- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Register HereCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: URLs for Category Testing
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
URLs for Category Testing
Hi,
A customer would like to be able to test that a deployed URL Filtering policy is working correctly and blocking or allowing access to different groups of users.
Do Check Point provide a similar database of URLs to that seen at testwebsensedatabase.com (ForcePoint) so that specific categories can be confirmed to be blocked for certain users without having to try and visit a site that belongs to that category?
Clearly they don't want to be trying to go legitimate pornography sites or other questionable sites just to confirm the policy is correctly applied.
Thanks
23 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Paul,
I'm pretty sure that similar questions have been raised on Check Mates before and I don't believe that there is such a 'database' (not one that Check Point offers anyway). You can verify URL categorization as outlined on sk69200 but no, I don't think there is such a database.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this what you are looking for?
http://www.cpcheckme.com/checkme/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can see what category a particular URL will map via https://urlcat.checkpoint.com/
What the policy will be for a given user can't be seen here.
Interestingly, Google Chrome marks http://testdatabasewebsense.com/ as malicious.
Also, the background image for this site is being flagged by ThreatCloud as malicious.
As far as I know, we don't have our own such page, but I'll ask around.
What the policy will be for a given user can't be seen here.
Interestingly, Google Chrome marks http://testdatabasewebsense.com/ as malicious.
Also, the background image for this site is being flagged by ThreatCloud as malicious.
As far as I know, we don't have our own such page, but I'll ask around.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That might work for seeing if malicious content, but it doesn't check if my policy is blocking a specific content category for a specific user.
They aren't known "safe" URLs that trigger the various App Control/URL Filtering categories similar to the URLs we maintain for Threat Prevention blades.
They aren't known "safe" URLs that trigger the various App Control/URL Filtering categories similar to the URLs we maintain for Threat Prevention blades.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's interesting. Although it won't test URL Categories for me, it looks like a useful test for whether various blades are functioning.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes! Are you all green?
Regarding URL tests, I want to believe the names of the categories are self-explanatory and when you pick them, you already know in mind which specific sites you don't want to use. Can you give me an example of a category where you are not sure which examples are relevant?
Regarding URL tests, I want to believe the names of the categories are self-explanatory and when you pick them, you already know in mind which specific sites you don't want to use. Can you give me an example of a category where you are not sure which examples are relevant?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've not run the tool Tomer. I would need the customer to run it.
Well an example might be malicious sites. Customer wants to be sure they are blocked without visiting them. Even if they know a URL that is categorised as such, should they be testing to a 'genuine' malicious site to see if the policy works? If it's not configured properly and then they connect to the malicious site rather than being blocked they've now potentially infected or exposed themselves.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, any updates on this case? I am having the same issue, unable to test the configured policies with safe sites. I requested Check Point to categorize test pages from other parties accordingly to their categories (currently, they are all categorized as Computer/Internet), as recommended in sk98489, but they just dismissed my requests without any explanation... Please, if you know of any safe testing pages that Check Point has categorized correctly, could you share them with the community?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Last time I looked (which I admit was a while ago), each URL Filtering category should have a couple of example URLs.
We don’t have a central list, though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
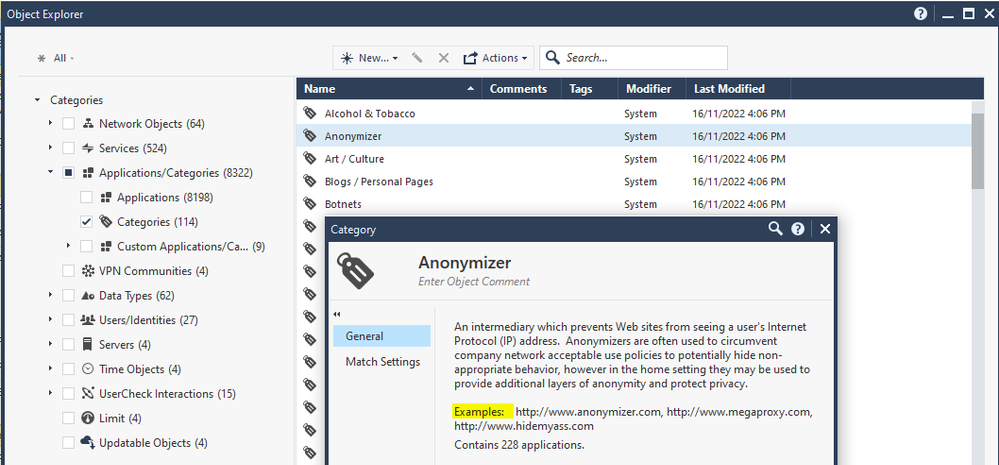
Indeed this is visible in SmartConsole / Object explorer as seen here:
See also: https://usercenter.checkpoint.com/ucapps/urlcat/categories
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your comments, guys. Yes, I am aware some examples are visible in SmartConsole, but let me explain why I think we need safe testing sites anyway:
1- For malicious or content-sensitive categories, we would prefer not to visit the actual web pages. For example, SmartConsole suggests xvideos.com for the Pornography category (do I really need to browse to an actual pornography site to check if my policy is correctly configured?), and no examples are provided for the Spyware / Malicious Sites category, at least in my SmartConsole version (so how do I check it?).
2- For non-malicious categories, some of the examples do not exist anymore (e.g., anonymizer.com), and most of them use only HTTPS currently, and we would like to check the policies before deploying HTTPS inspection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You don't need to browse to the sites you can test URLs here: https://urlcat.checkpoint.com/urlcat/
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am aware of it, but this is only helpful to see how Check Point categorizes an URL. We want to test if our configured policy is working as expected (so we need to surf to an actual page to check if the firewall is blocking that category).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HTTPS Categorization needs to be enabled (should be by default), but it should not be required to deploy HTTPS Inspection to categorize URLs in most cases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As you say, it is not required to categorize URLs, but it is to show the blocking page (otherwise, we only see a CONNECTION_RESET error message in the browser). Nonetheless, the issue with the need to surf to actual pornography pages to check the policy is still unresolved without safe testing pages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why do you believe that if you check the category of a URL on the URLCAT page and block this category in your policy that it wouldn't be effective?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are in an academic environment, students are learning, and they make mistakes. To verify their progress and continue to the next stages of the training, they need to check with us that their policies are correctly applied. As Check Point Academy instructors, we strongly believe that safe test pages are needed, and we do not want students to browse actual pornography or malicious sites to check their policies. I hope this is understandable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for clarifying the use case, it is different. Have you already raised this with the Secure Academy team as a requirement? If yes I will follow-up with them.
In the interim it sounds like something that may be overcome with a combination of DNS manipulation and a honeypot for such an environment (if not a basic category override).
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please provide further information on how to raise the case with the Secure Academy team? Thank you for your kind answers throughout the process.
The workaround we've been doing is to configure a category override for the safe testing sites, but if Check Point did it permanently on its database, it would be ideal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would start by reaching out to secureacademy(at)checkpoint.com and go from there.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any Idea where I can get the list of URLs that the IPS is blocking ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This would be VERY useful as well!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 15 | |
| 9 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter