under the rule "From 1.1 .1.2 to 3.3.3.3 - allow + community VPN ”, but it does not fall under this rule. I can't figure out why.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And I also noticed such a moment that as soon as I add the VPN to the community, the ping between 1.1.1.1 and 2.2.2.2 stops working. If there is no community then the ping works.
Message:
Auth exchange: Received notification from peer: Traffic selectors unacceptable MyTSi: <IPv4 Universal Range> MyTSr: <IPv4 Universal Range>
Maybe this is where the reason begins that does not work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
phoneboy gave you what I believe is 100% logical answer...Im not sure either why you would use alias interface for something like this. Just use NAT and make sure link selection is configure to reflect this.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like I said, you don't use an Alias interface for this.
You create the relevant NAT rules and/or use Link Selection>
Unless the "alias" is really a VTI, which your error message suggests.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, the fact is that I deleted the alias, but no changes happened, everything is exactly the same, I don't need a link selection , because I am building a tunnel on the address of my gateway, I checked all the settings again, but anyway when I start a ping from my server 192.168.10.26 to server 3.3.3.3 i get failure
Time: 2021-08-24T05: 14: 33Z
Interface Direction: inbound
Interface Name: daemon
Source: 1.1.1.1
Destination: 2.2.2.2
VPN Peer Gateway: 2.2.2.2
Scheme: IKEv2 [UDP (IPv4)]
Ike: Child SA exchange: Received notification from peer: No proposal chosen MyMethods Phase2: AES-256 + HMAC-SHA2-256, No IPComp, No ESN, Group 14
IKE Initiator Cookie: 15d14335ba002a1f
IKE Responder Cookie: e5ff887cd29f5794
IKE Phase2 Message ID: 00000003
Community: S2S-NIT-VPN
Reject Category: IKE failure
VPN Feature: IKE
Action: Reject
Type: Log
Blade: VPN
Origin: GW-A
Interface: daemon
When I check from my public address 1.1.1.1 to the other party's public address 2.2.2.2 I get a message
Time: 2021-08-24T05: 08: 01Z
Interface Direction: inbound
Interface Name: daemon
Source: 1.1.1.1
Destination: 2.2.2.2
VPN Peer Gateway: 2.2.2.2
Scheme: IKEv2 [UDP (IPv4)]
Ike: Child SA exchange: Received notification from peer: Traffic selectors unacceptable MyTSi: <IPv4 Universal Range> MyTSr: <IPv4 Universal Range>
IKE Initiator Cookie: 9168f24c72253a26
IKE Responder Cookie: e3c37a3a7679795a
IKE Phase2 Message ID: 0000001c
Community: S2S-NIT-VPN
Reject Category: IKE failure
VPN Feature: IKE
Action: Key Install
Type: Log
Blade: VPN
Origin: GW-A
Interface: daemon
But the ping still doesn't work ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you want the VPN to originate from a specific IP address, you must set Link Selection correctly, regardless of whether the IP exists on your gateway or not.
What is the precise setting?
Also, please go through the debugging steps in the SK I linked previously as "no proposal chosen" suggests a misconfiguration on one or both sides.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is my scheme, unfortunately I cannot see the troubleshooting, because I do not have access to the CLI, Can you please tell me if I have to configure the "user.def" file? now I have it empty
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To adequately troubleshoot this, you will need access to the CLI.
Otherwise, you are merely guessing where the issue is.
It's possible you may need to adjust user.def, but again, without knowing exactly what the issue is, one cannot say.
I would also strongly suggest engaging the TAC here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would 100% take advice phoneboy is giving you. And as far as user.def file, personally, I dont like modifying files like that on mgmt server, as it can cause bunch of issues, but obviously, back it up first and then make modifications, so if something was to happen, you can always revert the changes with cp command.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good afternoon, I'm slowly starting to figure it out ... I figured out the reason why I don't have a ping between 1,1,1,1 and 2,2,2,2.
The reason is that the checkpoint sends already encrypted traffic to 2,2,2,2, that is, even traffic that does not come from the LAN network, but only from a public address to a public checkpoint, encrypts it anyway, and in cisco, when pinging from a public address to a public one traffic does not go into the tunnel.
Now there is a problem, how can I make sure that traffic from the public address checkpoint 1,1,1,1 to 2,2,2,2 is not encrypted?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Whether you configure it or not, the gateway IP addresses are always in the encryption domain.
This requires editing .def files to resolve.
See scenario 3 here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, I tried this article, but my checkpoint does not want to apply these changes, I think that there are solutions for other checkpoint models. My version is R80.30, I tried all the options presented in scenario 3 but the checkpoint does not want to accept these changes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you say "does not want to apply these changes" what precisely happens?
Also, what precise version is used to manage these gateways, as that will likely impact where you need to make the necessary changes?
I highly recommend engaging with the TAC to assist you with this issue.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 15 | |
| 9 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter