- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Boosting Performance & Stability
with Harmony Endpoint E88.70!
Four Ways to SASE
April 23, 5PM CET | 11AM ET
It's Here!
CPX 2025 Content
Zero Trust: Remote Access and Posture
Help us with the Short-Term Roadmap
The Future of Browser Security:
AI, Data Leaks & How to Stay Protected!
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: Two ISP's with two appliances 4800 R80.10
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Two ISP's with two appliances 4800 R80.10
Hello guys,
My scenario is as follows: I have two 4800 appliances and now two different ISPs. Each ISP connects to only 1 gateway. Can I work with both in active / standby? Remembering that each ISP connects to 1 gateway and not both. Does ISP redundancy do this? I would like to leave a working ISP and if it goes offline, the backup goes online. My biggest doubt is that if the main ISP that is in the active gateway falls, there will be a connection to the other ISP in the Firewall standby.
My solution:
- 2 Checkpoint 4800 appliance;
- R80.10 version firewall and managment;
Thanks.
- Tags:
- 4800
- isp
- redundancy
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This exact question came up here: https://community.checkpoint.com/thread/10663-checkpoint-cluster-failover-query
TL;DR: It doesn't work that way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Easy - use HA Cluster and ISP redundancy !
- if the active cluster node fails, standby will take over, keeping the primary ISP
- if primary ISP fails, secondary will take over
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Will the ISP redundancy work with the schema that each ISP is physically connected on only 1 appliance?
The scenario is:
Firewall 1 -> ISP 1
Firewall 2 -> ISP 2
Only 1 port per ISP on 1 firewall and not both ISPs are on both appliances.
If the active firewall 1 fails, which has ISP 1 connected, will traffic be thrown to Firewall 2, which does not have ISP 1 connected?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, this is not a supported configuration.
Please refer to the thread I linked previously, which discusses this exact issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's what I thought. I have to physically connect the two ISPs on both appliances for redundancy.
Thanks everyone.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are the firewalls in the same location? We connect our ISP's to a switch then you can connect those WAN VLAN's to both the firewall appliances. If your ISP's both only give you one IP you can still use those just as the VIP's then use a different addressing scheme for the physical IP's.
So you can have ISP1 > Switch on vlan 1 > both checkpoints on VLAN 1 and setup physical IP's and a VIP for this vlan then do the same with a different VLAN/IP's for the other ISP connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Aidan,
The topology will look like this: ISP 1, located on DC1, connected to a core switch in VLAN X which in turn will connect to port X of FW1. ISP 2, located on DC2, connected to a core switch on the VLAN Y which in turn will connect to the FW2's X port. These switches are stacked, that is, they are part of the same "unit". In this way, what is the best approach for both ISPs to be connected, whether redundant or active?
Firewalls in active/standby mode or active/active ?
And about configuration of rules, NATs, static routes ?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is an unsupported configuration and ClusterXL will not work. Please explain why you can not use a standard ClusterXL ISP Redundany / LS configuration!
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I explained above, can I use ISP Redundancy? Isps arrive on each side, connected to VLANs -> FW?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ISP Redundancy requires both ISPs to be reachable from both gateways.
If that is not the case with your configuration, it will not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even every ISP having reach to the other side via switch / vlan? The core stack is interconnected between the DCs via fiber channel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the switch/VLAN configuration allow both gateways to reach both ISPs, then yes.
A proposed network diagram would be helpful to confirm.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
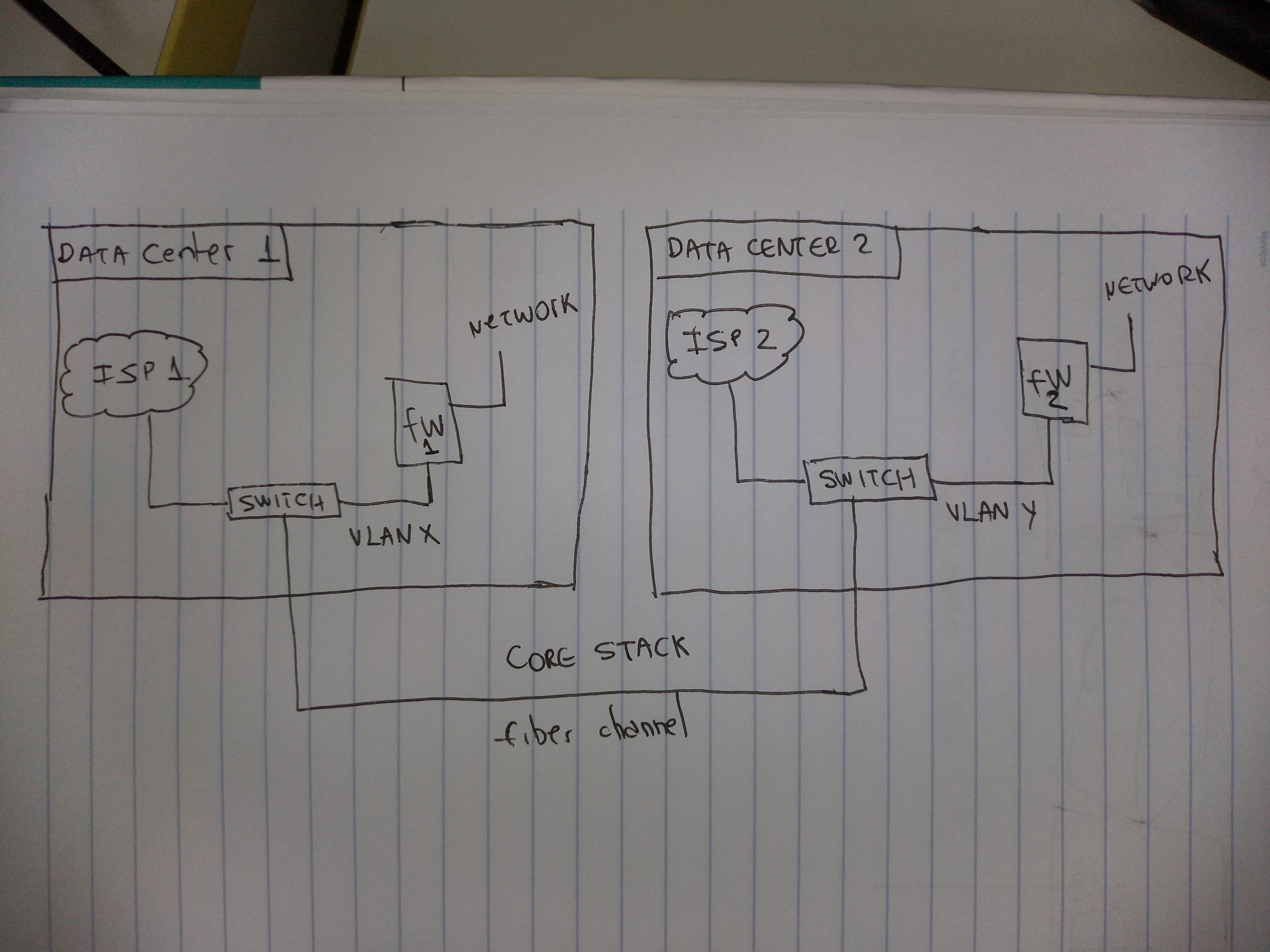
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks as if that should work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Be careful when you are thinking what you define as ISP being "offline".
It is either problem on physical layer (port goes down for whatever reason) or on protocol layer (default gateway or any other along the path fails). First one it is in fact the best to happen. Second one will require that you monitor certain hosts on the Internet and initiate fail-over should certain criteria is satisfied.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 11 | |
| 8 | |
| 6 | |
| 6 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Wed 02 Apr 2025 @ 03:00 PM (CEST)
The Power of SASE: Smarter Security, Stronger Network - EMEAWed 02 Apr 2025 @ 02:00 PM (EDT)
The Power of SASE: Smarter Security, Stronger Network - AmericasThu 03 Apr 2025 @ 01:00 PM (CEST)
Meet the Experts: Transforming Security Operations with Impactful Intelligence!Wed 02 Apr 2025 @ 03:00 PM (CEST)
The Power of SASE: Smarter Security, Stronger Network - EMEAWed 02 Apr 2025 @ 02:00 PM (EDT)
The Power of SASE: Smarter Security, Stronger Network - AmericasThu 03 Apr 2025 @ 01:00 PM (CEST)
Meet the Experts: Transforming Security Operations with Impactful Intelligence!Wed 09 Apr 2025 @ 05:00 PM (CDT)
Unleashing Performance & Stability with Harmony Endpoint E88.70Thu 10 Apr 2025 @ 10:00 AM (EEST)
CheckMates Live Sofia - Maintenance and Upgrade Best PracticesTue 06 May 2025 @ 09:00 AM (EEST)
CheckMates Live Cyprus - Performance Optimization Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


