- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Supports HTTPS Inspection and Domain object.
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Supports HTTPS Inspection and Domain object.
Hello.
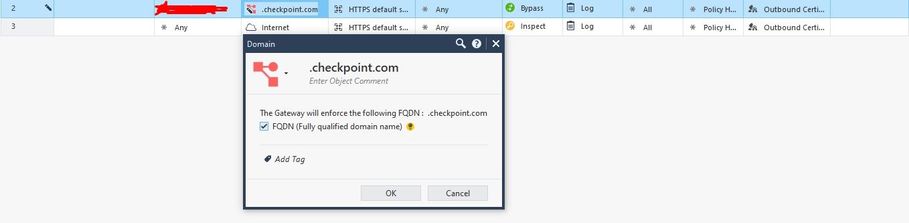
I am testing HTTPS Inspection work with Domain Object work. I created a test rule for .checkpoint.com and set the Action to Bypass.
But I found that the ssl certificate is spoofed for all Check Point resources except for the checkpoint.com home page. For example, for usercenter.checkpoint.com, the certificate is swapped for the certificate we import in the Security Gateway settings.
Can you please help me how I can put domain objects in bypass mode. And is this functionality supported by Check Point?
Check Point version R81.10
Output: enhanced_ssl_inspection = 1
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For FQDN, this is a full name, not a wildcard for multiple subdomains. Create another Domain object fro usercenter.checkpoint.com, and also for www.checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do we inspect the entire .checkpoint.com domain?
If we remove the flag on the FQDN, are all sites (usercenter.checkpoint.com, help.checkpoint.com) inspected except checkpoint.com?
Or does CheckPoint not provide for bypass of the entire domain and you have to create a domain group and explicitly specify the nodes that are not inspected there?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
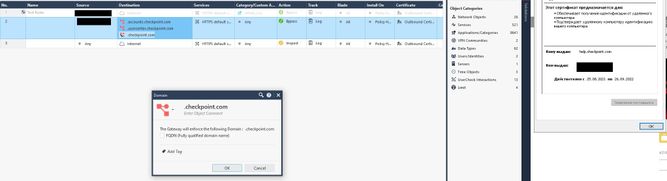
For example, I added two more objects -- .accounts.checkpoint.com and .usercenter.checkpoint.com and they have the FQDN flag enabled. They stopped being inspected.
For .checkpoint.com I turned off the FQDN, so I assumed that checkpoint treated it as a domain and hel.checkpoint.com would not be inspected, but I found that the certificate for hel.checkpoint.com was also spoofed. Could you help us solve this problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Never ever remove FQDN mark, it will kill performance on your FW. Basically you need to list all sites. There is a finite number of those 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_ I totally agree to the "never ever remove FQDN mark", because of CP is falling back to do reverse DNS lookup again (in some topologies, passive DNS learning may help).
But I always wondered what CP gateway does when trying to match an updateable object with wildcard domains in it. Do you know it?
Here is an example from updateable object "Webex Services":
# domains_tool -uo "Webex Services"
Domain tool looking for domains for 'Webex Services' and its children objects:
Domains name list for 'Webex Services':
[1] *.cisco.com
[2] cme-linuscmesquaredafram-035-afram-admin.wbx2.com
[3] cme-linuscmewdfw2wdfw2-027-wdfw2-public.wbx2.com
[4] mln1mcccl01.webex.com
[5] bottomlinetechnologies.webex.com
[6] *.walkme.com
[7] cme-linuscmewdfw2wdfw2-481-wdfw2-public.wbx2.com
[8] 0a4f0f5de2ab23da1a6b-0ebfd742e5f97efaf8e29d5671af2106.r94.cf1.rackcdn.com
[9] *.webex.com
[10] temas.s3.amazonaws.com
...
If it does fall back to old reverse DNS lookup, customers will get the performance penalty for that without even knowing it (because they may not think about how these objects work).
If it just ignores these entries, I guess it does not work as expected.
I really must have something missing here in my head. Anyone can help me out?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great Question @Tobias_Moritz! I've had the same thoughts concerning Updateable Objects and how Checkpoint would handle the wildcard domains in those objects. Looking forward to a response from Checkpoint folks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Look one comment above 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Updatable objects are pre-populated on GWs by different means (either CP own list or vendor list of IPs is used for various cases), but they are not using reverse DNS lookup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much for this relieving answer, Val. 🙂
Is it too greedy to ask if you can eleborate further? Is there any way we can see the actual list on gateway which is used for matching of updatable objects (as it cannot be the list of domains_tool -uo because of your answer)?
I love transparency because this can be very helpful during debugging sessions. And usually, Check Point is very transparent in how they implement stuff, so that guys like Tim or Heiko e.g. can write nice guides around it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mostly, we rely on distribution lists provided by relevant vendors. Those lists and URLs for them are listed in sk131852. For Webex specifically, the list is published and updated on the daily basis. It consists of IP ranges and associated domain names.
GWs do not get those lists directly from Webex, though. All UO are populated though Check Point own cloud services: updates.checkpoint.com and dl3.checkpoint.com.
In case of FQDN domain objects, GW resolves those in advance with the help of WSDNSD.
To check IPs and domain names, you can use domains_tool -ip <ip address> & domains_tool -d <domain name> commands.
Bottom line, there is no reverse DNS lookup for either FQDN domain objects or Updatable objects, ever.
There is no magic, just tech 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, other than main "static" check point sites, you can also use updatable objects (sk131852) for all Check Point cloud entities listed in sk83520
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 21 | |
| 17 | |
| 14 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter