- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- R81.20 jumbo 79
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.20 jumbo 79
Hey guys,
Just wanted to say I installed jumbo 79 in the lab, so far so good, I see lots of improvements from the documentation.
Andy
https://sc1.checkpoint.com/documents/Jumbo_HFA/R81.20/R81.20/Take_79.htm?tocpath=_____6
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @the_rock
I would like to ask one question:
Among your productive installations, is there any FWK issues? Randomly stops, etc? I have some in my, thats why I am asking you about this, because take 79 has a lot of FWK fixes.
Have you any expereience in this?
Akos
----------------
\m/_(>_<)_\m/
\m/_(>_<)_\m/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ask any questions mate, no worries. No issues I had observed so far. If anything, I will definitely update.
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @the_rock , urgent help need,
We have firewall in Datacenter and SMB 1500 device in remote site, both are connected via S2S VPN tunnel, I did upgrade the Datacenter firewall from R81.10 to R81.20 Take 76 on Aug 6th. All of sudden on Aug 16th , VPN is up on remote site, but not able to reach the internal IPs. When i check the routes on Datacenter firewall, I don't see the routes for the remote sites.
Basically, RIM is not working, It is not inserting the routes on to the DC routing table. VPN is up on both ends, but i suspects there is some issue on VPN that's the reason routes are not learning on DC firewall. can you advise on this, any bug on R81.20 Take 76?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mate, if its urgent, I would pick up the phone, call TAC and ask for remote session.
No, Im not aware myself of any issue like one you described. I would run basic vpn debug, maybe examine messages files, as well as routed.log
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @the_rock , urgent help need,
We have firewall in Datacenter and SMB 1500 device in remote site, both are connected via S2S VPN tunnel, I did upgrade the Datacenter firewall from R81.10 to R81.20 Take 76 on Aug 6th. All of sudden on Aug 16th , VPN is up on remote site, but not able to reach the internal IPs. When i check the routes on Datacenter firewall, I don't see the routes for the remote sites.
Basically, RIM is not working, It is not inserting the routes on to the DC routing table. VPN is up on both ends, but i suspects there is some issue on VPN that's the reason routes are not learning on DC firewall.
can you advise on this, any bug on R81.20 Take 76?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you using Domain-based VPN or route-based?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@paulraj29 You posted exact same thing mate...did you read my response, not only here, but also to the other post?
Happy to do remote if you want to check further.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Found an issue.
After upgrading the SMS we where no longer able to login to SmartConsole. The following message appeared as the symptom.
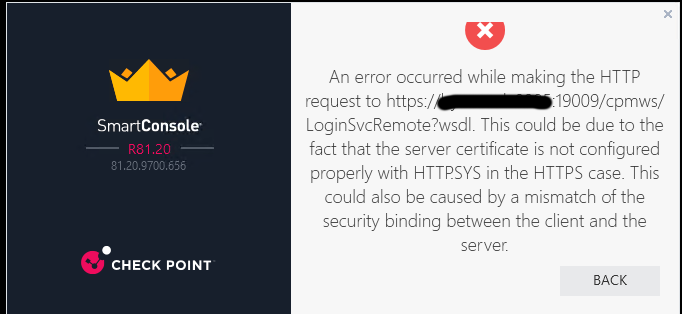
After investigation found SK169253 which basically tells us that the host machine running smartconsole does not support TLS cipher DHE_RSA_WITH_AES_128_GCM_SHA256.
I verified this by running the following from powershell prompt:
Get-TlsCipherSuite TLS_ECDHE_RSA_WITH_AES_128 | Format-Table -Property Name
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256
As you can see above the required cipher is not listed.
So you would need to add this to the host machine (using SK instructions or via group policies)
Question is why is this now a restriction and where is it documented in the Jumbo list?
In the meantime we have reverted back to JHFA70 which works fine.
People just be aware of this requirement when applying JHFA79 as it may not show up in a LAB, but in a production environment the system hosting smartconsole is likely to be hardened, and therefore you may come across this.
Also the other observation is TLSv1.2 requirement, but implies no TLSv1.3 support so if you only enabled TLSv1.3 on the SMS perhaps this would also break things.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tx for that @genisis__
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This could be the following from the release notes.
|
PRJ-50381, |
Security Management |
UPDATE: Various Web Portals on the Security Management Server (for example, Web SmartConsole, SmartView) no longer accept HTTPS connections to ports 443 and 19009 with specific TLS 1.2 ciphers. Refer to sk181879. |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks, at least there is something noted, what the SK does not indicate is the list of supported ciphers from JHFA79, or is it just that single cipher using TLSv1.2?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 39 | |
| 12 | |
| 9 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Tue 04 Mar 2025 @ 04:00 PM (CET)
Check Point | WIZ : Powering the Next Era of Cloud Security - AMERICASTue 11 Mar 2025 @ 05:00 PM (CDT)
Under the Hood: Configuring Site to Site VPN with Azure Virtual WAN and CloudGuard Network SecurityWed 12 Mar 2025 @ 06:00 PM (IST)
TechTalk: The Future of Browser Security: AI, Data Leaks & How to Stay ProtectedTue 04 Mar 2025 @ 04:00 PM (CET)
Check Point | WIZ : Powering the Next Era of Cloud Security - AMERICASTue 11 Mar 2025 @ 05:00 PM (CDT)
Under the Hood: Configuring Site to Site VPN with Azure Virtual WAN and CloudGuard Network SecurityAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


