- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: User Directory vs. Identity Awareness
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
User Directory vs. Identity Awareness
Hi, community!
One of our customers is asking for clarification regarding these two blades and honestly we’re kinda having a hard time giving it to them, since the information in course material and admins guides isn't clear enough for them.
I know - and please correct me if I'm wrong or not entirely right - UD is a management blade that will allow us to communicate with an LDAP server and manage users on that server directly from our Check Point infrastructure, as well as define authentication schemes for them; whereas IA will use the identities retrieved from, let's say, an AD, and maps them to their IPs and machine names so we can use that information in rules through access roles.
We've tried that "management vs enforcement" point of view, but they get confused because according to them, some parts of the material state you can have IA without UD, but then the guide says IA uses UD. So, and I quote them, "which one is it?" ![]()
Thanks in advance for your comments!
EDIT: they're running R80/R80.10.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I get this question all the time in CCSA classes. The TL;DR version of the answer is that as long as you have a firewall running at least R75 and a (free) CPSB-IA license, there is no need to enable UserDirectory or obtain a license for it UNLESS:
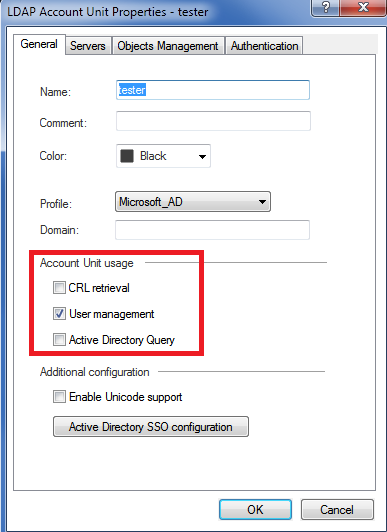
1) You want the ability to manage LDAP users in a read/write situation; in the real world this generally happens over the still-quivering dead body of your LDAP server administrator (i.e. practically never!). This will allow Remote Access VPN users to potentially change an expired password via the Check Point Remote Access VPN software as Marco Valenti observed, and also allow changes to LDAP user passwords/groups directly via the Check Point SmartDashboard (which also requires an extension of the LDAP user schema). This feature's checkbox is called "User Management" on the LDAP Account Unit object. (see screenshot below)
2) You want the ability to retrieve CRLs via LDAP instead of the more-typical HTTP or OCSP (not common). This feature's checkbox is labelled "CRL retrieval" on the LDAP Account Unit object.
3) You need to do an integration to an LDAP server that is not based on Microsoft Active Directory (i.e. Novell eDirectory, Netscape, Lotus Domino, etc). I've never done an LDAP integration to a server that was not AD in over twenty years of Check Point experience, so that should give you an idea of how common it is.
The "Use UserDirectory for Security Gateways (license required)" checkbox on the Global Properties screen for UserDirectory/SmartDirectory does NOT need to be set for IA to operate, which runs counter to some of Check Point's documentation and the CCSA R80.10 courseware. When IA's AD Query feature is first set up the wizard automatically creates the needed Account Unit object through the underpinnings of UserDirectory which is where a lot of the confusion comes in.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Identity awareness just get identity from a source of authentication that can be used for things like access role and rule based on identity and can't be used for things like changing ad user password from blade like mobile access or endpoint client that require user directory license.
At least this is what I understand ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I get this question all the time in CCSA classes. The TL;DR version of the answer is that as long as you have a firewall running at least R75 and a (free) CPSB-IA license, there is no need to enable UserDirectory or obtain a license for it UNLESS:
1) You want the ability to manage LDAP users in a read/write situation; in the real world this generally happens over the still-quivering dead body of your LDAP server administrator (i.e. practically never!). This will allow Remote Access VPN users to potentially change an expired password via the Check Point Remote Access VPN software as Marco Valenti observed, and also allow changes to LDAP user passwords/groups directly via the Check Point SmartDashboard (which also requires an extension of the LDAP user schema). This feature's checkbox is called "User Management" on the LDAP Account Unit object. (see screenshot below)
2) You want the ability to retrieve CRLs via LDAP instead of the more-typical HTTP or OCSP (not common). This feature's checkbox is labelled "CRL retrieval" on the LDAP Account Unit object.
3) You need to do an integration to an LDAP server that is not based on Microsoft Active Directory (i.e. Novell eDirectory, Netscape, Lotus Domino, etc). I've never done an LDAP integration to a server that was not AD in over twenty years of Check Point experience, so that should give you an idea of how common it is.
The "Use UserDirectory for Security Gateways (license required)" checkbox on the Global Properties screen for UserDirectory/SmartDirectory does NOT need to be set for IA to operate, which runs counter to some of Check Point's documentation and the CCSA R80.10 courseware. When IA's AD Query feature is first set up the wizard automatically creates the needed Account Unit object through the underpinnings of UserDirectory which is where a lot of the confusion comes in.

--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there,
Apparently you also need to have a license and active User Directory if you want to use AD groups and users in the Include/Exclude settings of Threat Extraction. It's a bit surprising that such a basic feature requires this license while AD Query should be sufficient.
Getting Started with the Threat Extraction Blade
n the Exclude/Include Users page, configure these settings:
- Scan all mail
Click Exceptions to not include specified users, groups, recipients or senders.
- Scan mail only for specific users or groups
Click Configure to select specified User Groups, Recipients or Senders.
Note:
A user is an object that can contain an email address with other details.
A group is an AD group or LDAP group of users
A recipient is an email address only.
Important: In Global Properties > User Directory, make sure that you have selected the Use User Directory for Security Gateways option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Timothy.
Only if I enable user management, I am able to see the select the domain when I enable Identity awareness. Do you know why? I got confused a bit.
Only if I enable user management, I am able to see the select the domain when I enable Identity awareness. Do you know why? I got confused a bit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes the "User Management" checkbox on the AU object itself must be set for IA to work, although this checkbox was mentioned in my post in the context of User Directory. What does not necessarily need to be set (subject to the conditions mentioned above) is the "Use UserDirectory for Security Gateways (license required)" checkbox in the Global Properties.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I have a question regarding User Directory and Identity Management. Can I use only User Active Directory on Management Server, without Identity Management on Gateways ?
I want to integrate a Checkpoint Infrastructure with 1 Mgmt and 2 GWs with AD, then to create some policies for remote VPN by using Groups of AD.
I know that using IA, you cannot retrieve info from AD Groups, you need UD to do this or Am I wrong ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can create Access Roles for Remote Access with more granularity using Identity Awareness, which can be restricted to Remote Access.
This would be the preferred approach versus using legacy groups/objects.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I am currently working on configuring Machine certificate. But I have a question. How can I integrate my FW with my Microsoft AD in order to find the users and computers that belong to said AD? I need to do this to be able to create the Access roles
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally! The answer I have been looking for;
>I have always been confused and conflicted with CP's documentation. CP's LDAP Best practice guide (under SK31841) recommends that it should be enabled, but as per our testing it just works even if disabled (and has been working for all of our clients deployed with CP's Firewall)
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 37 | |
| 29 | |
| 11 | |
| 10 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


