- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Stealth Rule best practices
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Stealth Rule best practices
Have a question: In the guide 'Creating a basic access control policy,' it is recommended to create a Stealth Rule which restricts management access to the firewall gateways themselves. I believe most, if not all, customers of Check Point thusly have some version of this rule in their policy. But it seems like there are many different ways to go about actually writing the rule.
From the guide, the two basic rules they suggest:
1. Source: Admins (Access Role); Destination: Group of Security Gateways; Services: Any; Accept
2. Source: Any; Destination: Group of Security Gateways; Services: Any; Drop
But when researching this topic, searching these forums, etc, I am seeing several different way that customers have set these rules up, in regards to what object they are using in the 'Destination' column. Some different designs I've seen talked about:
- Reference the actual Cluster Object and/or Gateway Objects in the rule
- Creating Host Objects representing the IP Addresses of the Gateway Interfaces
- Using Dynamic Objects i.e. LocalGatewayExternal, LocalMachine, LocalMachine_All_Interfaces, etc.
In addition to that, in Gateways & Servers under Cluster Properties there is 'Platform Portal Accessibility' feature which can be toggled to 'Through all interfaces," "Through internal interfaces," or "According to the Firewall policy."
I know the answer is usually "it depends on what your intention is," but it's not exactly clear how these different options affect how matching works, i.e. does using the Cluster Object match on any IP Address of the cluster interfaces, or does it only match on the management address? Are the Dynamic objects like LocalGatewayExternal better? Stealth rule applies only if you have "According to the Firewall Policy" toggled for Platform Portal?
I am just wondering, if you are ATAM and setting up a brand new gateway for a brand new customer, policy being built totally from scratch, how are you building the Stealth Rules? is the best practice differ between R81.10/20, R82, etc. Thanks for any discussions you can bring!
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Cypress
What was the sk what you read?
Here are two:
https://support.checkpoint.com/results/sk/sk106597
https://support.checkpoint.com/results/sk/sk102812
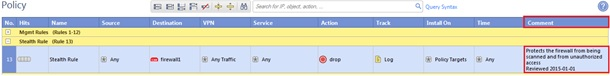
- The Stealth rule should be located as early as possible in the policy, typically placed immediately after the management rules.
The purpose of the Stealth rule is to drop unauthorized connections destined to the firewall; protecting the firewall from being scanned and attacked.
The rulebase is likely to be constantly evolving so the effectiveness of the Stealth rule should be periodically tested; it may need to be re-positioned to maintain effectiveness.
Akos
----------------
\m/_(>_<)_\m/
\m/_(>_<)_\m/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Both great references @AkosBakos
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One thing to be careful of regarding the use of Dynamic Objects (eg LocalMachine) is they require an explicit “Install-On” field (ie cannot be Any).
It’s not something I see for a stealth rule, usually.
The stealth rule is also complicated by how the Implied Rules work, particularly for http/https to the gateway itself.
This will likely help that: https://support.checkpoint.com/results/sk/sk180808
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy this kind of Dynamic Objects (eg LocalMachine) not related to only SMB appliances?
----------------
\m/_(>_<)_\m/
\m/_(>_<)_\m/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dynamic_objects -l from expert on my locally managed SMB appliance includes LocalGateway plus several others.
I've also used them in centrally managed policies previously.
There is just no mechanism in local management to create/refer to these objects beyond the objects that already exist (e.g. "This Gateway").
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would say this is PERFECT explanation...courtesy of AI copilot 🙂
Andy
**********************************
This is Check Point AI Assistant.
Configuring a stealth rule is a best practice to prevent direct access to the Security Gateway. Here are the steps to configure a stealth rule in Check Point:
Steps to Configure a Stealth Rule
-
Open SmartConsole:
- Launch the SmartConsole application and log in with your administrator credentials.
-
Navigate to the Security Policies:
- Go to the "Security Policies" tab.
-
Create a New Rule:
- Click on the "+" button to add a new rule at the top of the rule base.
-
Define the Rule Properties:
- Name: Give the rule a meaningful name, such as "Stealth Rule".
- Source: Set the source to "Any" or specify the networks that should be restricted.
- Destination: Set the destination to the group of Security Gateways.
- Services & Applications: Set this to "Any".
- Action: Set the action to "Drop".
- Track: Set the tracking option to "Alert" to receive notifications when this rule is matched.
-
Position the Rule:
- Ensure that the stealth rule is placed at the top of the rule base, just below any necessary administrative access rules.
-
Install the Policy:
- After configuring the rule, click on "Install Policy" to apply the changes to the Security Gateways.
Example of a Stealth Rule Configuration
| No | Name | Source | Destination | Services & Applications | Action | Track | Install On |
|---|---|---|---|---|---|---|---|
| 1 | Stealth Rule | Any | Group of Gateways | Any | Drop | Alert | Policy Targets |
Best Practices
- Admin Access Rule: Ensure you have an admin access rule above the stealth rule to allow administrators to connect to the Security Gateways.
- Cleanup Rule: Place a cleanup rule at the bottom of the rule base to drop all traffic that is not explicitly allowed by earlier rules.
By following these steps, you can effectively configure a stealth rule to enhance the security of your Check Point environment.
Learn more:
- R81 Quantum Security Management Administration Guide - Creating-a-Basic-Access-Control-Policy
- R80.40 Security Management Administration Guide - Creating-a-Basic-Access-Control-Policy
- R82 Security Management Administration Guide - Best-Practices-for-Access-Control-Rules
- R80.40 Security Management Administration Guide - Best-Practices-for-Access-Control-Rules
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To further expand upon what "Admin Access" rules need to be placed in front of the Stealth Rule, there are generally 4 categories of these rules:
1) General Admin Access - SSH, HTTPS, 4434 access to Gaia OS from a trusted IP/network
2) Ping/traceroute - Do you want the gateway to respond to ping requests to its own interfaces and also show up in traceroute? Generally if the request is coming from the inside or DMZ I'd say allow this. Coming from the Internet or other untrusted networks? Nope.
3) NMS SNMP - If you have some kind of network monitoring system doing SNMP GETs to the firewall for pulling statistics, you'll need a rule allowing this. Netflow statistics are connections initiated by the gateway to the collector, so no need for explicit rules allowing Netflow usually.
4) DHCP - If the firewall's Gaia OS is acting as a DHCP Server (not likely) or performing DHCP Relay/Helper (more likely), the DHCP broadcasts will need to be allowed.
There are a few other random corner cases involving legacy identity/authentication features and such, but these 4 categories should about cover it.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 17 | |
| 8 | |
| 8 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter